 That means you can from now on count a ransomware infection as a data breach with all the consequences that this brings. Moreover, the so-called "human-operated" ransomware gangs have stepped up their attacks amid the pandemic to maximize their ill-gotten profits.
That means you can from now on count a ransomware infection as a data breach with all the consequences that this brings. Moreover, the so-called "human-operated" ransomware gangs have stepped up their attacks amid the pandemic to maximize their ill-gotten profits.
In fact, Redmond also reported that they launched more of the file-encrypting malware on target networks in the first two weeks of April than in earlier periods, causing chaos at aid organizations, medical billing companies, manufacturing, transport, government institutions, and educational software providers.
Almost Every Ransomware Infection Had Evidence Of Attackers Viewing And Exfiltrating Data
Microsoft called it a "slight uptick" in the volume of ransomware attacks in the first two weeks of April, usually from ransomware groups that had already gained access to networks several months earlier. "Attackers have compromised target networks for several months beginning earlier this year and have been waiting to monetize their attacks by deploying ransomware when they would see the most financial gain," Microsoft's Threat Protection Intelligence Team said.
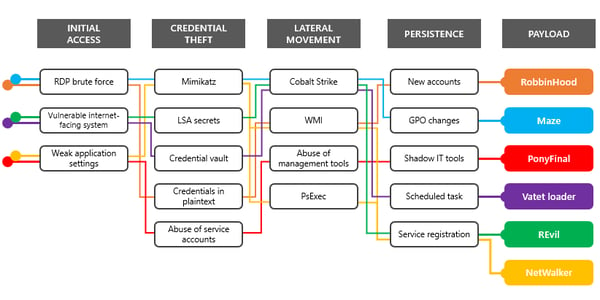
They continue with the observation that these attacks demonstrate that threat actors really don't care that they're impacting critical services during a global crisis,. They also stated that the relatively long lag between compromise and ransomware deployment means that you as a defender should look for signature activity preceding the deployment, which includes credential theft and lateral movement activities, using tools like Mimikatz and Cobalt Strike.
Attackers Often Maintain Control Over Some Endpoints After Deploying Ransomware
Admins who haven't patched vulnerabilities in these systems are asking for trouble, given that attackers are continuously scanning the internet for these unpatched systems. Microsoft also noted a concerning trend among ransomware key groups. Over the past few months, multiple ransomware gangs have taken to stealing data before encrypting it and then threatening to leak it online if a ransom isn't paid.
Microsoft says these attackers often maintain control over some endpoints after deploying ransomware for the purpose of launching future attacks after a ransom has been paid. And while some groups have gained a reputation for selling victims' data, even gangs that didn't advertise they would go down this path still viewed and stole data anyway.
Microsoft's list of top ransomware payloads deployed in April include RobbinHood, Maze, PonyFinal, Valet loader, and REvil. Others include Paradise, RagnarLocker, MedusaLocker, and LockBit.
Microsoft advised defenders to scour networks for malicious PowerShell, Cobalt Strike and other penetration-testing tools that may look like red team activities. They should also look for suspicious access to Local Security Authority Subsystem Service (LSASS) and suspicious registry modification, as well as evidence of tampering with security event logs.
Key systems and vulnerabilities defenders should check for include:
- RDP or Virtual Desktop endpoints without MFA
- Citrix ADC systems affected by CVE-2019-19781
- Pulse Secure VPN systems affected by CVE-2019-11510
- Microsoft SharePoint servers affected by CVE-2019-0604
- Microsoft Exchange servers affected by CVE-2020-0688
- Zoho ManageEngine systems affected by CVE-2020-10189
It is CRUCIAL to step your employees through new-school security awareness training which deploys randomized simulated phishing attacks to keep your employees on their toes with security top of mind, even when they WFH. Sources:




