Ouroboros, one of the world’s most sophisticated hacking groups with close ties to the Russian government, has been accused of hijacking unencrypted commercial satellite communications. They use hidden receiving stations in Africa and the Middle East to hide their Control & Command servers and mask attacks on Western military and governmental networks.
The group which created the advanced malware known as “Snake” or “Turla” was exposed last year as having mounted aggressive cyber espionage operations against Ukraine and a host of other European and American government organizations over nearly a decade.
In a report by Kaspersky released on Wednesday, they said they had identified a new “exquisite” attack channel being used by the group that was virtually untraceable. The need for hackers to communicate regularly with machines they have compromised allows security researchers to trace back the hackers' Command & Control servers.
“This method makes it almost impossible to discover the physical location of these C&C servers,” said Stefan Tanase, senior security researcher at Kaspersky. “Safe to say this is the ultimate level of anonymity that any cyber espionage group has reached in terms of hiding its origins.” Here is the Video
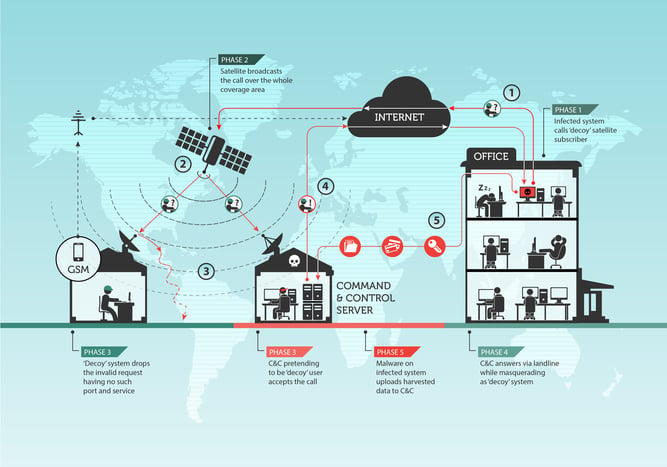
The Ouroboros satellite hack exploits the fact that most satellite communications being sent from satellites back to earth are unencrypted, and so can be spoofed. The process is laid out by Kaspersky in a large illustration and follows a number of steps.
First, the Ouroboros malware sends out a request for instructions. Normally such a request goes straight to a C&C server, and is traceable. Ouroboros instead sends the request to an unwitting decoy server, because the hackers have identified it as a satellite communications user.
The request from Ouroboros is then automatically routed via a commercial satellite and beamed to earth towards the location of the decoy. Once the decoy server receives the request for instructions, it discards it, because the request is meaningless to it.
But the satellite will have beamed the request over a large geographical area. A hidden receiver anywhere in the area, planted by Ouroboros’ operators, can then pick up the unencrypted request. The receiver then issues a reply to Ouroboros, disguised as a communication returning from the decoy.
This way, any defender looking to trace communications from Ouroboros back to its controllers will lose the trace from the point at which the data becomes a signal beamed from a satellite, effectively breaking any direct digital link.
Ouroboros’ handlers are using satellite operators in the Middle East and Africa. Finding the receivers depends on the size of the dish, but it's a needle in a haystack because the area could be tens of thousands of square kilometers.
“The receivers do not necessarily cost much themselves but finding a physical location for these indicates that there is some kind of extensive logistical support network,” Kaspersky said. Such operations point to a state intelligence service, he added.
For the moment, satellite operators are powerless to prevent the hackers from routing requests through their networks until they encrypt all of their downstream communications, which would cost hundreds of millions in new satellite arrays.
Western security officials have previously stated that Ouroboros is a Russian operation, a fact supported by the group’s targets and reverse engineering of the malware itself. What else is new for "once-a-spook-always-a-spook" Vladimir Putin.
Usually, foreign hackers infect target machines with spear-phishing attacks using public facing email addresses. Which of your email addresses are exposed on the Internet and are a target for phishing attacks? You can get a one-time no-charge Email Exposure Check (EEC) sent to you if you want to know how big your email attack surface is:





