 Most computer security practitioners have understood for many years the importance of having an aggressive security awareness training program. As social engineering is involved in 70% to 90% of all successful hacking attacks, not addressing the human element is not an option. Still, some of the regulatory documents have been slow to come around. Not anymore.
Most computer security practitioners have understood for many years the importance of having an aggressive security awareness training program. As social engineering is involved in 70% to 90% of all successful hacking attacks, not addressing the human element is not an option. Still, some of the regulatory documents have been slow to come around. Not anymore.
Gramm-Leach-Bliley Act (GLBA) Closed the Gap
Among many requirements, the 1999 Gramm-Leach-Bliley Act (GLBA) was one of the first broad federal initiatives to require US financial organizations to implement security controls to protect customer data and it made corporate executives PERSONALLY liable for complying. It is known as the Safeguard Rule. Nothing wakes up corporate executives more than regulations with personal liability.
The GLBA applies to "financial institutions," which are defined as:
- Banks, savings associations, and credit unions that are chartered or insured by federal or state governments;
- Securities firms, such as broker-dealers, and investment companies;
- Insurance companies that provide certain types of financial products or services; and
- Companies that provide certain types of financial products or services to consumers, such as financial or investment advice, tax preparation, or debt counseling.
It is important to note that the GLBA also applies to third-party service providers that perform services for financial institutions, such as data processing, back-office operations, and call center services. These service providers must also comply with the GLBA's privacy and security requirements.
Deadline June 9, 2023
Unfortunately, the first version of GLBA did not directly require security awareness training. This glaring omission has finally been fixed. The US Federal Trade Commission (FTC) announced that mandatory updates to the GLBA Safeguard Rule must be in effect by June 9, 2023. Key among those updates is a requirement for all regulated entities to have a security awareness training program. Specifically, Title 16, Chapter 1, Subchapter C, Part 314.4(e)(1) says, “Providing your personnel with security awareness training that is updated as necessary to reflect risks identified by the risk assessment”.
Most other regulatory documents have either already recognized the importance of security awareness training long ago and/or increased the importance of it over time. For example, the Health Insurance Portability and Accountability Act (HIPAA), created in 1996, officially required security awareness training (in section 164.308(a)(5)(i)) by 2003. The US government required security awareness training in 2006 as part of NIST Special Publication 800-53. NERC, the North American Electric Reliability Corporation, had security awareness training requirements (adopted in CIP-004-4) by 2012.
In some cases, weaker security awareness training requirements of some regulatory requirements were improved over time. For example, the Payment Card Industry Data Security Standard (PCI-DSS) has required security awareness training since they released version 1.0 of their document in 2004 (as part of the twelfth and last requirement).
But up until the latest version, version 4.0, released in March 2022, coverage was very minimal. The previous version of PCI-DSS, 3.2.1, released in May 2018, is 129 pages long, but only has 6 sentences and 3 controls discussing security awareness training (see the image of the relevant PCI-DSS text below).
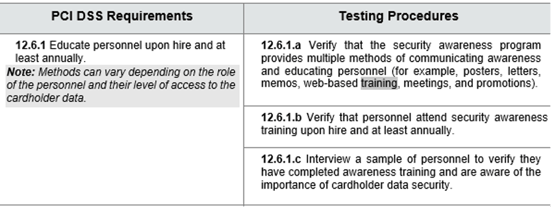
That is not a lot of coverage when phishing and social engineering is the number one root cause of most cybersecurity incidents by a large margin (unpatched software is a distant number two).
PCI-DSS’ coverage of security awareness training as a mitigation is in comparison with the 8 pages and 35 controls related to firewalls, the very first requirement, which do not work nearly as well as aggressive security awareness training. Version 4.0 of PCI-DSS, which is over 356-pages long, partially fixed the disparity by now having 5 security awareness training-related controls described over 4 pages (as compared to the previous version 3 controls over 6 sentences).
And this is a pretty time-worn pattern, that of security awareness training getting more coverage over time in cybersecurity regulatory documents. Although, surprisingly, some cybersecurity standards are moving backwards and devoting less space to security awareness training over time. For example, the international cybersecurity standard known as ISO 27001/27002, had some basic security awareness training requirements in the first version in 2005. The language was very general and most people reading the section probably didn’t come away with a need to start a security awareness training program.
But by the second version released in 2013, an entire section (7.2) had been created, with specific recommendations devoted to security awareness training. Unfortunately, the 2022 version, shrank the section on security awareness training (section 7.3) to a few general sentences, none of which seem to truly indicate the importance of establishing and using an aggressive security awareness training program. The authors of the 2022 version seemed intent on creating less pages and few specific requirements, but in doing so seem to wipe out the single best mitigation (i.e., security awareness training) that could best help most readers.
Luckily the US government, early on, understood the importance of a good cybersecurity training program. Part of that was, starting in 2004, by declaring the entire month of October, Cybersecurity Awareness Month. The Cybersecurity & Infrastructure Security Agency (CISA) still has a big commitment to security awareness training and offers one of the biggest repositories of public-based, free, content and tools.
You Need Frequent Training
KnowBe4 welcomes increased coverage of security awareness training. We know that it is one of the best things any organization can do to address human risk management and build a strong security culture. Any regulatory document or agency recommending or requiring a security awareness training program is welcomed.
However, most regulatory documents either do not recommend a specific frequency in which cybersecurity training should occur or if they do, only require annual training. KnowBe4’s data over tens of thousands of customers have shown us that training only once a year is not enough. In most cases, training just once a year has nearly the same effectiveness as never training. We don’t see significant decreases in human-based risk until the training is at least done quarterly and we really see the biggest payoff with at least monthly training and simulated phishing campaigns. If you want to stop social engineering, your security awareness program needs to be educational, entertaining, frequent, and redundant. Anything less will raise your risk of a social engineering attack getting through your human-based firewall.
If you need help convincing senior management your need to implement a security awareness training program, you can use the relevant regulator guide. If you want to make the most effective security awareness training program possible, talk to KnowBe4.
 The ModStore Preview includes:
The ModStore Preview includes:




