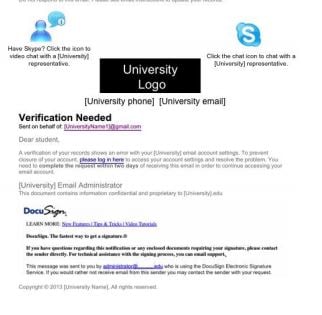
 A successful phishing attack has several elements that all together convince the victim that the email is legit and that they need to act on the message. One of these elements sems to be graphics.
A successful phishing attack has several elements that all together convince the victim that the email is legit and that they need to act on the message. One of these elements sems to be graphics.
Researchers at the University at Buffalo have found evidence that the incredible spread of email phishing scams may be due to phishers’ increased use of “information-rich” emails that alter what they call recipients’ "cognitive processes" in a way that facilitates their victimization.
The study, “Examining the impact of presence on individual phishing victimization,” was presented (PDF) at the 48th Hawaii International Conference on System Sciences, held Jan. 5-8 at the University of Hawaii.
Arun Vishwanath, professor of communication at the University at Buffalo, and co-author of the study, says “information-rich” emails include graphics, logos and other brand markers that communicate authenticity.
“In addition,” he says, “the text is carefully framed to sound personal, arrest attention and invoke fear. It often will include a deadline for response for which the recipient must use a link to a spoof ‘response’ website. Such sites, set up by the phisher, can install spyware that data mines the victim’s computer for usernames, passwords, address books and credit card information.
The study involved 125 undergraduate university students, who were threatened with their email account being closed down. Vishwanath says 49 participants replied to the phishing request immediately and another 36 replied after a reminder. When a few other variables were factored in, the phishing attack had an overall success rate of 68 percent.
Looks like these grad students should be stepped through some effective security awareness training before they hit the workforce, because this is a pretty basic social engineering trick that was used.
Find out how affordable this is for your organization today.





