
Bradley Barth at SCMedia nailed it when he wrote: "No, NSA whistleblower and U.S. fugitive Edward Snowden did not just purchase a 2 terabyte storage plan for iCloud, nor has he moved back to the States.
"Instead, a strange spam campaign that targets Apple customers has been found distributing phishing emails containing an Apple receipt that bills $9.99 to an Edward Snowden residing at a U.S. address.
"In a Feb. 13 blog post, Malwarebytes reported that these Snowden emails, the contents of which have slightly varied, were observed from Feb. 2-6 of this year. URL shortening service provider PixelMe ultimately blocked the link found within the emails, but it is unclear what the link's original intended destination was.
"The general rule of thumb is to try and be as inconspicuous as possible, so we're not really sure why the scammers went with one of the most well-known privacy advocates on the planet to fill in the personal information box," wrote Chris Boyd, blog author and lead malware intelligence analyst.
On the other hand, if it really is Snowden, it appears he's made a nice life himself -- considering that, according to Boyd, the randomly-grabbed address listed in the spam emails is "from a property website sporting nine bedrooms and four bathrooms."
The same Malwarebytes blog post also references three other recent Apple-themed phishing scams attempting to trick recipients into clicking on malicious links. One involves a fake notification informing recipients that someone is logging into their Apple account using an iPod in Monaco.
Another is a smishing scam featuring texts, purportedly from Apple Care, warning recipients that their Apple ID is about to expire. And a third scam was reported by a Twitter user, who received a fake iTunes Store email citing an order ID number that was an actual valid number from a previous purchase the recipient had made."
Major brands are misused by the bad guys literally all day long, using them for social engineering tactics to manipulate the end-user into clicking a link or opening an infected attachment.
There are dedicated companies like BrandProtect and PhishLabs that make it their life's work to take down criminal sites that violate brand copyrights. The problem is that this is often too late. The average phishing site lives for 6 hours. And guess what the average update time for antivirus definitions is? You got it: 6 hours. That's no coincidence, the bad guys get in the air, send a zillion phishing emails and shut down 6 hours later. If you rely on antivirus to keep your end-users safe, you have a false sense of security.
SEE RELATED: Bad News: Your Antivirus Detection Rates Have Dramatically Declined In 12 Months
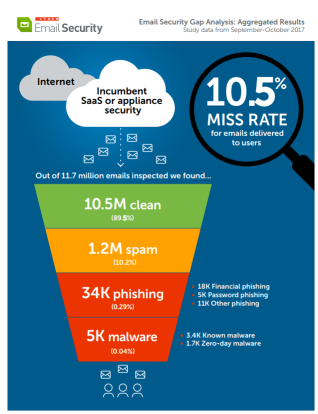
You need to create a human firewall as your last line of defense, when malicious emails make it through all the filters, which happens more than you and I would like to see. About 10.5% makes it through, consistently, so you need to create a security culture in your organization. (Image: Cyren)
Creating a better security culture in your organization has a few challenges. Let's have a look at them, see how you can overcome some, and turn a few others around into your advantage. The ultimate goal is your organization being such a hard target that the bad guys just get discouraged and move on.
Of course, every organization has an existing security culture. If they say they don't, they probably are reluctant to admit they have a bad security culture. Corporate culture in general could be called the combination of all technology, knowledge, morals and even wisdom afloat in your organization.
Ever heard the statement about the difference between morals and ethics? Morals is what you do when other people are watching. Ethics is what you do when no one is watching.
You could define "Security Culture" as what happens with security when people are not being watched, are they making smart security decisions? And how do you measure it?
OK, so how do we get there?
By first having a look at the current state of affairs and see where we need to start. Here are the 5 main issues:
- Employees are not easy to train in secure behavior. They have been living their online lives for a long time, and "making smart security decisions" has not been their modus operandi. They need to be trained out of bad habits.
- Organizations do not realize the scale of the social engineering threat. Your board, C-levels, and the general employee population simply have not been aware of the massive increase of cybercrime and their tactics. Security culture is only starting to catch up with the threat landscape.
- There is no budget set aside and not enough resources allocated. It's the logical result of not realizing the threat in point 2.
- Changing a culture requires a lot of (internal) marketing and PR. Those are not areas that IT pros are trained in themselves. Creating a multi-disciplinary team that covers these skill sets is a must, but hard to do.
- Creating and maintaining an intentional Security Culture takes buy-in and work at all levels of the organization. Culture is less about words and more about actions. Creating and sustaining the culture that you want is an ongoing, intentional process. The desired cultural tones, standards, and practices must be set, modeled and evangelized at the leadership level, as well as middle-management and by influential individual contributors. Culture is set by social norms and social pressures; our job is to help shape and sustain them.
Because of this, it is crucial to ensure that there is buy-in for each security-related value that you want to cultivate. Part of this can be accomplished and sustained through the creation of a security champion/liaison program that is intended to be an open line of mutual communication and support between key security stakeholders and other lines throughout the organization.
This not only helps disseminate security-related information, but is also a mechanism for creating open dialog related to security concerns, misunderstandings, and so on. Key to this concept is having membership from the executive team, middle-management, and influential and knowledgeable individual contributors -- creating cultural reinforcement points at all levels of the organization.
So, How To Create A Security Culture?
IT pros don’t exactly know where to start when it comes to creating a security awareness program that will work for their organization. We’ve taken away all the guesswork with our new Automated Security Awareness Program (ASAP).
Includes:
- 15-25 questions depending upon answers
- Suggested training materials based on answers
- Choose and change your program start date and tasks
- Calendar and list view of tasks
- Dashboard with program status, % complete, tasks overdue, etc.
- Detailed and summary exportable PDF versions of your program
- Fully mature awareness program ready in 10 minutes
If you do not have a KnowBe4 account yet, (free or paid) find out what YOUR program will look like. There is no cost… Start ASAP!
Don't like to click on redirected buttons? Cut & paste this link in your browser:
PS: If you’re a current KnowBe4 customer, just login to your console, click on ASAP at the top right and get started!





