On May 7, executives of Equifax submitted a "statement for the record" to the Securities and Exchange Commission detailing the extent of the consumer data breach the company first reported on September 7, 2017. The data in the statement, which has also been shared with congressional committees investigating the breach, reveals to a fuller extent how much personal data was exposed in the breach.
Millions of driver's license numbers, phone numbers, and email addresses were also exposed in connection with names, dates of birth, and Social Security numbers—offering a gold mine of data for identity thieves and fraudsters.
Equifax had already reported that the names, Social Security numbers, and dates of birth of 143 million US consumers had been exposed, along with driver's license numbers "in some instances," in addition to the credit card numbers of 209,000 individuals. The company's management had also reported "certain dispute documents" submitted by about 182,000 consumers contesting credit reports had been exposed as well, in addition to some information about British and Canadian consumers.
Equifax felt it did not have a legal obligation to disclose those details
But the exact details of the nature of these documents and information had not been revealed, in part because Equifax felt it did not have a legal obligation to disclose those details. "With respect to the data elements of gender, phone number, and email addresses, US state data breach notification laws generally do not require notification to consumers when these data elements are compromised, particularly when an email address is not stolen in combination with further credentials that would permit access," Equifax's management asserted in the SEC letter.
Of the 146.6 million individuals affected by the breach:
- 145.5 million had Social Security numbers exposed.
- 99 million had address information exposed.
- 27.3 million had gender information exposed.
- 20.3 million had phone numbers exposed.
- 17.6 million had driver's license numbers exposed.
- 1.8 million had email addresses exposed.
- 209,000 had credit card numbers exposed.
- 97,500 had Tax Identification numbers exposed.
- 27,000 had the state of their driver's license exposed.
In addition, Equifax provided more detail about the "dispute documents" that were stolen in the breach. These were personal identity documents uploaded as images to Equifax:
- 38,000 driver's licenses
- 12,000 Social Security and Taxpayer ID cards
- 3,200 passports and passport cards
- 3,000 other documents, including military and state IDs and resident alien cards.
The stolen data did not come from a single, centralized database but from a collection of disparate databases associated with Equifax's Web applications and payment systems.
This dumpster fire (more like an underground coal fire if you ask me) is still burning. Full story with more detail at Arstechnica.
What is your organization's actual social engineering attack surface?
When data is breached at this scale, it's probably a good idea to check how vulnerable your organization may be to social engineering, spear phishing and ransomware attacks.
Our NEW Email Exposure Check Pro goes even further to identify the at-risk users in your organization by crawling business social media information and scouring hundreds of breach databases, many of them in the Dark Web. This is done in two stages: 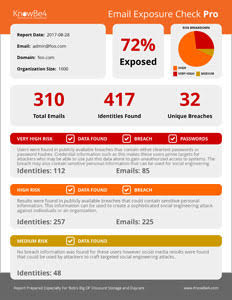 First Stage: Does deep web searches to find any publicly available organizational data. This will show you what your organizational structure looks like to an attacker, which they can use to craft targeted spear phishing attacks.
First Stage: Does deep web searches to find any publicly available organizational data. This will show you what your organizational structure looks like to an attacker, which they can use to craft targeted spear phishing attacks.
Second Stage: Finds any users that have had their account information exposed in any of several hundred breaches, using Have I Been Pwned. These users are particularly at-risk because an attacker knows more about that user, up to and including their actual passwords!
Your EEC Pro Reports: We will email you back a summary report PDF of the number of exposed emails, identities and risk levels found. You will also get a link to the full detailed report of actual users found, including breach name and if a password was exposed.
This is so important that even if you already ran your one-time no-charge legacy EEC, you are eligible to try the new Pro version. Run your complimentary one-time Email Exposure Check Pro here. Results come back in a few minutes:
PS: Don't like to click on redirected buttons? Copy/Paste this in your browser:
https://info.knowbe4.com/email-exposure-check-pro-chn





