Ewww. Something else to watch out for. Will it ever stop?. Ummm, no.
A new academic study published today reveals that Android-based password managers have a hard time distinguishing between legitimate and fake applications, leading to easy phishing scenarios.
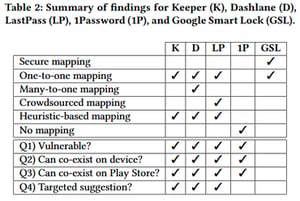
TL:DR - "Android versions of password managers from Keeper, Dashlane, LastPass, and 1Password were found to be vulnerable and have prompted the user to auto-fill credentials on fake apps during tests. Researchers found that Google's Smart Lock app did not fall for this fake package name trick, and the reason was because it used a system named Digital Asset Links to authenticate and connect apps to a particular online service."
The study looked at how password managers work on modern versions of the Android OS, and which of the OS features attackers can abuse to collect user credentials via phishing attacks carried out via fake, lookalike apps.
What the research team found was that password managers, initially developed for desktop browsers, aren't as secure as their desktop versions.
The problem comes from the fact that mobile password managers have a hard time associating a user's stored website credentials with a mobile application and then creating a link between that website and an official app.
Most password managers use an Android app's package name to establish a connection to a real-world website URL, and then associate the user's credentials for that website with a mobile app.
But within the Android ecosystem, package names cannot be trusted, as they can be faked by a malicious actor quite easily. This leads to situations where a malicious app can trick a mobile password manager into associating it with a legitimate website.
For example, when a user opens a malicious app and the app prompts for login credentials, password managers that get tricked by the fake app package name will suggest login credentials for a legitimate service, allowing the fake app to collect the user's username and password for later (ab)use.
In the image above, the fake app uses a generic UI, but in the real world, attackers would almost certainly use apps that are near identical clones of legitimate apps, at a pixel level accuracy.
Even if a user might have suspicious about an app's authenticity, when a trusted password manager suggests to auto-fill login credentials, this might be the final piece that may sometimes push users into thinking the fake app is, in fact, real, when it is not. Full story with more data at ZDNet.




