Appleinsider reported Feb 9, 2017: "Mac malware discovered in Microsoft Word document with auto-running macro", which was the second example of malware targeting macOS users this week.
Security researchers have detected the first in-the-wild instance of hackers are making use of malicious macros in Word documents to install malware on Mac computers – an old Windows technique. The hack uses the same social engineering tactic, tricking victims into opening infected Word documents that subsequently run malicious macros.
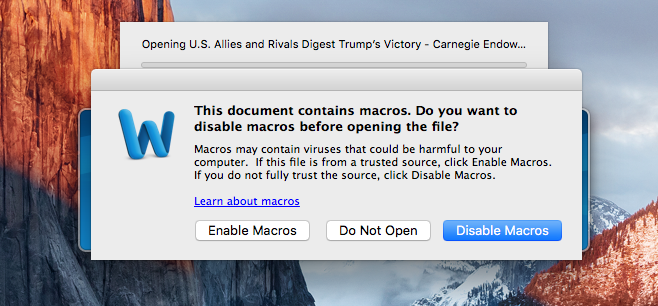
The malicious Word file discovered was titled "U.S. Allies and Rivals Digest Trump's Victory – Carnegie Endowment for International Peace.docm." Mac users are always prompted to enable macros, but the bad guys are going after the weak link, the users.
Clicking the embedded macro executes a function, coded in Python, that downloads the malware payload to infect the Mac PCs, allowing hackers to monitor webcams, access browser history logs, and steal password and encryption keys.
Patrick Wardle, director of research at security firm Synack, said the Python function is virtually identical to EmPyre – an open source Mac and Linux post-exploitation agent. "It’s kind of a low-tech solution, but on one hand it’s abusing legitimate functionality so it’s not going to crash like a memory corruption or overflow might, and it’s not going to be patched out," said Wardle.
Wardle tracked the IP address from which the malicious Word documents were spread to Russia and that IP has previously been associated with malicious activities like phishing attacks. Not surprisingly, macOS malware is targeting mostly the defense industry and reportedly has been used against a human rights advocate.
The best way to avoid these kinds of attacks is to step employees through new-school security awareness training and have them deny permission to enable macros from running when opening a Word document they did not ask for, and avoid downloading software from third-party App Store or untrusted websites.
When KnowBe4 created our simulated phishing Macro attachments we designed and tested them to work with Windows and OSX versions of Office, they automatically detect what platform they're on and react accordingly. We did not think that the bad guys would limit themselves to just the Windows platform. This means that phishing tests sent with our platform will also test Apple users who have been told for years that nothing bad can happen.
Free Phishing Security Test
Did you know that 91% of successful data breaches started with a spear-phishing attack?
Cyber-attacks are rapidly getting more sophisticated. We help you train your employees to better manage the urgent IT security problems of social engineering, spear-phishing and ransomware attacks. Take the first step now. Find out what percentage of your employees are Phish-prone™ with our free test. Did you know that KnowBe4 also supports "Vishing" where you can actually send your users simulated voice mail attacks?
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





