...they can still be helping the bad guys compromise your organization. Sad but true.
One of the points we’ve made in a  number of our blog posts over the past few years is that the bad guys are always learning. And one of the ways they learn how to phish your organization successfully is by interacting with your employees — drawing them into back-and-forth email exchanges in which your users are unwittingly training malicious actors how to attack the organization.
number of our blog posts over the past few years is that the bad guys are always learning. And one of the ways they learn how to phish your organization successfully is by interacting with your employees — drawing them into back-and-forth email exchanges in which your users are unwittingly training malicious actors how to attack the organization.
Here’s the key: even if your users don’t ultimately take the bait and click on a malicious link or attachment in any one particular phishing email, they can still do damage to your organization’s security posture if they engage with the malicious actors behind that email.
We were reminded of this hard lesson by a customer whose HR and Payroll department recently dealt with a rather well-executed payroll phish. Payroll or direct deposit phishing attacks are prolific these days. Why did payroll phishing become so big and so dangerous? Because that’s where the money is.
This customer, which is in the health care industry, found the experience of dealing with this phish eye-opening. So much so, in fact, that the company emailed its employees an incredibly useful summary of the lessons learned. Here it is.
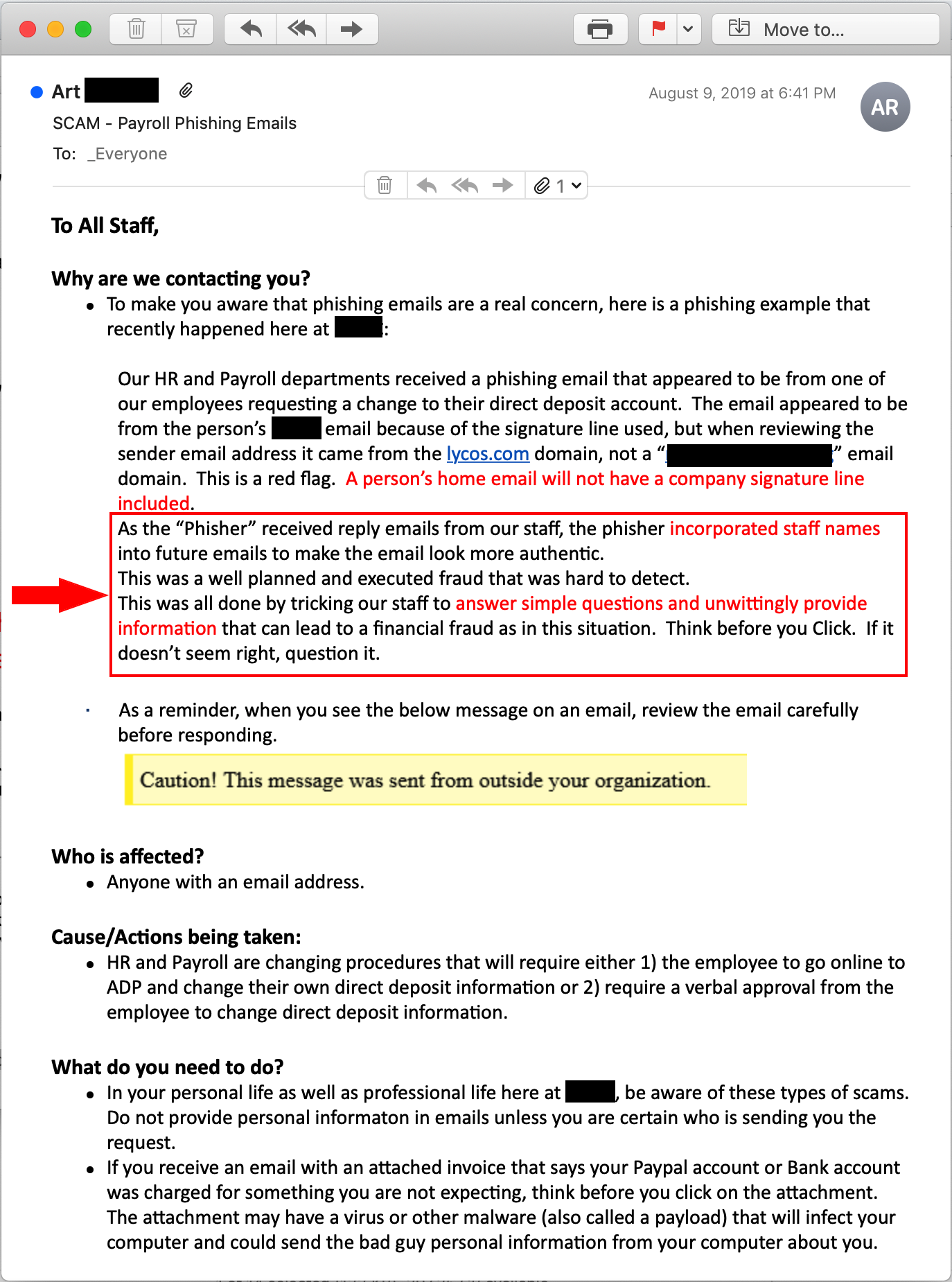
One of those key takeaways is worth repeating:
As the 'Phisher' received reply emails from our staff, the phisher incorporated staff names into future emails to make the email look more authentic...This was all done by tricking our staff to answer simple questions and unwittingly provide information that can lead to a financial fraud as in this situation.
Even simple email conversations that seem innocuous and routine can provide malicious actors with information that can be weaponized and used against your organization.
Think before you click. Know who you’re talking with. If an email exchange you’re engaged in seems odd or suspicious, stop — and notify your manager or the IT department.
Loose lips really can sink corporate ships.




