Note: I got this too and had a similar reaction last week.
Security researchers say the legitimate email is training people to have bad email hygiene.
Richard De Vere, a security consultant who specializes in social engineering, said that even though the Google email we got is not a phishing attempt, it is so good at luring people to click on a link that he plans to add it to his brochure of good phishing attacks to use it in his ethical hacking engagements.
“It has urgency, guides to a login page, quite vague, but alarming...we used to take legitimate Google emails and adapt, but this is just perfect as is. [...] It’s that good,” he tweeted. “Unforgivable for Google to send this out en masse.”
The company told me that this alert is the result of months of experiments, and this version of the alert had the best engagement (meaning people actually opened and clicked it). There are no specifics in it because the company wanted to avoid giving hackers hints about what was wrong with the account, and the company concluded that the extra click required to get to the checkup was a security feature in this case.
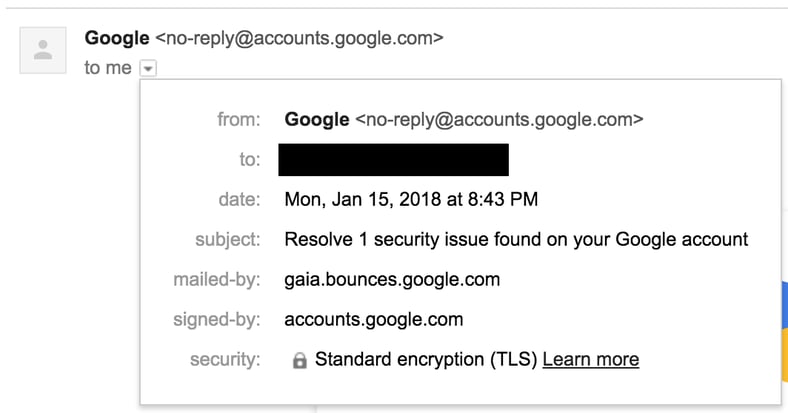
Holmes stressed that when someone receives an alert like this, the right thing to do is to first “take a deep breath,” and then open a new browser window and manually type and navigate to the settings of the service in question (in this case, to myaccount.google.com/security-checkup) and see what’s going on there, without ever clicking on the link in the email.
“They are walking a fine line here: if your account is compromised, they don’t want to give your attacker too much specific info as to how,” Holmes told me in an online chat. “They just give you enough info to hopefully get your attention. Continued at Motherboard: https://motherboard.vice.com/en_us/article/7xemne/google-gmail-security-alert-phishing-attempt
Find out what percentage of your employees are Phish-prone™ with our free Phishing Security Test (PST). If you don't do it yourself, the bad guys will.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





