Phishers have found a way of moving the malicious URLs in their emails past Office 365's protections. The security company Avanan says they've observed criminals using a <base> tag in the HTML header used with the URL.
The hack works because newer email clients are equipped to handle the <base> tag, and they render the split URL as a link. Office 365's Advanced Threat Protection includes Safe Links, which checks links in emails against a blacklist. Safe Links would catch a malicious link like this one—Avanan's example, which we hasten to state is a fake:
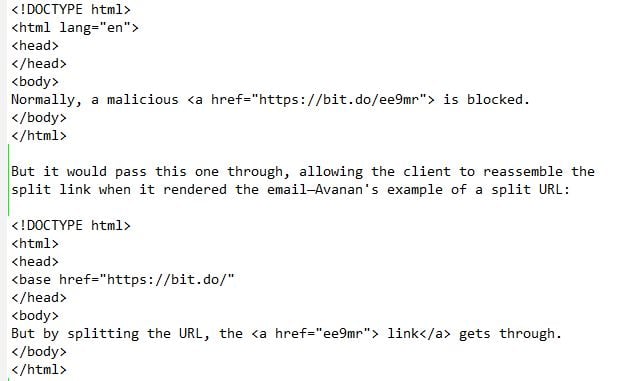
Avanan calls the technique "baseStriker." It works against Microsoft Outlook clients that support the <base> tag. Gmail is said to be immune. Avanan has informed Microsoft, which is investigating. In the meantime Microsoft has told SecurityWeek, "We encourage customers to practice safe computing habits by avoiding opening links in emails from senders they don’t recognize."
That's good advice, and something any organization might wish to reinforce with some realistic, interactive security awareness training. And remember that technical means of defense do have their limitations, which criminals are always actively seeking out. SecurityWeek has the story: https://www.securityweek.com/phishers-use-new-method-bypass-office-365-safe-links
Note that other email clients may be vulnerable to this exploit as well.
Companies like MimeCast and Proofpoint have built-in defenses against this, but there is a cheaper alternative. As a matter of fact, this one costs nothing.
Wouldn't it be great if your users had a way to "roll back time" when they forgot to think before they click on a bad link? Now they can!
Second Chance enables your user to make a smarter security decision by giving them a way to back out of a click that could be in a phishing email. It takes an intelligent look at the clicked URL in email, and asks your user if they are sure they want to do this, in case they clicked on a potentially unsafe or an unknown website. It even prompts your user when they click on a Punycode link!
You might ask: "What happens if my user continues or aborts their action?" If they choose to abort their action, the prompt will be closed, and the URL will not be opened. If they choose to continue, their browser will navigate to the URL they clicked on.
Here's how it works:
- Checks links originated in email messages, including attached Office Docs and PDFs
- Ability to customize the message your user gets after clicking a URL
- You can set "No Prompt" domains
- Get reporting data on what URLs users chose to abort or continue
There are more technical details on our support site.
Second Chance could one day be the difference between a ransomware infection and a free weekend. Give it a try!
PS: Don't like to click on redirected buttons?
Cut & Paste this link in your browser: https://www.knowbe4.com/second-chance





