New data from Akamai provides insight into why phishing attacks are making it all the way to the endpoint… and why they can trick users so easily into becoming a victim.
Every IT pro would like to believe that by putting a layered security defense in place to specifically stop phishing attacks, the attacks would simply be detected and stopped.
Not so fast.
A new report from Content Delivery Network (CDN) provider Akamai shows that the bad guys are figuring out ways to not just make it past your defenses, but are counting on your browser’s use of a CDN to keep their maliciousness alive.
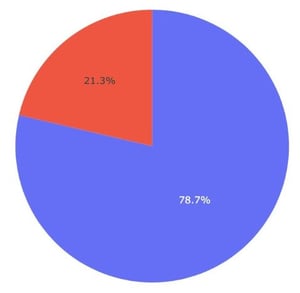
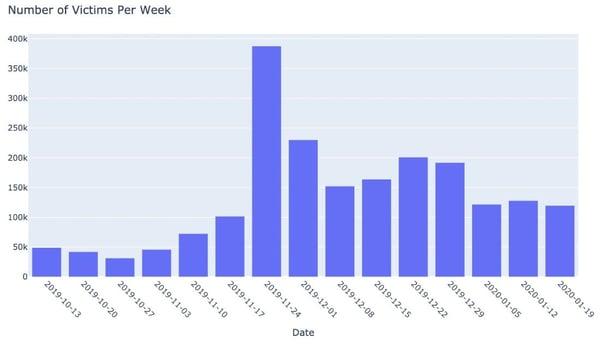
According to Akamai, of over 1200 malicious domains using Akamai’s CDN functionality to deliver malicious content, 21.3% of all phishing URLs used were not known to be malicious to public threat intelligence sources. Akamai estimates that over 2.4 million victims worldwide over a 4-month period were the target of attacks (whether successful or not) using these URLs.
They attribute the attack success to a few factors that may be delivered from a CDN:
- The use of abused brand pages and some of the original brand’s website resources
- The use of legitimate libraries and services
- Redirection to original brand web pages
These techniques both help to avoid detection, as well as create a sense of credibility with potential victims by impersonating well-known brands.
The only way to successfully stop these attacks that make their way into your user’s Inbox is to employ your users user to identify and stop suspicious and potentially malicious emails.
How, you ask? Through Security Awareness Training – by putting them through continual training, you educate them to be vigilant in the same way you are each and every time you open your Inbox. See that email about an invoice that you knew immediately was bogus? That’s what you get with Security Awareness Training; users that are as aware as you that can easily spot and stop and attack before it has an impact.
 Here's how it works:
Here's how it works:




