 Every person and organization is different and requires slightly different methods and ways of learning. But every person and organization can benefit by more frequent security awareness training (SAT).
Every person and organization is different and requires slightly different methods and ways of learning. But every person and organization can benefit by more frequent security awareness training (SAT).
Most organizations do not do enough. Training and testing once a year certainly is not that helpful. How often should you do SAT to get the biggest decrease in cybersecurity risk? At least once a month, if not more. But a sophisticated SAT program includes a combination of methods and tools. We will share one recommended, “dream team” training and testing schedule here.
Training When Hired
Whenever anyone is hired, they should be provided more extensive SAT. It should cover a bunch of topics, give a lot of examples of popular social engineering and phishing scams, and include some quizzes. This training should be 15-45 minutes long. Then every year, give a long SAT training session, but do not use the same content as before. The training doesn’t have to be on January 1st, and probably shouldn’t be, as most organizations are busy preparing for the new year. But most organizations probably do offer/require the longer training in January or the first quarter of each year.
Annual SAT Party
Every year, you should have an SAT party where everyone is invited to a meeting, in person or remotely, where the focus is on defeating social engineering and phishing. It should open up with a supportive speech by the CEO or some other senior executive. You want the organization to know that your SAT program is important to the goals and achievements of the organization and supported from the very top.
It should have door prizes, quiz prizes, and lots of company swag. You should have a dozen or two SAT- or organization-related quiz questions where you hand out prizes to the first person who answers correctly. Have some grand prizes, gift cards, and goofy gifts. Have food, drink, and dessert. Some of the best parties, when allowed, have alcoholic beverages. The mood should be festive, fun, and drive home the importance of fighting social engineering and phishing across the organization.
Monthly Training
Every employee should have shorter monthly training. These training sessions should last from one to five minutes and focus on topics that are currently happening and likely to target the organization. This training doesn’t have to be on the first of the month, and for some organizations, shouldn’t be. But it should be monthly.
Simulated Phishing
Simulated phishing campaigns should be done at least once per month. Every two weeks or every week is even better. The data from 11 years and over 65,000 customer organizations shows that the more frequently you do training and simulated phishing, the better your co-workers get at spotting simulated and real phishing attacks. Once a week may be too much for some organizations. We get that. Simulated phishing tests should be done no less than once a month, and more if possible. People who “fail” simulated phishing tests should have to take more education and get more simulated phishing tests.
There is strong evidence to show that simulated phishing tests are better than even formal training education at helping employees avoid falling victim to social engineering and phishing. If you skip or skimp on simulated phishing tests, you are doing a disservice to your co-workers.
Drills
At least once a year, and possibly more, choose a monthly exercise that helps people spot real-world phishing attacks. But instead of it being a single simulated phishing test, make it a bunch of simulated phishing examples, which drill and quiz the user into the good actions you want them to perform when evaluating real suspected phishing emails and messages.
Note: One of our most popular content offerings is ‘Spot the Phish Reloaded’, which is a great drill.
Employee Share
You should have an employee share their real-world phishing experience and how they avoided being a victim or how they were tricked and what subsequently happened. Nothing speaks better to co-workers than seeing another co-worker and learning from their close-to-home experiences.
Champion Programs
In that same vein, some of the most successful SAT programs have “champion programs”, where selected groups of people who have experience with social engineering and phishing, and are good at defeating it, share and help others. Many times, these champion programs will have interesting names, logos, meetings, and swag to earn and hand out.
Training Content
Content should be a mix of types, including videos, newsletters, quizzes, and games. Training should be knowledgeable and fun, and repetitive. You know your favorite commercial? Yeah, it is repeated dozens of times a day. Sometimes back-to-back, twice-in-a-row. Why? Because marketers know that repetition gives messaging staying power. Do the same with your SAT. We have a saying, “Test like an attacker, train like a marketer!”
Goals
Your overall goal is to lower cybersecurity risk to your organization from social engineering and phishing. You want your co-workers to be able to spot social engineering and phishing attempts and know how to mitigate and appropriately report them. Focus on those three goals and your SAT program will be a winner for the organization.
Be Flexible
Let your SAT program change as the results dictate. If you get too many complaints, back down on the frequency or change up the content and methods. Use what is working and get rid of what is not.
Below is an example SAT program with methods and cadence.
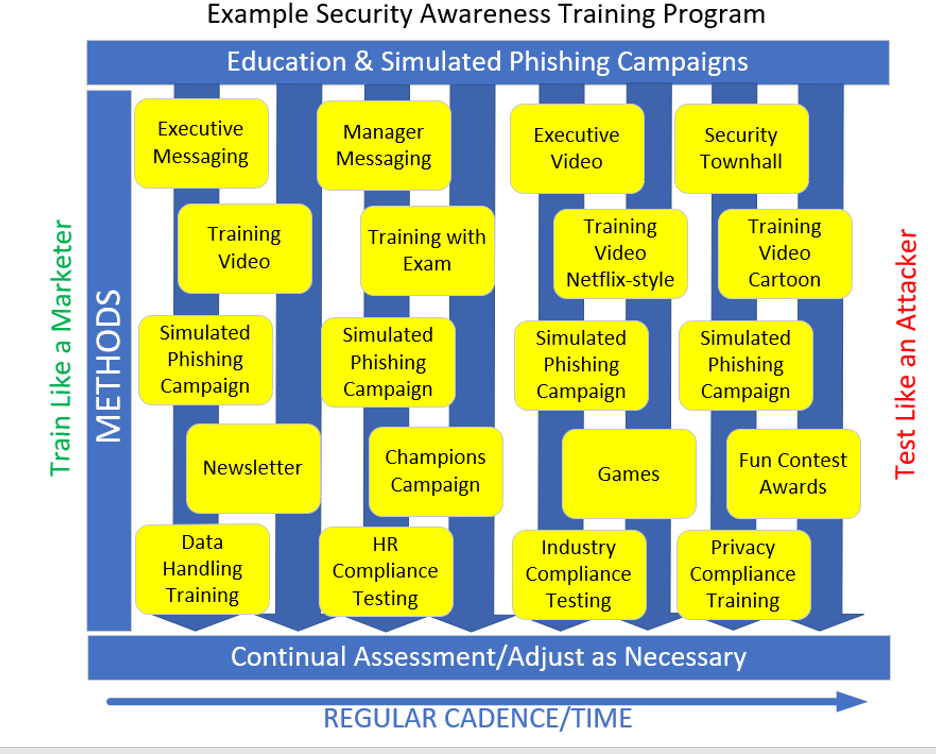
Many organizations, without full senior management support, simply will not be able to do this “dream team” SAT program. But if you can get your program somewhere near it, you will reap the best benefits and make an organizational culture that best decreases the risk from social engineering and phishing.
 The ModStore Preview includes:
The ModStore Preview includes:




