 Rather than take the usual path of sending an email and linking to a spoofed logon page, this attack takes a different set of actions that at first make no sense but may actually be brilliant.
Rather than take the usual path of sending an email and linking to a spoofed logon page, this attack takes a different set of actions that at first make no sense but may actually be brilliant.
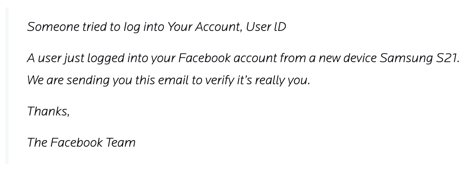
So, you get an email that seemingly looks like every phishing email you've received – pretty bland and simple, but with a message that those not in IT could fall for:
 Source: Malwarebytes
Source: Malwarebytes
Now, you’re probably thinking that there’s a link to a look-alike Facebook page so threat actors can steal your credentials, right?
In this case your wrong. Security researchers at Malwarebytes have uncovered a multi-stage scam that starts with an email like the one above, but the link provided opens a new pre-filled email using a mailto: link to begin a dialog with a “customer support” person of some type.
At first glance, this seems like a really dumb step. But when you think about how the “email-to-logon page” method has been overdone, this may actually be an unexpected twist that may actually increase credibility. The emails contain the usual “good enough to pass a cursory glance” test, and the assumption is eventually the customer service person will ask for the victims credentials, or perhaps credit card details, etc.
So, is this dumb or brilliant? Time will tell.
 Here's how the Social Media Phishing Test works:
Here's how the Social Media Phishing Test works:




