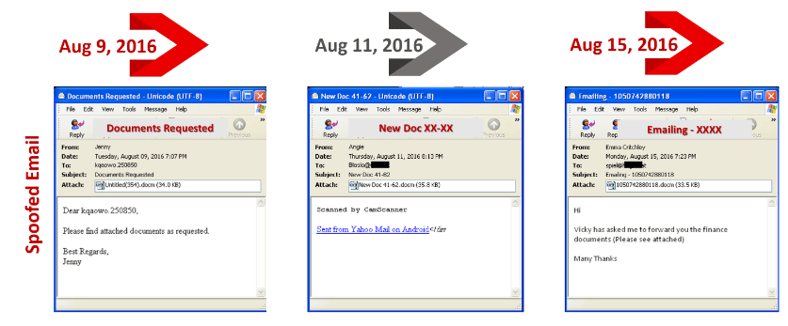
The dangerous Locky ransomware is being hurled at a variety of industries, healthcare being the number one target, according to FireEye researcher Ronghwa Chong. We have talked about Locky on this blog since it first emerged and this strain is as nasty as it gets. "Throughout August, FireEye Labs has observed a few massive email campaigns distributing Locky ransomware," Chong stated in a blog post.
"The campaigns have affected various industries, with the healthcare industry being hit the hardest based on our telemetry. The volume of Locky ransomware downloaders is increasing and the tools and techniques being used in campaigns are constantly changing." Here is a graph of the volume by day and the payloads:
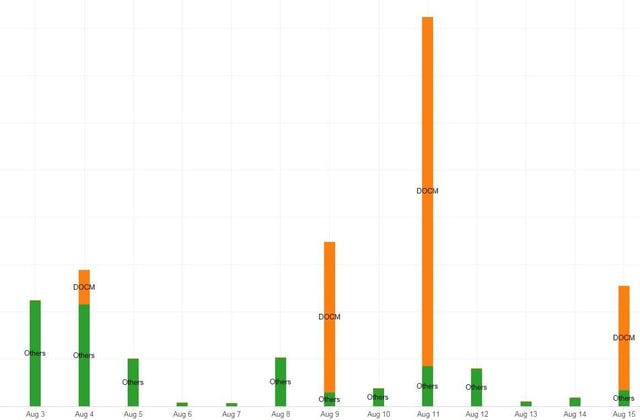
Ransomware mafias have shifted to DOCM format attachments, and each email has a unique campaign code used to download Locky from a command and control server to victim machines, and Chong warned "These latest campaigns are a reminder that users must be cautious when it comes to opening attachments in emails or they run the risk of becoming infected and possibly disrupting business operations." We would agree :-)
Security firm Proofpoint recently confirmed that 69% of email attacks that used malicious document attachments featured Locky ransomware in Q2, compared to 24% Q1. Last month Locky claimed top spot for email-based malware in Q2, overtaking Dridex.
So why did FireEye take an interest in what is really a run-of-the-mill Locky ransomware campaign -- the kind that has been going on every week since, say, April or May? Here's a good guess: What FireEye's Stock Crash Says About Hacking.
All These Strains Rely On Social Engineering
You simply cannot sit back and hope your filters are going to catch it all, they never do. You have to create an additional layer, call it your "human firewall". Thousands of organizations are doing this with great results. Most of you have to do this anyway to be PCI compliant so why not do it right the first time.
Stepping your users through new-school security awareness training is a must, moreover it's simply fun to phish your users and train them not to fall for social engineering attacks! Find out how affordable this is for your organization and be pleasantly surprised.
Don't like to click on redirected buttons? Cut&Paste this in your browser:
https://info.knowbe4.com/enterprise_get_a_quote_now





