By Eric Howes, KnowBe4 Principal Lab Researcher. Over the past week we spotted something new and interesting in the malicious emails being reported to us by customers using the Phish Alert Button (PAB): a two-part phish in which users are hit with a sequence of two coordinated emails. The first email prepares users for the second, which contains a malicious link that usually leads to a credentials phish.
How It Works
In the initial email -- usually sent from the compromised email account of someone known to the potential victim -- users are told to expect a followup email containing important information that may wind up in their Junk folders.
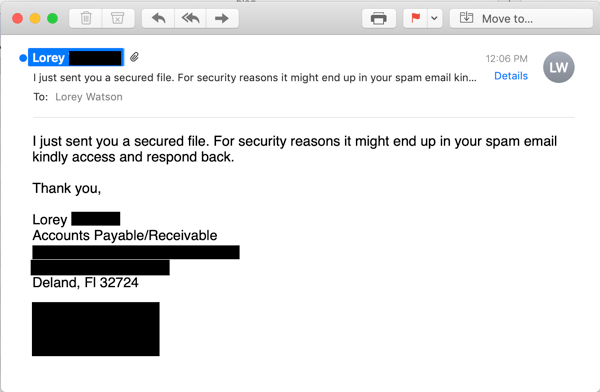
This initial email will often -- but not always -- carry one of these Subject: lines:
- "Check your junk for the attached file"
- "kindly check you received this email in your inbox/junk"
- "I just sent you a secured file. For security reasons it might end up in your spam email kindly access and respond back"
The second, followup email -- sent from the same compromised account as the first but using a different Subject: line -- is a standard phishing email using some of the latest social engineering techniques that we have documented in earlier blog posts.
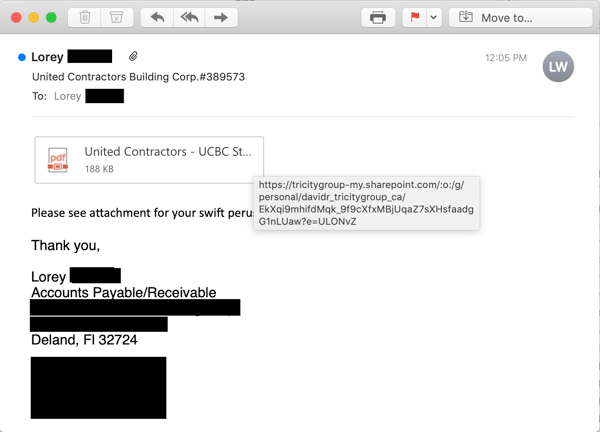
Note the use of a fake attachment graphic often seen in malicious emails of this sort.
Like all the other examples we've seen, this second email contains a link to a file hosted on a legitimate, well-known web site or service -- an increasingly common practice among malicious actors looking to leverage the trust users tend to afford these high profile branded sites and services.
In this example, the link in the followup email points to a file on Microsoft Sharepoint...

...which in turn contains yet another link taking users to a slickly designed web page on SurveyGizmo...
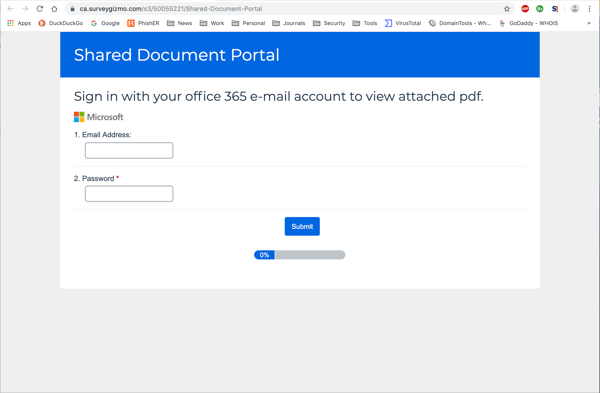
...which turns out to be a credentials phish.
It's worth calling attention to the level of care exercised by the bad guys here, who ensured that the branding experience encountered by potential marks would be consistent -- even to the point of designing a Microsoft-branded landing page on SurveyGizmo, surmising (probably correctly) that most users would not notice the disjunction between the branded web page and the site hosting it.
Why They Do it
We suspect the bad guys are experimenting with this approach in order to combat a persistent, nagging problem with run-of-the-mill spam filters. Just as retail web sites now resort to commercial services to resurrect abandoned shopping carts and prod users to complete their purchases, the bad guys are now turning to ordinary users themselves to rescue their malicious emails from digital purgatory in Outlook's Junk folder.
Even in those instances where the second email does not, in fact, end up in the user's Junk folder, the bad guys might still find this two-fer phishing technique useful, as it prepares the user for second malicious email, encouraging them to locate it and engage with it. Additionally, the initial email adds an element of the "human" to this sequence of emails -- potentially lending credibility to the second email, which would otherwise land with a cold thud in the user's inbox.
Does It Work?
Although we've encountered only comparatively small numbers of phishing attacks using this approach, we've already seen evidence that the bad guys may be getting some traction with it.
Consider this second example, which leads off with a rather short, to-the-point announcement of a followup email that the recipient should be anticipating.
