 Microsoft's Security Intelligence team recently sent an alert to Office 365 users and admins to watch out for a suspicious phishing email that uses spoofed sender addresses.
Microsoft's Security Intelligence team recently sent an alert to Office 365 users and admins to watch out for a suspicious phishing email that uses spoofed sender addresses.
The alert was sent after observing an active campaign that was zoning in on Office 365 organizations with convincing emails.
In a statement by Microsoft, "An active phishing campaign is using a crafty combination of legitimate-looking original sender email addresses, spoofed display sender addresses that contain the target usernames and domains, and display names that mimic legitimate services to try and slip through email filters."
Below is the rest of the alert with the specific example of the phishing page:
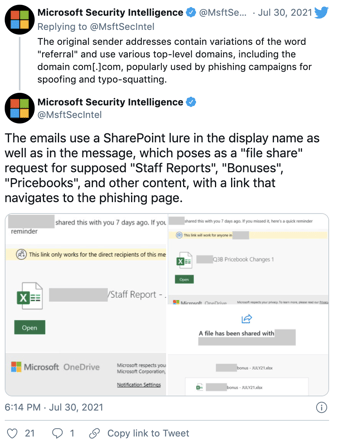
Source: Microsoft Security Intelligence
Microsoft notes that this campaign is sneakier than usual due to the convincing Microsoft logos with the link posing as a 'file share' request to access bogus reports. However, the main phishing URL relies on a Google storage resource that takes the victim to the Google App Engine domain Appspot. This results in hiding a second URL that directs the victim to a compromised SharePoint site, and thus allowing the attack to bypass sandboxes.
We highly recommend frequently testing your users and implementing new-school security awareness training. Your users are the strongest layer of defense that can spot and report any suspicious activity.
ZDNet has the full story.
 Here's how it works:
Here's how it works:




