 Details around the recent successful ransomware attack on fashion retailer FatFace provide some insight into what you should expect when you become a victim.
Details around the recent successful ransomware attack on fashion retailer FatFace provide some insight into what you should expect when you become a victim.
If you’ve paid attention to news stories about organizations hit by ransomware, the topic of paying the ransom inevitably comes up. But a recent story about how FatFace was hit by the Conti ransomware gang provided some first-hand details that I found fascinating.
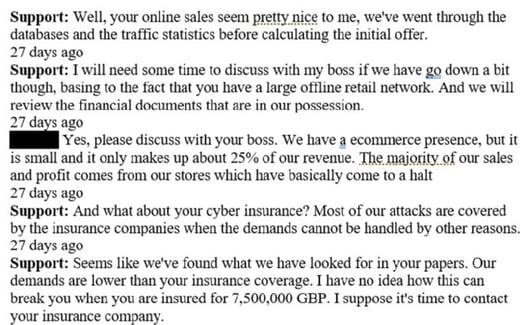
According to the story over at Computer Weekly, the discussion about the ransom amount started at around $8 million. From the negotiation logs (shown below), the cybercriminals didn’t just come up with that number randomly. They looked through FatFace’s databases, and website traffic statistics to come up with their initial ask.
Source: Computer Weekly
What is equally fascinating is that when FatFace pushed back, Conti did some additional digging through the data they exfiltrated to find the cyber insurance policy in place and its’ coverage amount.

Source: Computer Weekly
Ultimately, upon further negotiation, FatFace was able to reduce the ransom amount to $2.65 million.
I was happy to see that as part of their remediation steps to shore up security, FatFace included phishing testing (which is the feedback loop for Security Awareness Training to let the organization know which users need more training), as the combination of the two are extremely effective in reducing the end-user’s portion of the threat surface.
Read the full article over at Computer Weekly.
 Here's how it works:
Here's how it works:




