 A creative mix of phishing emails, solid social engineering, use of Facebook Messenger, brand and site impersonation, and a sense of urgency all add up to a believable attack.
A creative mix of phishing emails, solid social engineering, use of Facebook Messenger, brand and site impersonation, and a sense of urgency all add up to a believable attack.
Most phishing scams take users through a series of hoops to jump through to avoid detection – so much so, that the hoops themselves should serve as a red flag. But in the case of a new Facebook-themed phishing attack documented by security vendor Trustwave, the steps taken are likely so unfamiliar to the victim, that they will be thrown off completely and will simply follow the steps… to give up their Facebook credentials.
The scam starts with a simple enough email from “Facebook” stating “your page has been scheduled for deletion for violating our Community Standards.” The “Appeal Now” call to action takes users to a Messenger conversation with a chatbot under the name of “Page Support”.

Source: Trustwave
The chatbot “requires” that the user be logged onto Facebook, prompting the user to log on. Within the chat is an opportunity to appeal the page deletion which takes the user to a Facebook-branded (but impersonated) “Support Inbox".

Source: Trustwave
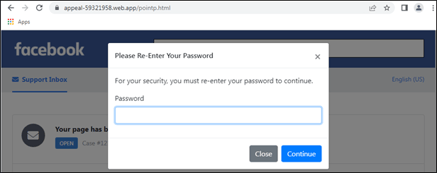
The initial “appeal” form asked for login, name, and phone number. But the sneaky step is how they ask for the password. Take a look – I find this to be believable enough to fool those that aren’t tech-savvy:
Source: Trustwave
Since the user has already experienced logging onto Facebook during this scam, this step feels like it’s legitimate. There’s even a fake one-time password request sent to the mobile phone number supplied to make this seem legitimate.
What makes this scam scary is that it can just as easily be pretending to be your organization’s instance of Salesforce, Microsoft 365, or any other critical SaaS application. Users need to be aware of such attacks via Security Awareness Training so they don’t fall for the initial email in the first place, nullifying all the social engineering effort in the attack that will, no doubt, establish some credibility and gain the attackers some victims.
 Here's how the Social Media Phishing Test works:
Here's how the Social Media Phishing Test works:




