 A Swiss phishing study involving roughly 15,000 participants in a 15-month experiment produced some interesting results. The study was run by researchers at ETH Zurich, working together with a company that remained anonymous.
A Swiss phishing study involving roughly 15,000 participants in a 15-month experiment produced some interesting results. The study was run by researchers at ETH Zurich, working together with a company that remained anonymous.
The company did not inform their employees about the simulated phishing program they were going to be part of. The four goals of the study were to determine:
- Which employees fall for phishing
- How vulnerability evolves over time
- How effective embedded training and warnings are
- Whether employees can do anything to help in phishing detection.
The test started by first deploying an email client "phish alert" button that allowed employees to report suspicious emails easily, and as the next step sent simulated phishing tests to employees' work email address for more than a year.
A few takeaways were that gender did not seem to matter much related to phishing susceptibility, and regarding repeat-clickers, 23.91% of those performing a dangerous action (enabling macros, submitting credentials), did it more than once. The research paper also showed that if an employee failed a phishing test and was sent voluntary training (i.e. the employee was not required to complete the training) that this does not work to improve security behavior.
Crowd-sourcing Turns Out To Be Feasible
As stated, employees in the tested company were given a 'Phish Alert' button in their email client to report suspicious messages. In terms of the effectiveness of crowd-sourcing of defending against phishing attacks, the researchers looked into both the reaction time and flagging accuracy of employees.
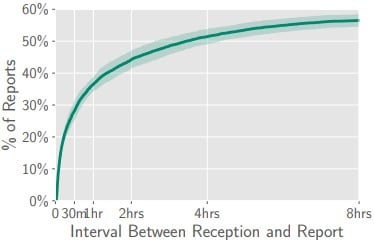
The user reports were accurate in 68% for phishing and 79% if spam is accounted for as well. The most active reporters reached an accuracy of over 80%. And here is an important point: the time for these reports to be submitted after reception was 5 minutes for 10% of the total volume and half an hour for 35% of the total number of reports.
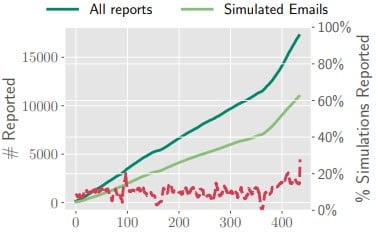
"To apply these numbers to a hypothetical company of 1,000 employees where 100 of them are targeted by a phishing campaign, we would have between 8 and 25 reports of the email by employees—of which one within 5 minutes with high probability, and a larger number within 30 minutes," details the paper.
In other words, in case of an active attack, the SOC would get a user-generated warning in 5 minutes and be able to PhishRIP the message immediately, or better yet, PhishFlip this attack into a simulated phishing attack for the whole user base.
Bleepingcomputer commented: "These findings show that utilizing a corporate-wide crowd-sourced phishing detection service [like PhishER] could significantly reduce the threat of phishing attacks. It is also important to note that such a system wouldn’t produce a sizable operational workload as a result, so a corporation implementing crowd sourced phishing protection wouldn’t incur much additional burden. Also, the researchers concluded that there is no "reporting fatigue," suggesting that crowd-sourcing anti-phishing data is feasible.
We like it when scientific studies confirm what we have been saying here for a while...