 In the last few months, law enforcement has warned repeatedly about a new scam that is rapidly expanding. The FBI calls it "Business Email Compromise" (BEC), but it is better known as "CEO Fraud."
In the last few months, law enforcement has warned repeatedly about a new scam that is rapidly expanding. The FBI calls it "Business Email Compromise" (BEC), but it is better known as "CEO Fraud." Now Symantec sounds the alert. They have a service called Email Security Cloud and they see these types of spoofed CEO emails trending up.
"BEC attackers target senior-level employees rather than consumers as it’s easier to scam them out of large amounts. In one incident, we observed the scammers asking the target to transfer over US$370,000. By requesting large amounts of money, the scammers only need to be successful a couple of times to make a profit," Symantec researchers explained.
They continued with: "The FBI estimates that the amount lost to BEC between October 2013 and August 2015 was over $1.2 billion. With such huge returns, it’s unlikely that these scams will cease any time soon."
C-level employees, especially CEOs and CFOs, have to be aware of the various techniques the scammers are using to trick them into wiring out large amounts of money. We have warned about this before.
Crafting The Email
BEC emails typically have the same format, the email poses as a message from the targeted company’s CEO. This is done using one or more of the following methods:
- Compromising the CEO’s email account
- Spoofing the CEO’s email address
- Using a form of typo-squatting where the email address uses a domain which resembles the targeted company’s actual domain (e.g. myydomain.com vs mydomain.com). These domains are often registered on the same day that the email is sent.
The scammers use a few simple tricks to try and avoid arousing suspicion. The emails often state how the CEO is traveling or is in a meeting and can’t accept phone calls. Many of the emails have "sent from my iPad" appended, to suggest the sender is on the road or excuse typos in the message.
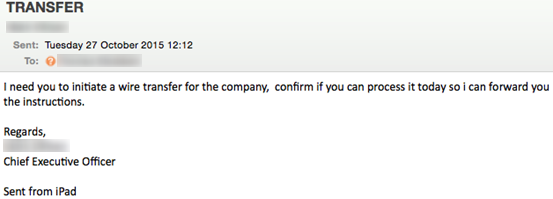
The scammers know their targets: the names and email addresses of executives can often be found on the company website or on LinkedIn. Sometimes the emails will be short and simple ("I need you to initiate a wire transfer for the
company, confirm if you can process it today so I can forward you the instructions", signed with the name of the CEO).
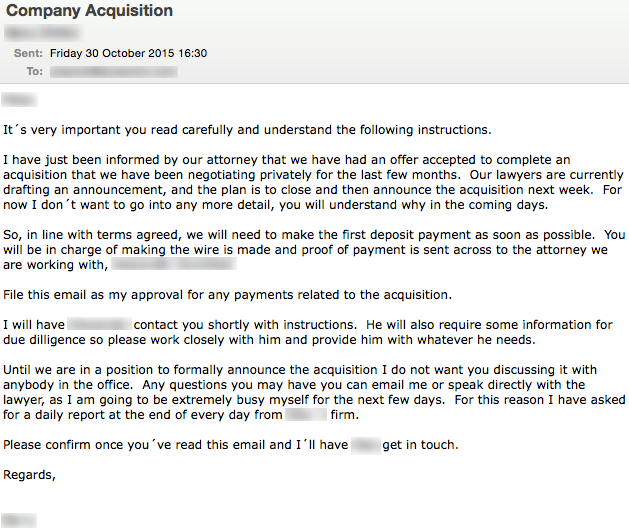
But sometimes they are much longer and sophisticated.
What To Do About It
Symantec stated: "User education is the most effective means of protecting companies against BEC scams". We could not agree more. Here are a few hints and tips you can send to your Accounting department, and cc your CEO while you are at it.
- Double-check any emails that request actions which seem unusual or aren’t following normal procedures. Make it OK to "query" wire transfers higher than a secret agreed-upon amount.
- Verify the email via a different medium, for instance the phone or fax.
- Use two-factor and/or two-person authentication to make wire transfers.
- Grab this updated version of our Social Engineering Red Flags PDF, print and laminate it, and give it to everyone. (There is no charge)
If you believe you have been a victim of CEO Fraud, notify your financial institution as fast as possible (24 hours is already on the late side to try to claw back wire transfers) and report the fraud with your local law enforcement agency for later insurance and legal procedures. Remember that "ounce of prevention"; find out how affordable security awareness training is for your organization and be pleasantly surprised.