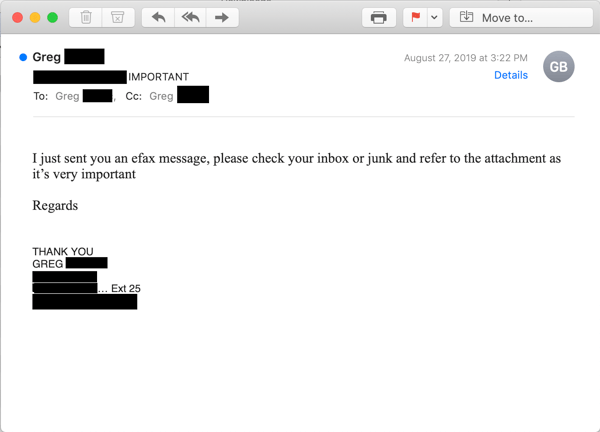
Like our earlier example, the followup email hails from the same compromised email account as the first...
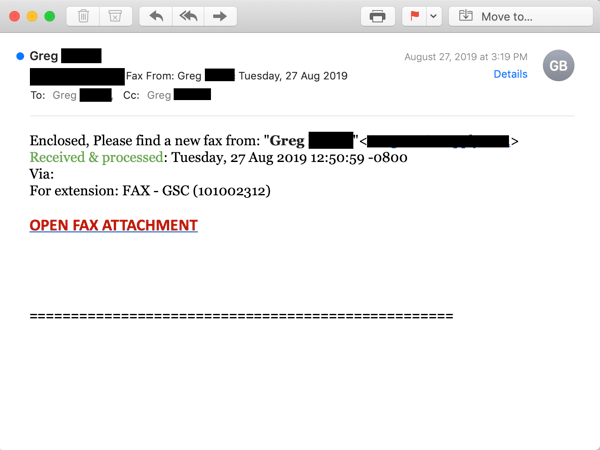
..and contains a link pointing to a file or web page hosted on a trusted online service -- OneDrive, in this case.
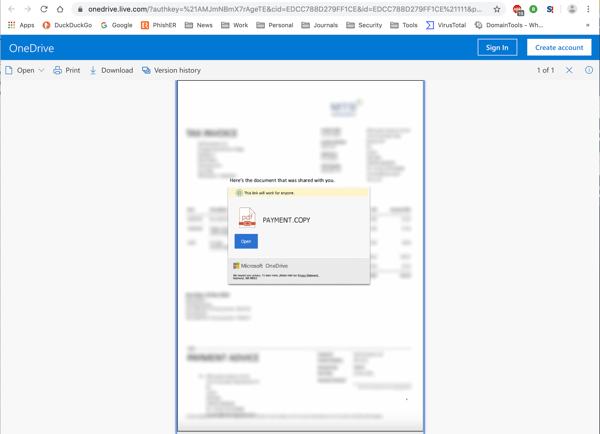
As before, the landing page is professionally designed and seamlessly preserves the Microsoft branding experience with a spoofed OneDrive web page hosted on OneDrive itself.
In this case, however, the user encountered problems following the malicious link contained in the spoofed page on OneDrive.
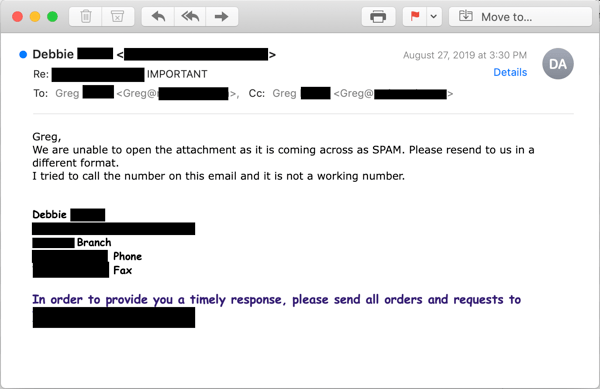
We do not know what stopped the user from accessing that final link to the actual malicious content. Perhaps the user's endpoint AV blocked the link, which points to yet another non-Microsoft web site. Alternately, she might have found that external web page had been taken down when she clicked the link to it (indeed, it was gone by the time we checked).
Whatever the case, the user here was obviously committed to gaining access to a file she was convinced was legitimate -- even after calling the phone number of the alleged sender and finding it to be a non-working number. (One wonders how many more clues this user needed!)
Ultimately, only time will tell whether the bad guys enjoy enough success with this approach that it becomes more common -- and begins attracting copy-cats from other malicious groups operating in the same space.
The Upside
Although the bad guys may be getting some traction with this social engineering technique, there is an upside for the good guys: that initial email is a massive red flag. Simply put, any email that warns recipients that a followup email will be coming and may need to be fished out of the Junk folder ought to be treated with a great deal of suspicion.
Here's the catch, though. Although some of your users will be naturally skeptical of that initial email, there will be plenty who are not. Buried in their work and firmly on auto-pilot, many users will succumb to a form of tunnel vision -- seeing only one more minor thing to add to an already long list of tasks to be finished before the end of the day. Some may even appreciate being given a helpful heads-up to an email they might have otherwise missed (and may ultimately wish they had).
In other words, your users need New-school Security Awareness Training, which teaches them what to look for and encourages them to be cautious and skeptical when handling incoming emails -- even those that appear to arrive from individuals they recognize and that purport to take them to sites they know and trust.
 Here's how it works:
Here's how it works:




