 In our previous blog post, we discussed the behavioral science behind why people click on malicious links. So far in this series, we’ve established that our old security playbooks are broken and that we’re dealing with the complexity of humans. Trying to tackle that all at once can feel like herding cats. What we need is a simple, memorable mental map to bring structure to the chaos.
In our previous blog post, we discussed the behavioral science behind why people click on malicious links. So far in this series, we’ve established that our old security playbooks are broken and that we’re dealing with the complexity of humans. Trying to tackle that all at once can feel like herding cats. What we need is a simple, memorable mental map to bring structure to the chaos.
Let’s go DEEP.
DEEP is a conceptual framework that breaks down a holistic Human Risk Management (HRM) strategy into four interconnected pillars. Explored in depth in our recent whitepaper, it ensures you’re building a balanced program that doesn't just rely on one type of defense.
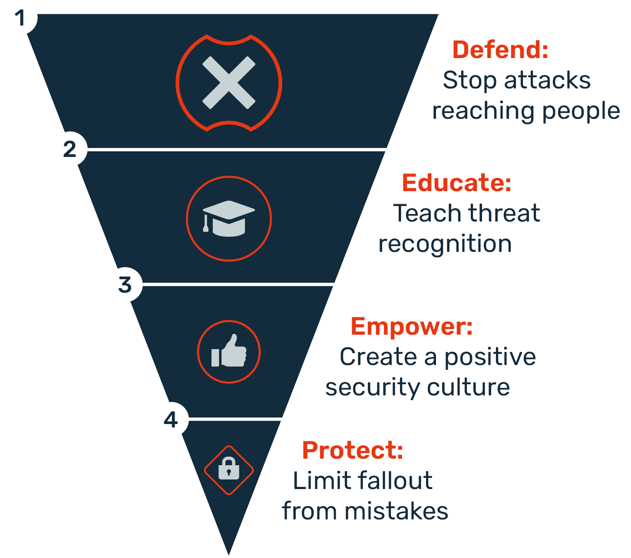
Defend: This is the proactive, technical front line. It’s about using smart technology, like AI-enhanced email security and link scanners, to shrink the attack surface. The less malicious stuff that lands in front of your people, the fewer chances they have to make a mistake. This is about making it harder for the bad stuff to get through in the first place.
Educate: This is where we move beyond "awareness" and start building real skills. It’s about equipping employees with the know-how to spot a scam through engaging training, realistic simulations, and content that actually sticks. This isn’t death-by-PowerPoint; it’s about turning "Oh Dear" moments into "Aha!" moments with relevant, often AI-tailored, micro-training.
Empower: This is arguably the most important—and most overlooked—pillar. It’s about creating a culture where the secure choice is the easy choice. It’s one thing to know what to do; it’s another to feel able and supported to do it. This pillar is where you truly build your security culture, transforming it from a list of rules into a shared value.
Protect: Let’s be realistic: mistakes will happen. This pillar is about damage limitation. It’s about having robust incident response plans and tools (like PhishER Plus automating the cleanup) that can quickly contain a threat, and then—crucially—learning from every incident to make the other three pillars even stronger.
The "Empower" pillar is about creating a security culture built on proven principles. Think of it like building a temple. And a strong security culture is supported by five foundational pillars:
Creating Champions: You can't be everywhere at once. Empowering influential employees as peer-to-peer security advocates is invaluable.
Sharing Stories: Policies are dry; stories stick. Anonymized tales of near-misses make risks tangible.
Intensity vs. Consistency: A gentle, consistent drumbeat of engagement builds lasting habits far better than a once-a-year security blitz.
Choice Architecture: Intentionally designing systems (like a one-click report button) so the secure path is the easiest path.
User-Centric Security: Putting users at the center of security decisions to reduce friction and prevent risky workarounds.
Now we have a framework. But how do we apply it to the real, messy, diverse group of people in our organizations?
Make sure not to miss our next blog post in this series in which we’ll introduce the DEEP Matrix, a practical tool for mapping your strategy to your people.




