 Millions of business accounts on Facebook are the target of a new malware attack, which is seeing a success rate of 1 out of 70, causing concern for the security of corporate credentials.
Millions of business accounts on Facebook are the target of a new malware attack, which is seeing a success rate of 1 out of 70, causing concern for the security of corporate credentials.
A new Python-based multi-stage infostealer is rearing its ugly head across business Facebook Messenger accounts that is proving to be rather sophisticated in its ability to evade detection. Security researchers at guard.io have documented how the malware – dubbed “MrTonyScam” – is so effective.
The attacks begin using different theming – some bring up the supposed misuse of a photo, others maintain that the business page is violating Facebook policy, and some even pretend to want to purchase a product from the business. In the end, each sends the user managing the business page a link to a RAR file with a filename that somewhat matches the scam theming (e.g., starting the filename with “photo” for the photo misuse scam).
Once the RAR file is opened, the contents are extracted, a dropper is executed, a second dropper is pulled down from GitHub, which pulls down the Python-based infostealer. According to guard.io, this attack uses several methods of obfuscation to avoid detection. In the end, the accounts stolen by this scam are sold on the DarkWeb:
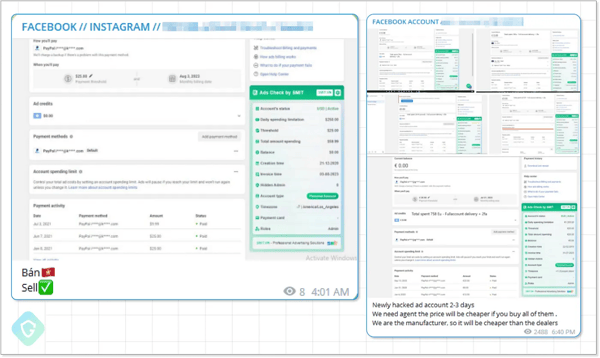
The Achilles heel for these attacks is the filename – in every case, the file’s extension of “.RAR” is clearly visible. If those users involved with managing the company’s social media were put through security awareness training, they’d know to be mindful of the file extension and spot the attack without aiding in its success.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




