By Eric Howes, KnowBe4 Principal Lab Researcher. Over the last few months, we have seen a rising trend of the bad guys using legitimate services—mainly file hosting platforms, but also free survey services—to slip by anti-virus software and Exchange security services. Legitimate file hosting and survey services allow the bad guys not only to host their malicious content for but even use those services to push out phishing emails to potential victims. This type of cleverly staged phishing attack can be particularly hard to spot by end users but there are some giveaways.
Our labs are seeing an increase in phishing emails pushing links to malicious files hosted on the compromised accounts of known external contacts -- users who likely familiar to your employees but who who have had their inboxes as well as their accounts at popular online services compromised. Given that the links in these phishing emails are pointing to legitimate, trusted online platforms and services like Microsoft, Google, Box.com, Dropbox, and SurveyMonkey (among others), unwitting employees could very well assume such links are completely safe. But in clicking through these links your users could find themselves in for a nasty surprise.
Two Great Flavors, Same Bad Taste
We have observed two distinct varieties of these apparently innocuous but highly malicious emails. Both are dangerous. Both can result in your users coughing up their credentials or downloading and executing malware on their PCs. One, however, is a bit trickier than the other.
In the first variety malicious actors host malicious content on a legitimate online service or platform, then push links to that content through phishing emails of their own creation -- often spoofing the very online services they are exploiting. Even though the email itself may be spoofed, the link provided in the email body points to a legitimate, trusted service or web site.
One common example we see on a a daily basis spoofs Microsoft and invites users to click through to malicious content hosted on Microsoft's Forms site.
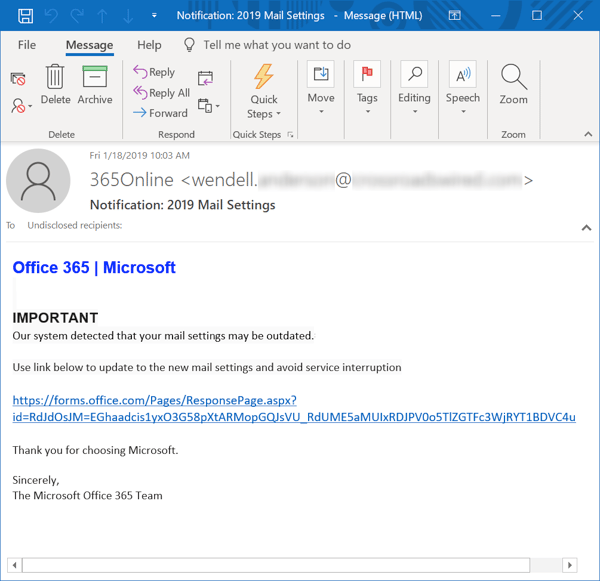
There is no attachment here, just a link to what appears to be an innocent file. The email itself appears legit and often does not get blocked by security software, given that the link points to a trusted web site where a slickly designed form typically points users to yet another external site hosting a malware download or a convincing credentials phish.
Occasionally the bad guys will even spoof an attachment by employing a cleverly placed fake download graphic in the email body:
![]()
When users hover their mouse over that graphic they are shown a link that appears to be safe because it points to Microsoft.
For the bad guys, this kind of attack is a no brainer. When one of our customers reported this Microsoft Forms phish to Microsoft, the company confirmed that anyone can create a free Microsoft Live account and create malicious forms that are conveniently hidden behind a URL pointing to Microsoft itself.
Microsoft isn't alone in seeing its free forms service abused and exploited by malicious actors, though. The bad guys are perfectly happy to abuse Google forms in a similar fashion:
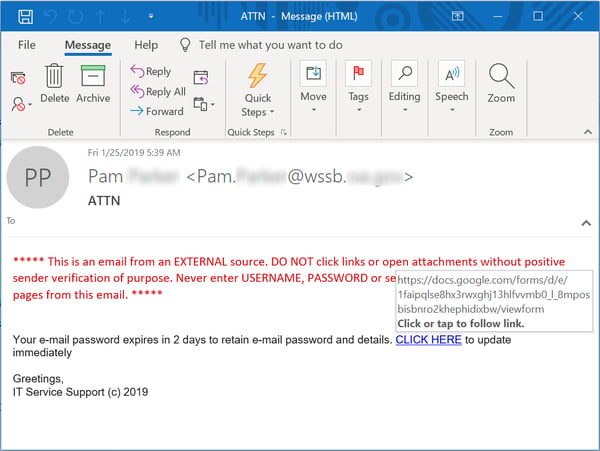
Although this email isn't quite as slick as the previous one (which neatly spoofs an Office 365 email with a link directing users to Microsoft itself), users who click through this Google link will be taken to malicious form nicely branded by Google itself.
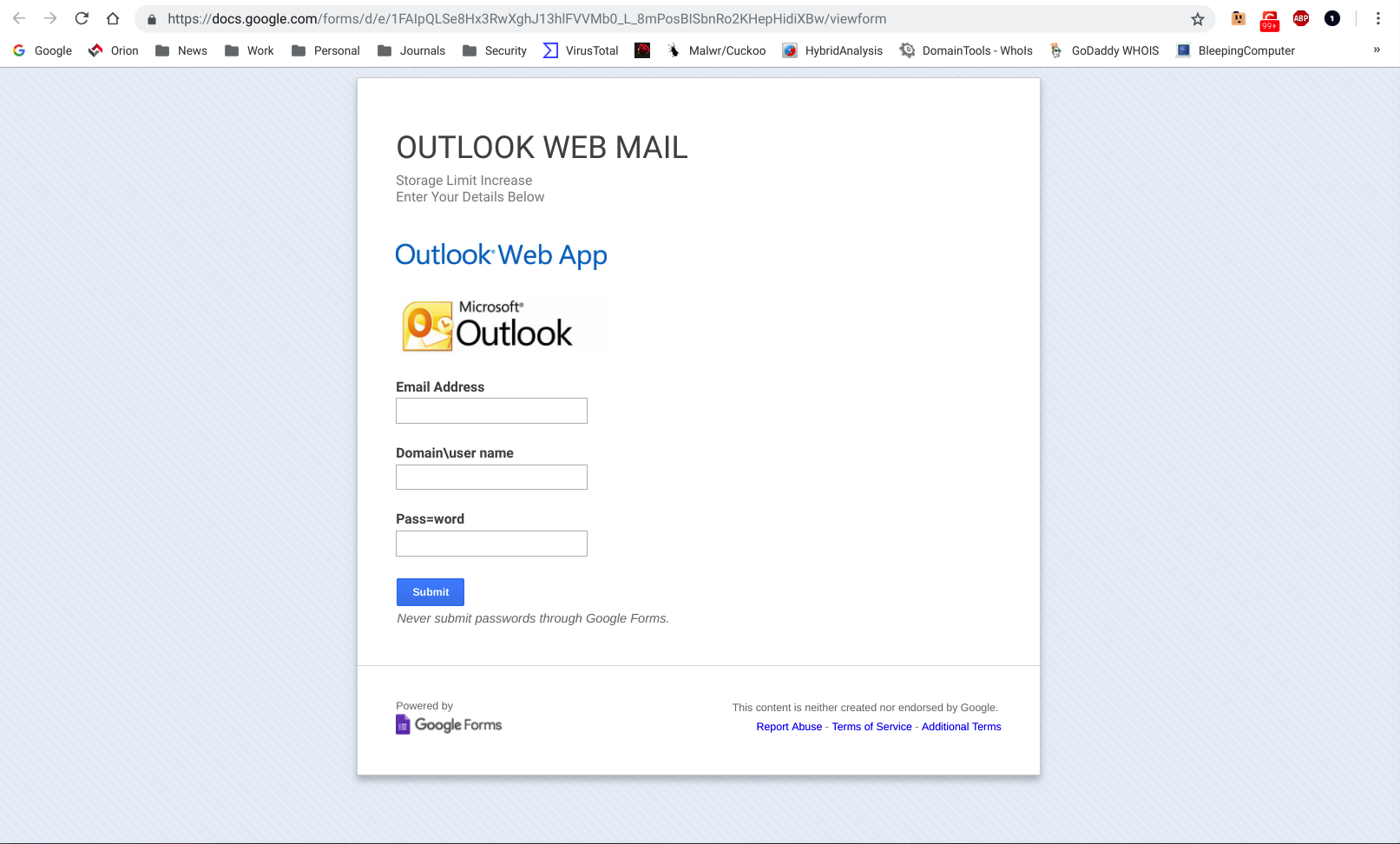
In the second variety of phish that we've observed over the past few months the bad guys dispense with the spoofed email entirely, relying instead on the exploited service itself to deliver their highly malicious but apparently innocuous links to potential marks.
One of the services most frequently abused in this manner is Dropbox, which is used by bad actors not only to host their malicious content but to push out emails offering up that content to potential victims.
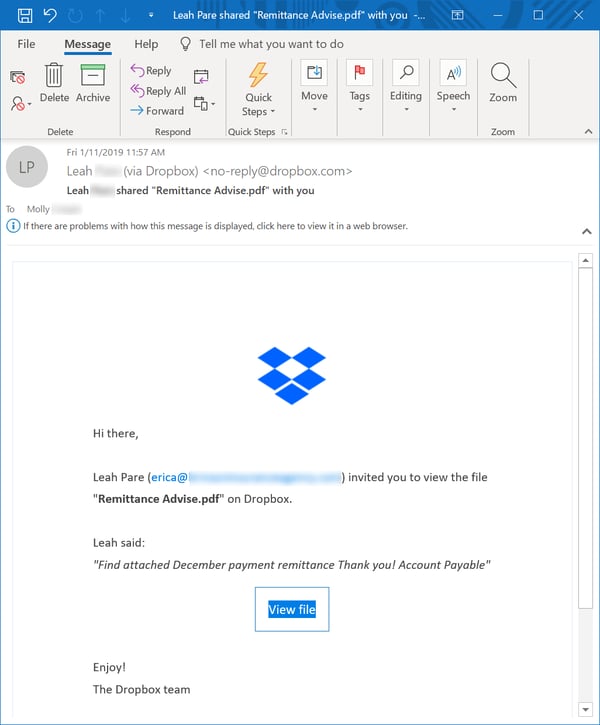
These emails, like the links they contain, will likely strike most users as completely innocent given that they are hailing from Dropbox itself. Indeed, the ruse can be so convincing that even users who run into difficulty after arriving at the landing page for the malicious file continue to press the malicious actors for access to what they believe is a legitimate, safe file.
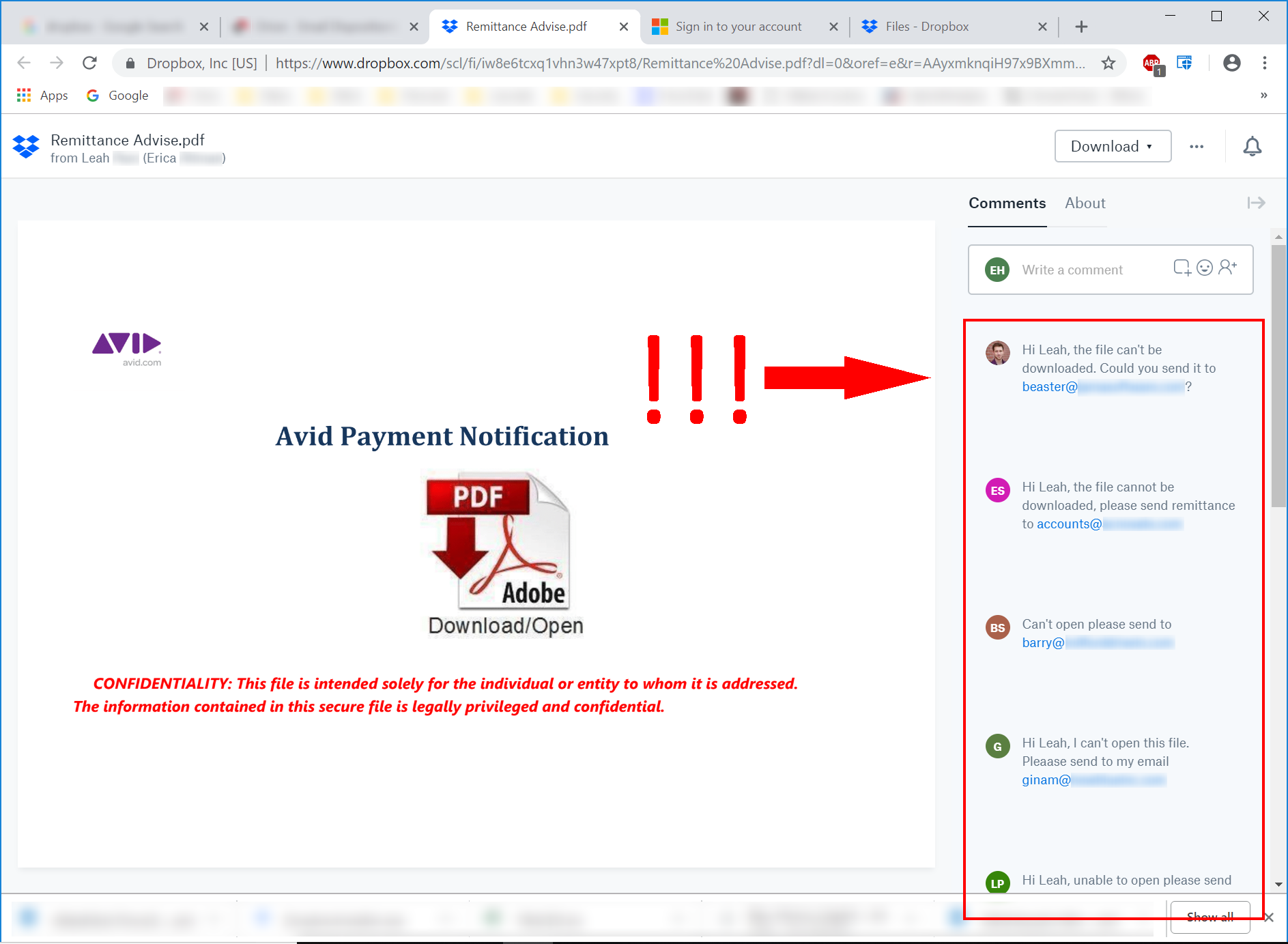
The Giveaways
As sneaky as these phishes are, there are almost always "tells" that should alert wary, properly trained users that something is amiss.
With the first email we documented above, the first giveaway is the forms.office.com domain in the URL. In fact, there is no reason for allegedly legitimate content of the kind advertised in the email body to be hosted on a forms site. And in cases where the bad guys couple the link with a fake attachment graphic, the fake attachment is itself yet another giveaway -- links for real email attachments don't point to external web sites.
The Google Forms phish is plagued by its own share of problems. Skeptical users really ought to be raising an eyebrow at the curious appearance of a Microsoft Outlook password reset form being hosted on a Google Forms web site. All too many users, unfortunately, are on auto-pilot in situations like this -- ignoring obvious clues as they blithely hand over their login credentials to malicious actors.
In fact, the bad guys are all too often careless in their rush to exploit trusted brands. Users who have been stepped through New-school Security Awareness Training should be brought up short by the link in this spoofed DHL email:
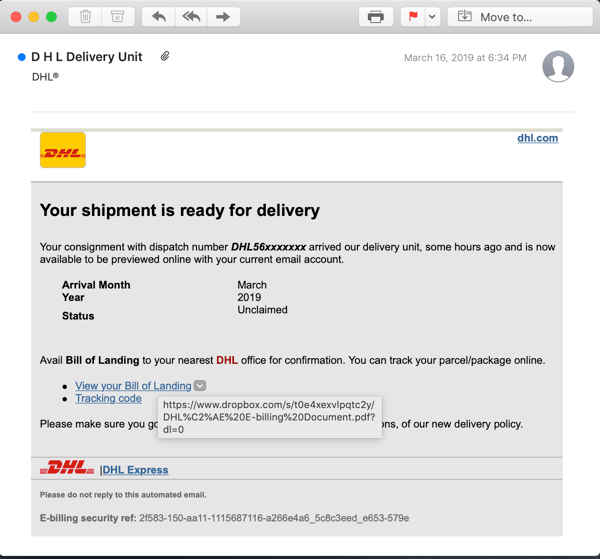
Dropbox is generally regarded as a trusted service, but what is a link to Dropbox doing in the middle of an email purportedly from DHL?
Even a phishing attack that leads off with an email delivered through Dropbox itself usually ends up throwing off plenty of clues that something nefarious is afoot. Users who attempt to download or view that "Payment Notification" PDF hosted on Dropbox itself are inexplicably kicked to a spoofed Microsoft login page hosted on a .TK domain:
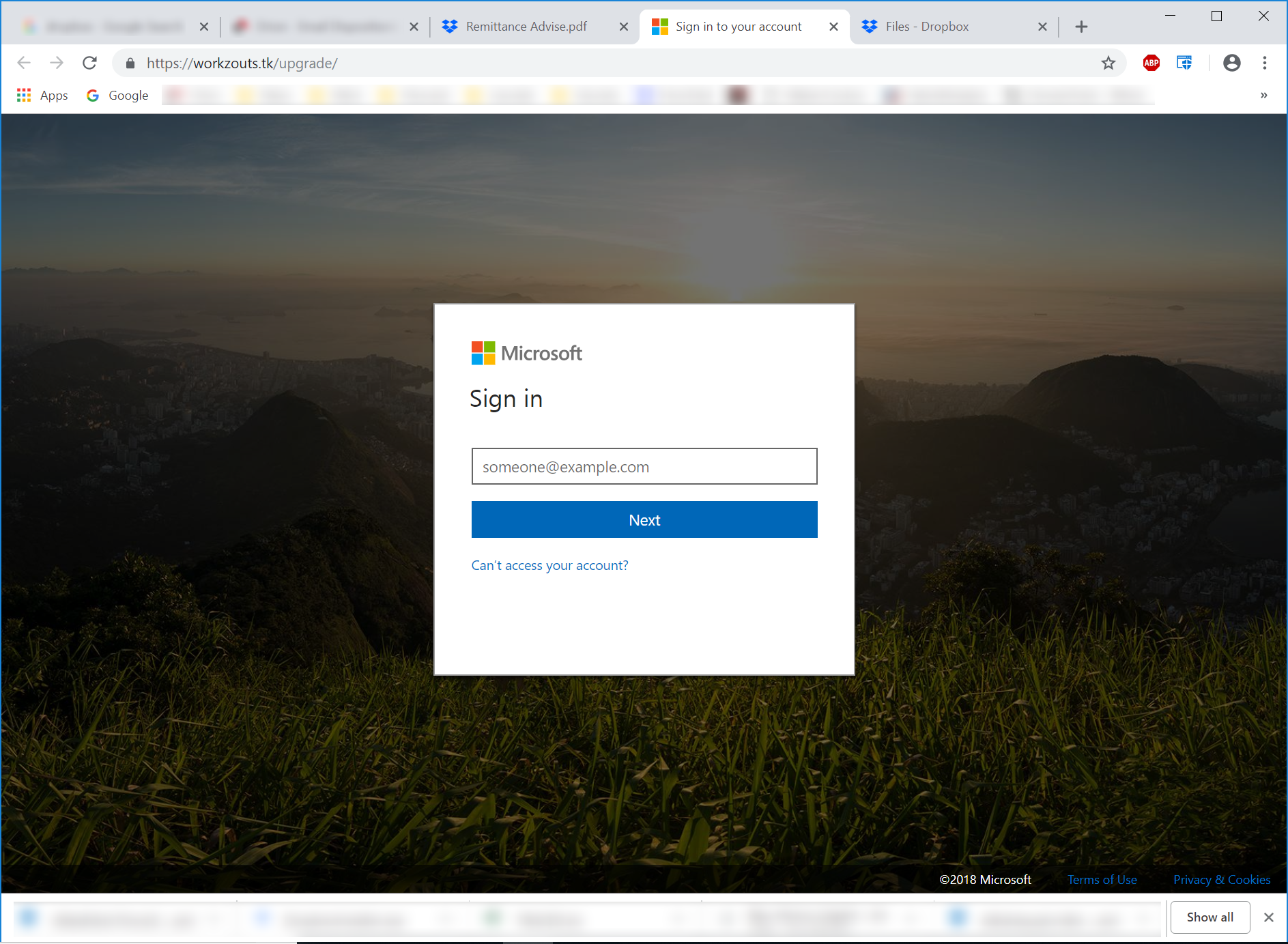
Clues Abound -- For Users Trained to Look for Them
As sneaky as these phishing attacks are, and as difficult as they can prove for ordinary users to spot, the bad guys do manage to leave sufficient clues for users trained to look for and act on them.
If you haven't stepped your users through New-school Security Awareness Training, now is the time to do so -- before they end up on a service like Dropbox cluelessly inviting malicious actors to send them malicious content or provide them more opportunities to fork over their credentials to accounts inside your network.
Do you know what's getting through your mail filters?
KnowBe4 is excited to announce that now you can use our brand new, innovative Mailserver Security Assessment (MSA), to help you assess your organization’s mailserver configuration settings and check the effectiveness of your email filtering rules.
With email still the #1 attack vector used by the bad guys, MSA helps you to see what types of messages may make it through your filters from the outside.
MSA gives you a quick insight at how your mailserver handles test messages that contain a variety of different message types including email with attachments that contain password-protected, macro zipped, and .exe files or have spoofed domains.
Here’s how MSA works:
- 100% non-malicious packages sent
- Select from 30+ automated email message types to test against
- Saves you time! No more manual testing of individual email messages using MSA's automated send, test, and result status
- Validate that your current filtering rules work as expected
- Results in an hour or less!
Find out now if your mail server is configured correctly, many are not!
Don't like to click on redirected buttons? Copy & Paste this link in your browser.
https://info.knowbe4.com/mailserver-security-assessment-blog





