 Check Point Software is one of the world's best-known and largest infosec companies. In September 2021 they acquired email security company Avanan and recently they updated Check Point's initial 2020 research about the email security effectiveness of Microsoft 365 and Defender.
Check Point Software is one of the world's best-known and largest infosec companies. In September 2021 they acquired email security company Avanan and recently they updated Check Point's initial 2020 research about the email security effectiveness of Microsoft 365 and Defender.
The report is very good and strikes the right tone. They start out by saying: "In general, Microsoft 365 is a very secure service. That is a result of a massive and continuous investment from Microsoft. In fact, it is one of the most secure SaaS services on the market. This report does not indicate otherwise.
What this report does note is the challenge that Microsoft has. As the default security for most organizations, many hackers think of email and Microsoft 365 as their initial points of compromise. A good example of how hackers focus on Microsoft 365 comes in a series of blogs from Microsoft that details the attempts of a state-sponsored group to compromise their services.
Hackers have stepped up their game.
Microsoft is the most used and most targeted email service in the world. After a thorough analysis of nearly three million emails, Check Point found that at the moment Microsoft Defender misses 18.8% of phishing emails. Their previous 2020 analysis showed 10.8 percent of phishing emails reaching inboxes, so Defender's missed phishing rates have increased by 74 percent. This represents not a decline in Microsoft effectiveness, but rather an increase in targeted attacks designed directly to bypass Microsoft. Hackers, in other words, have stepped up their game.
Another interesting finding in the report showed that Defender sends seven percent of phishing messages to the Junk folder, so they can still be accessed by the user and possibly clicked on.
It's not all bad news though
There are several areas where Defender does quite well. For example it catches 90 percent of unknown malware, and it's also good at spotting attacks that spoof DMARC. Only 2.5 percent of those make it through to inboxes. It also does quite well with Business Email Compromise, with only 2 percent getting through.
However...
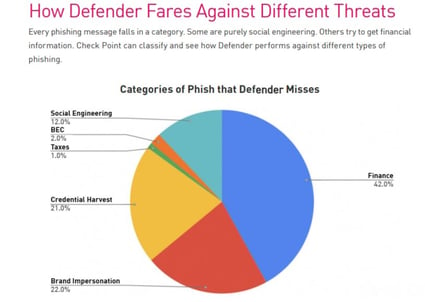
When financial-based phishing attacks have been specifically crafted to bypass Defender it missed 42 percent of them. This category includes things like fake invoices and bitcoin transfers. Brand impersonation is another popular method hackers choose to bypass Defender and 22 percent of these emails get through. 21 percent of credential harvesting attacks also get through to users' inboxes.
Missed phishing rate higher in larger organizations
The missed phishing rate is also higher in larger organizations, reaching between 50 and 70 percent. This is despite security operations center staff in large businesses devoting a large percentage of their time to email issues. One large company studied saw 910 reported phishing emails within one week, yet the IT team could only remediate 59 of these or less than seven percent.
Defender vs. Secure Email Gateways
In another study analyzing 300 million emails, Check point found that Microsoft is in the middle of the pack compared
to the rest of the competition, in this case, Secure Email Gateways. Per every 100,000 emails, Microsoft’s catch rate of phishing emails is better than some Secure Email Gateways and worse than others. The report compares Avanan, Mimecast, Google, Proofpoint and Barracuda. To get the report, start with this article at Betanews. (Registration required.)
SEG's are only part of the picture
it is important to keep in mind that none of these SEG stop the phishes using any other medium beyond email (and maybe web-based social engineering using content filtering). They don't catch SMS phishes, voice-call phishes, social media phishes, WhatsApp phishes, tailgating, and so on.
Even if some magic solution came into being that solved the email phishing issue (highly unlikely), all organizations would still have to manage the ongoing social engineering problem. That's why KnowBe4 trains your users about social engineering in general as the overall threat and how to defeat it REGARDLESS of the medium.
It is super important to improve your overall organization's security culture. Start by getting the 2022 Phishing Industry Benchmarking Report and see how you score against your industry peers.
 The 2024 Phishing By Industry Benchmarking Report compiles results from the seventh annual study by KnowBe4 and reveals at-risk users across 19 industries that are susceptible to phishing or social engineering attacks. Taking it a step further, the research reveals radical drops in careless clicking after 90 days and 12 months of simulated phishing testing and security awareness training using the KnowBe4 platform.
The 2024 Phishing By Industry Benchmarking Report compiles results from the seventh annual study by KnowBe4 and reveals at-risk users across 19 industries that are susceptible to phishing or social engineering attacks. Taking it a step further, the research reveals radical drops in careless clicking after 90 days and 12 months of simulated phishing testing and security awareness training using the KnowBe4 platform.




