 In a recent official advisory, the FBI warned about the threat of callback phishing (among other threats). Below is the relevant excerpt.
In a recent official advisory, the FBI warned about the threat of callback phishing (among other threats). Below is the relevant excerpt.

Source: FBI
If you are not familiar with callback phishing, it is usually a phishing email that arrives into a user’s email inbox, containing some sort of usual phishing message requiring the user’s urgent response. But unlike traditional email phishing, it does not contain a URL linked to a malicious site or content. Instead, it contains a phone number that the user is prompted to call. Here are two examples.
The first example:

The second example:

The second example is a fraudulent receipt for McAfee antivirus.
In both cases, the sender is attempting to scare the user into making the call so that their credit card will not be charged for these made-up charges.
There are no other clickable URL links in the email. Anything that looks like it could be a clickable link is not. In most cases, including these two examples, the entire phishing message is just one un-clickable picture. Also, the phone number to call is displayed prominently more than once. The phishing message is begging the user to call.
When the user calls, they are normally sent to an overseas call center. Oftentimes, the call center person is handling so many callback scams that they do not know which scam the potential victim has been sent and they will ask for more details so they can familiarize themselves with the particular version of the callback scam that the user received.
In the FBI’s case, however, the callback numbers lead to the ransomware group’s call center, which is ready for the specific scam. They want to maximize their ability to get their ransomware on the victim’s computer.
As with typical callback scams, the hacker wants to induce the user into installing new software. In the past, the software might have been a custom backdoor or trojan horse program. These days, the installed program is likely to be a legitimate (or semi-legitimate) remote access program that legitimate admins and users might use to manage computers they are authorized to use. But in the callback scams, the legitimate software is used so that the remote attacker can install more malicious programs, scripts and watch the user’s screen.
In the ransomware case, the attacker will eventually convince the victim to install ransomware. In the generic callback scams, typically the remote scammer is going to induce the user to go to their bank account to send or receive money. The scammer’s remote access allows them to manipulate the transaction into stealing the victim’s money and hiding the malicious manipulation.
Callback phishing scams are becoming more and more popular because they are harder for anti-phishing content filters to block. With traditional phishing attacks, the anti-phishing content filters can review the sent text and open the URL locations to see if they contain malicious content or code. There are content and objects that can be examined to determine whether or not the email is malicious.
With callback phishing, the entire message is one big picture. Many anti-phishing content filters cannot “read” the text on the picture. The best they can do is look at the name or hash of the picture file, both of which can easily be made unique and individual for each potential victim.
Hint: If you want your anti-phishing content filter to be able to read the text on a picture file, it should have Optical Character Recognition (OCR) capabilities.
Second, none of the anti-phishing content filters will read the phone number and then be able to determine if it is malicious or not. The anti-phishing filters do not call the number and none of the existing content filters have “malicious phone number” lookup databases. So, basically the entire phishing scam comes in as a single picture file, which contains few to no clues about whether the request is malicious or not.
Defense
First, educate your end users so they know about callback phishing. Be super suspicious of any email that contains only a single picture file, a repeated phone number and no clickable links.
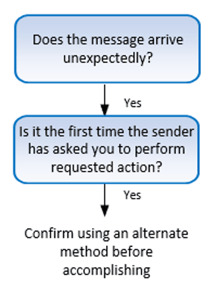
Even better, teach your end users to be wary of any incoming message with these two traits:
- Message arrives unexpectedly (you were not expecting it)
- It is asking you to do something you have never been asked to do before (at least by that sender)
If a message arrives with these two traits, it has a higher chance of being malicious. Confirm using some other alternative method before performing (i.e., call the company directly using a known good phone number, go directly to the legitimate website, etc.).
This is the same advice represented graphically:
Callback phishing scams are an increasingly big problem, even going so far as to come under the FBI’s concern and warning program. Until anti-phishing technical defenses get better at detecting and blocking callback scams, the best you can do is to educate people on how to recognize them and how to mitigate and appropriately report them. A little knowledge can do wonders for protection.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




