 When you think of cyber-espionage, you might be surprised it’s far less “Mission: Impossible” and a lot more basic phishing tactics.
When you think of cyber-espionage, you might be surprised it’s far less “Mission: Impossible” and a lot more basic phishing tactics.
A North Korean developer has been formerly charged by the US Department of Justice for his role in cyber-attacks backed by the North Korean government. The group responsible for attacks such as the one on Sony back in 2014 in response to the movie The Interview, and the 2016 theft of $81 Million from Bangladesh Bank, included the developer.
According to the FBI, the group has targeted a wide range of businesses and industries, with damages estimated to be in the billions.
So, how did they do it? Fancy gadgets and masks? Fast cars and tuxedos?
Nope – just good old-fashioned spear phishing.
According to the FBI, the group spent time researching their victim company and its employees. Messages were then sent via email or social media to employees in an attempt to compromise endpoints with malware. For example, emails were sent purporting to come from Facebook or Google, in the hopes the employee would open them on their work computer. In other instances, they went as far as to compromise company A, create email accounts posing as recruiters, and then sent recruitment messages to company B (their intended target).
In both the case of Sony and the Bangladesh Bank, the same social engineering methods were used in conjunction with spear phishing email.
A user’s willingness to naively click a link can literally result in millions of dollars in damages. If you believe that malicious emails can make it past your security infrastructure – even just one – you need to educate your users via Security Awareness Training about the dangers of phishing, social engineering, malicious links, and how to avoid becoming a victim. It could save the organization its’ reputation, wallet, and livelihood.
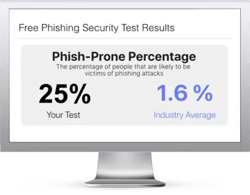
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
Would your users fall for phishing attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
 Here's how it works:
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/phishing-security-test-offer





