The 360 security blog just came up with an eye opener. Recently, 360 Security Center’s threat monitoring platform has detected a new email phishing attack. This attack uses a secret-stealing Trojan called Poulight. The Poulight Trojan has been put into use since last year and has complete and powerful functions. This attack proved that it has begun to spread.
Attack process analysis
The attacker will first drop a phishing file using RLO (Right-to-Left Override) technology. Using RLO technology, the phishing file originally named “ReadMe_txt.lnk.lnk” will be displayed as “ReadMe_knl.txt” on the user’s computer. . At the same time, if the attacker sets the icon of the lnk file as a notepad icon, it is easy for the user to mistake it for a harmless txt file.
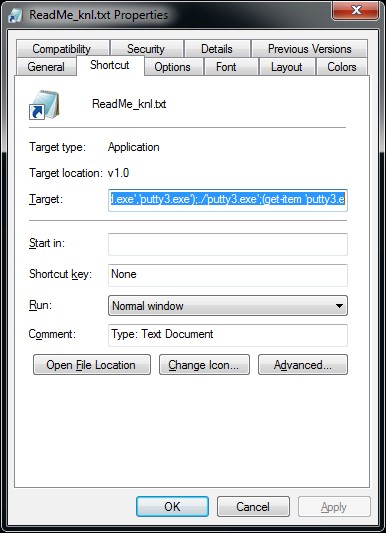
In this way, the user originally thought to open a txt file, but actually executed the code prepared by the attacker. The system will execute the powershell command according to the content of the “target” customized by the attacker, download the malicious program https[:]//iwillcreatemedia[.]com/build.exe, set it as a hidden attribute, and run it. After analysis, the downloaded malicious program was compiled with .net and the internal name is Poullight.exe. Full attack and code analysis at the 360totalsecurity blog.
https://blog.360totalsecurity.com/en/a-txt-file-can-steal-all-your-secrets/
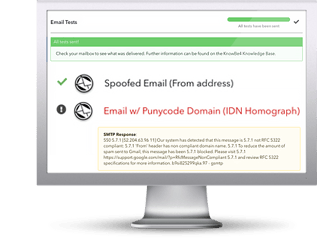 Here's how MSA works:
Here's how MSA works:




