 Cyber security firm FireEye reported that that a number of Canadian mines and casinos were hacked by a group named FIN10 – FireEye labels FIN10 to be “one of the most disruptive threat actors observed in the region.” It has been identified that these cyber criminals might be native English speakers.
Cyber security firm FireEye reported that that a number of Canadian mines and casinos were hacked by a group named FIN10 – FireEye labels FIN10 to be “one of the most disruptive threat actors observed in the region.” It has been identified that these cyber criminals might be native English speakers.
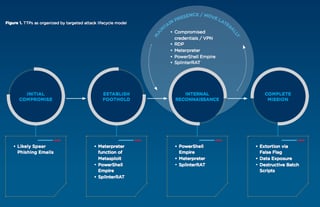
FIN10 used phishing campaigns with malicious links, attachments, and documents, and also led users to compromised websites masked as either a legitimate holiday scheduling system or providing access to an online document like Google Docs. Clicking or accessing these would activate the ransomware and drop remote access trojans.
Combination of Ransomware and Data Breach
As part of the campaign, FIN10 has apparently both locked machines with ransomware and hacked into the networks of different mining companies and casinos in Canada and exfiltrated critical information with regards to customers’ habits and other system-level data.
According to the FireEyes's research (PDF), FIN10 has been in the wild since 2013 and had gone undetected until 2016. It is only now that the attacks have been linked to the group. However, the identity and location of the perpetrators remain to be unknown.
The senior manager of FireEye, Charles Prevost, is unclear why Canada has been the primary target. Data stolen included information on customer betting habits from casinos and other relevant information belonging to mining companies. Also, the malware allowed the hackers to delete or change files and affect critical databases.
The ransom demanded
The ransom demanded was around 100 to 500 Bitcoins, to be paid in 10 days if the victims did not want their data to be released publicly. Those who did not comply with the group’s terms had their systems completely shut down, closing down operations altogether.
Victims’ names not yet revealed
When asked about who the victims were, FireEye did not tell the specific names and simply said that less than ten companies have been infected. However, there have been recent attacks that targeted certain casinos including the Cowboy’s Casino along with mining organizations such as the Goldcorp and Detour Gold Corporation. It's not been confirmed, but the same casinos and mining companies might have been the victims of FIN10 as well.
There is something that can be done about this now
The vast majority of these attacks start with phishing emails. KnowBe4's integrated training and phishing platform allows you to send fully simulated phishing emails so you can see which users answer the emails and/or click on links in them or open infected attachments. If you have a Platinum subscription you can even send them "vishing" attacks straight to the phone on their desk.
See it for yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo




