A cyberattack against Banco De Chile (BDC)—that country's largest financial institution—bricked a hair-raising 9,000 workstations and 500 servers. However, killing these machines was actually just to a cover trying to hide illegal transactions on the SWIFT network where banks transfer funds internationally. After the dust settled, $10 million was funneled off to accounts in Hong Kong.
On Sunday, BDC’s general manager Eduardo Ebensperger told Chilean media outlet Pulso that the late-May attack allowed the attackers to complete four separate fraudulent transactions before the cyberheist was discovered. The massive downtime caused by this wiper-attack will be an order of magnitude more expensive than the 10 mil that was stolen, the bank had to halt almost all operations at its 400 branches throughout the country. It took almost two weeks for the bank to resume normal services.
 The bad guys used extremely destructive wiper malware similar to NotPetya trying to cover their tracks. Its main functionality is to wipe the disk —hence destroying forensics data. Trend Micro analysts discovered that the code is a modified strain of the Buhtrap malware component known as Kill_OS, which bricks the box by overwriting the Master Boot Record (MBR). Here is how that looks close-up.
The bad guys used extremely destructive wiper malware similar to NotPetya trying to cover their tracks. Its main functionality is to wipe the disk —hence destroying forensics data. Trend Micro analysts discovered that the code is a modified strain of the Buhtrap malware component known as Kill_OS, which bricks the box by overwriting the Master Boot Record (MBR). Here is how that looks close-up.
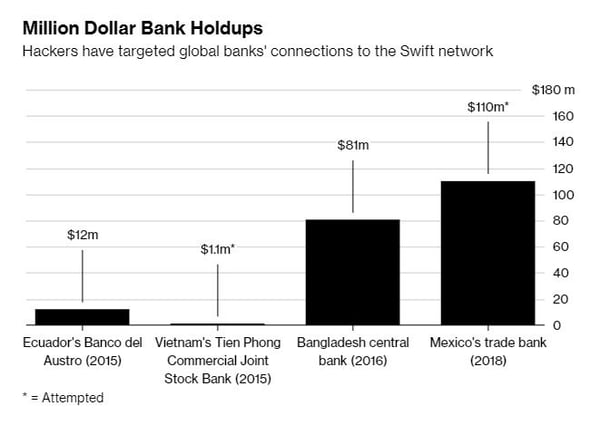
BDC is the latest victim in a string of cyber-attacks targeting Latin American payment transfer systems. For instance, in May, Somewhere between $18 million to $20 million went missing during unauthorized SWIFT money transfers in Mexico’s Bancomext central banking system.
Forensic experts consulted by Bancomext would later tell the bank that hackers had managed to penetrate its Swift connection thanks to 0-day malware that had been activated after an employee clicked on a phishing email attachment. It is expected that the BDC hack was also caused by a similar social engineering attack using email.
"Who Done It", Russia, North Korea or copycats?
The attribution behind the BDC attack remains uncertain.
The Buhtrap malware and its components, including MBR Killer, were previously used by a Russian-speaking hacker collective in attacks against multiple financial institutions in Russia and the Ukraine, Flashpoint noted.
However, Chilean financial institutions were targeted entities by the Lazarus Group, which was linked to North Korea, during the compromise of the Polish Financial Supervision Authority website in 2017,” Vitali Kremez, director of research, told Threatpost in an interview.
Ofer Israeli, CEO of Illusive Networks, said via email that he too believes the North Korea-linked Lazarus Group, which is thought to have carried out the SWIFT attacks in Bangladesh in 2016, is behind it all.
It’s also possible, researchers said, that it’s an entirely different copycat group making use of Buhtrap’s leaked source code and running a false flag operation.
What To Do About It
Trend Micro at the end of their technical write-up gave some good hints and tips about mitigation and best practices:
- Identify and address security gaps
- Secure mission-critical infrastructure
- Enforce the principle of least privilege
- Proactively monitor online premises
- Foster a culture of cyber security: Many threats rely on social engineering to succeed. Awareness of the telltale signs of spam and phishing emails, for instance, significantly helps thwart email-based threats.
- Create a proactive incident response strategy.
We could not agree more. Start by stepping your users through new-school security awareness training, so they stay on their toes with security top of mind. Then install the free Phish Alert Button in so your employees can report phishing attacks that make it through the filters so that your Incident Response team can be proactive.
I strongly suggest you get a quote for your organization and find out how affordable this is. You simply have got to start training and phishing your users ASAP. If you don't, the bad guys will, because your filters never catch all of it. Get a quote now and you will be pleasantly surprised.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat_get_a_quote_now
Let's stay safe out there.
Warm regards,
Stu Sjouwerman,
Founder and CEO,KnowBe4, Inc






