 The ransomware strain was discovered in a private peer-to-peer (p2p) network and targets consumers by using the icon of a game or application to trick the user into downloading it.
The ransomware strain was discovered in a private peer-to-peer (p2p) network and targets consumers by using the icon of a game or application to trick the user into downloading it.
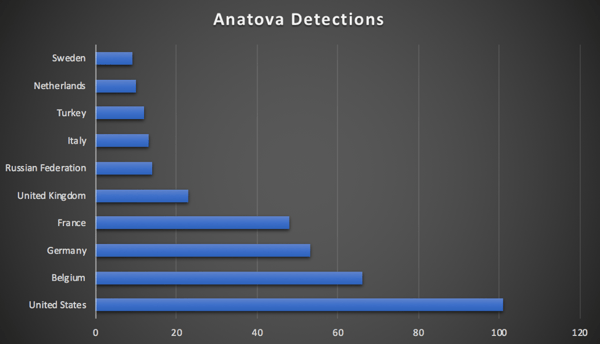
McAfee researchers today announced the discovery of a new ransomware family, “Anatova” that is targeting consumers at scale across the globe. The ransomware was discovered in a private peer-to-peer (p2p) network and targets consumers by using the icon of a game or application to trick the user into downloading it.
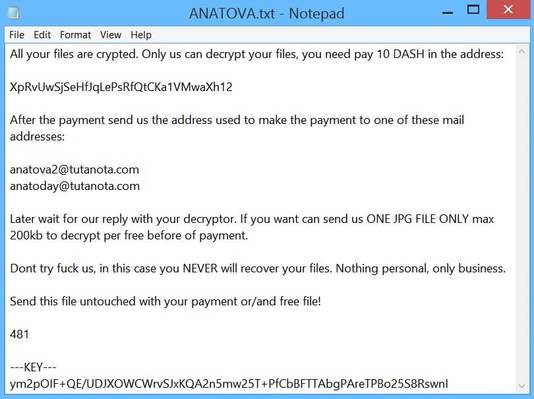
Christiaan Beek, Lead Scientist & Principle Engineer at McAfee said, “Creating a quick and fast piece of ransomware is fairly easy for those with basic know-how. Ransomware packed with functionality that is also difficult to analyze, such as Anatova, is more difficult to create from scratch. Anatova has the potential to become very dangerous with its modular architecture which means that new functionalities can easily be added. The malware is written by experienced authors that have embedded enough functionalities to be sure that typical methods to overcome ransomware will be ineffective, for instance data can’t be restored without payment and a generic decryption-tool cannot be created.” This is a screenshot example
Here are the highlights:
- Brand-new code shows the actors behind this ransomware family aren’t your average hackers, but experienced bad actors
- Shown the ability to morph quickly, adding new evasion tactics and spreading mechanisms
- Includes functions which are not often see in ransomware families. In the same vein however, where there are observed similarities, the functions are the same as those used by the most destructive ransomware families such as GandCrab
- Once downloaded, the malware quickly encrypts all or many files on an infected system and demands ransom in cryptocurrency in order to unlock it - 10 DASH – currently valued at around $700 USD
McAfee’s researchers reported this new ransomware could become a serious threat since the code is prepared for modular extension - this means that new functionalities can easily be added.
The malware is written by skilled authors that have embedded enough functionalities to be sure that typical methods to overcome ransomware will be ineffective, for instance data can’t be restored without payment and a generic decryption-tool cannot be created.
You simply have to step your users through new-school security awareness training to inoculate them against attacks like this. Keeping families safe at the house is just as important, so here is a free Children's Interactive Cybersecurity Activity Kit.
Free Ransomware Simulator Tool
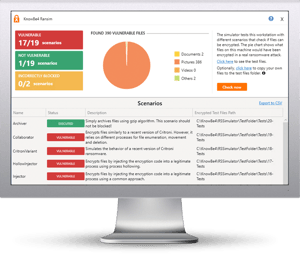 How vulnerable is your network against a ransomware attack?
How vulnerable is your network against a ransomware attack?
Bad guys are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.





