 Leveraging a legitimate feature of Dynamics 365, threat actors are able to obfuscate the malicious nature of the email within content that naturally requires user interaction.
Leveraging a legitimate feature of Dynamics 365, threat actors are able to obfuscate the malicious nature of the email within content that naturally requires user interaction.
It’s been called the “static expressway” – the use of legitimate sites to bypass security scanners that would, otherwise, spot the malicious nature of the phishing emails. We’ve seen this before in attacks using Paypal invoices, for example. In this latest attack documented by security analysts at Avanan, threat actors are using a survey feature within Dynamics 365 normally used to gain feedback from customers.
Instead, threat actors are sending bogus voicemails with links to play the voicemails that send victims to credential harvesting logon pages impersonating the Microsoft 365 platform. In some cases, legitimate Customer Voice links are also embedded for additional credibility with security scanners.
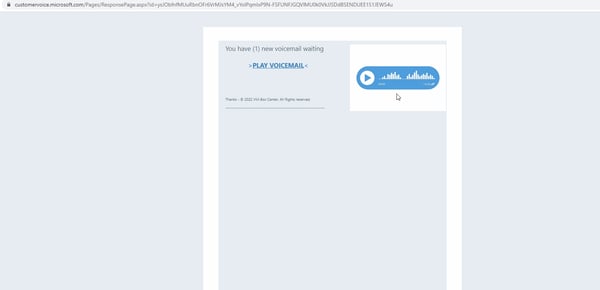
Source: Avanan
The challenge here for security solutions is that many solutions see a known-good link from a legitimate platform and don’t scan it (which, of course, does not help the situation). So you're not going to be able to rely solely on your security solutions to stop these kinds of attacks. Instead, it’s up to the recipient user to be vigilant – something taught to those that undergo continual Security Awareness Training – when receiving emails that are unexpected, or look even the slightest bit off or out of place.
 Here's how it works:
Here's how it works:




