 Now, here is an interesting one. Gigabyte BRIX are very small computers, similar to Intel NUCs, that can be used to replace those bulky desktop towers. I am using Intel NUCs myself at the house and the office.
Now, here is an interesting one. Gigabyte BRIX are very small computers, similar to Intel NUCs, that can be used to replace those bulky desktop towers. I am using Intel NUCs myself at the house and the office.
Well, these small devices have no hard disk and everything lives in different types of memory. At the BlackHat Asia 2017 security conference, researchers from cyber-security firm Cylance disclosed two vulnerabilities in the firmware of Gigabyte devices, which allow an attacker to write malicious content to the UEFI firmware.
Unified Extensible Firmware Interface (UEFI) is a specification for a software program that connects a computer's firmware to its operating system (OS). UEFI is expected to eventually replace BIOS.
Major FAIL on the part of Gigabyte who did not implement write-protection on their UEFI, and neither a system that cryptographically signs their firmware files.
During their presentation, researchers installed a proof-of-concept UEFI ransomware, preventing the BRIX devices from booting, but researchers say the same flaws can be used to plant rootkits that allow attackers to persist malware for years. Patches are being readied, and if you have Gigabyte devices include GB-BSi7H-6500 (firmware version vF6), and GB-BXi7-5775 (firmware version vF2) in your network, read this post at Bleepingcomputer:
Otherwise, keep track of firmware updates on any other diskless devices you run, because this is something you will see more of.
I'm excited to announce a new resource for you, our new Ransomware Simulator.
How vulnerable is your network against ransomware? Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.
Here's how RanSim works:
![]() 100% harmless simulation of a real ransomware infection
100% harmless simulation of a real ransomware infection![]() Does not use any of your own files
Does not use any of your own files![]() Tests 10 types of infection scenarios
Tests 10 types of infection scenarios![]() Just download the install and run it
Just download the install and run it ![]() Results in a few minutes!
Results in a few minutes!
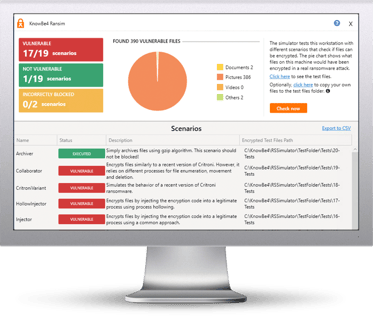
NOTE: Created for Windows-based workstations running Windows 7+. RanSim does not alter any existing files on disk. As part of the simulation RanSim does enumerate all files on the local disk(s). For the purposes of encryption, simulated data files are downloaded from the Internet.
Don't like to click on redirected buttons? Copy & paste this link in your browser:
https://www.knowbe4.com/ransomware-simulator





