
Armor, a leading global cloud security solutions provider, read the news about a recent cyberattack, where hackers targeted the payroll department of the city of Tallahassee, FL and absconded with almost $500,000 dollars. Armor’s Threat Resistance Unit (TRU) began digging to find if there had been other similar-style attacks in recent months. They found that a series of cyberattacks, targeting payroll departments and payroll services had transpired.
Armor’s TRU team discovered that three payroll-related cyberattacks have occurred between February and April 2019 in the southeastern U.S. Interestingly, these incidents came on the heels of the massive "Collection #1" data dump discovered in January 2019. TRU’s analysis of the Collection #1 data revealed that amongst the almost 773 million unique email addresses and passwords were the email credentials and plain-text passwords for over 240 payroll departments from apparently at least 240 different organizations.
While Armor is not aware of any connection between these payroll-related attacks, the incidents follow a September 2018 warning from the FBI's Internet Crime Complaint Center (IC3) that cybercriminals are targeting the online payroll accounts of employees in a variety of industries to include education, healthcare and commercial airway transportation.
According to the IC3, these attacks use phishing emails to steal employee login credentials. Armed with these credentials, the attackers can access employee payroll accounts and modify account settings to prevent the employees from receiving alerts about changes made to their payroll direct deposit status. Direct deposits destinations are then changed as the payroll deposits are redirected to accounts controlled by the cybercriminals, often in the form of prepaid cards.
These security incidents serve as a stark reminder to organizations to stay on top of the latest cyber threats -including managing risks posed by third-party vendors and partners. Below are some suggested mitigations from Armor.
9 Security Tips for Protecting Against Payroll-Related Cyberattacks
- Implement separation/segregation of duties for critical transactions: This key security principle mandates that the agent responsible for conducting a transaction cannot be the same agent responsible for checking or approving the transaction. When this principle is implemented properly it provides an effective control measure against malicious insiders and external threat actors alike who have gained access to critical systems.
- Classify third-party vendors and partners: Organizations should categorize their third-party partners and vendors according to risk, factoring in each vendor’s level of access to their network and any critical data the vendors may have. Organizations should also take steps to ensure vendors have properly implemented security policies commensurate with their calculated risk levels.
- Choose vendors wisely: The security strategy and reputations of third-party companies should be closely evaluated before organizations begin doing business with them or trusting them with any type of system access or data. Likewise, once they have system or data access, third-party partners and vendors should be continuously monitored and audited on a regular basis.
- Employ strong security controls: Use robust, continuously-updated antimalware and active threat mitigation controls across all endpoint devices and application platforms.
- Keep IT systems and software up-to-date: Organizations should apply software security patches and updates as soon as possible.
- Perform security awareness training: Employees, continually educated about current and emerging cybersecurity risks, can better identify phishing emails and suspicious behavior. Effective security awareness training should invoke active employee engagement and institutionalize the correct response to suspected phishing attempts. With proper foundational and enhancement training, employees can effectively act as cybersecurity monitoring and reporting sensors in a potent line of defense against cyber-attacks.
- Be smart about passwords: Employees should utilize strong passwords, and NEVER reuse passwords across multiple sites. These passwords should change periodically in accordance with a set policy.
- ALWAYS use multi-factor authentication for access to critical systems: This provides an extra layer of security to prevent unauthorized access.
- Develop a secure backup strategy: Ensure all critical data, applications, and application platforms are backed up by password-protected backup/redundancy systems.
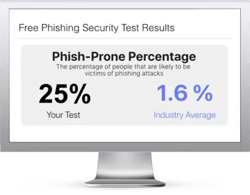
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
Would your users fall for phishing attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here's how it works:
 Immediately start your test for up to 100 users (no need to talk to anyone)
Immediately start your test for up to 100 users (no need to talk to anyone)- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





