CyberheistNews Vol 7 #03
Bad News: Your Antivirus Detection Rates Have Dramatically Declined in 12 Months 
We all had the nagging suspicion that antivirus is not cutting it anymore, but the following numbers confirm your intution. I have not seen more powerful ammo for IT security budget to transform your employees into an effective "last line of defense": a human firewall.
I have covered Virus Bulletin here many times, and have kept track over the years since this is the industry I lived in for 10 years before KnowBe4, and why I started this company in 2010.
Virus Bulletin (VB) is the AV industry's premier "insider site", and shows how good/bad endpoint detection rates are, but VB also covers spam filters, and tests them on a regular basis.
Both antivirus (aka endpoint protection) and spam filter tests are published in quadrants graphing the results. What most people do not know, is that participants in this industry all share the same samples, and it's often just a matter of who gets the definition out first, because soon enough everyone else has that malware sample and blocks the hash.
Well, there is bad news: your proactive antivirus detection rates have dramatically declined in 12 months.
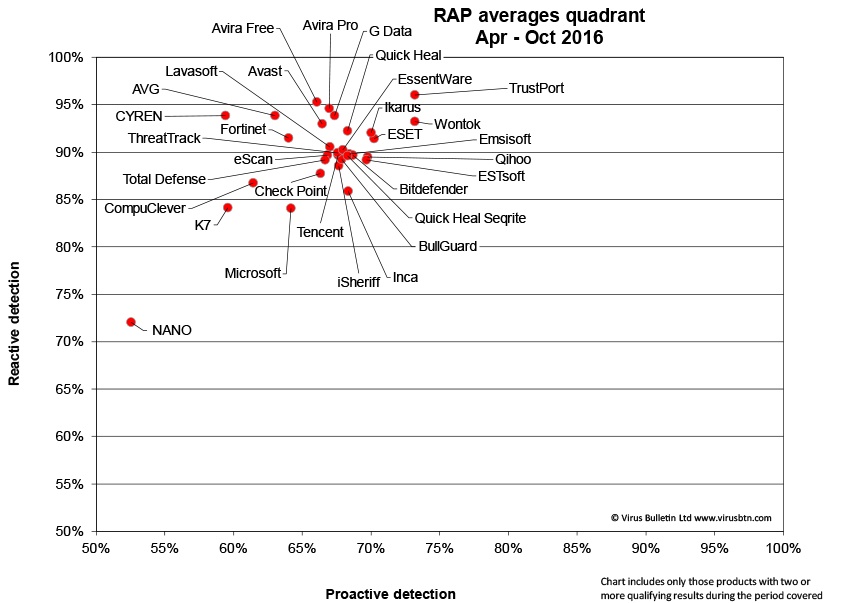
Don't take my word for it. Just look at the quadrants for Jun-Dec 2015 and compare it to the most recent one for 2016. Note the fact that in 2015, the proactive detection is a bit spread out, but the midpoint hovers around 80%, and the reactive midpoint sits at roughly 90-95%. (Reactive means they know this sample, have a hash, and can block it, Proactive means this is an unknown sample and the security software's heuristics need to recognize the malware behavior.)

Next, look at the same midpoints a year later for April-Oct 2016.
The bad guys are winning
Note that reactive detection dropped a little bit and now clusters on the 90% line, but if you eyeball proactive detection, it has dramatically dropped to 67-70%. You would expect that with modern machine-learning techniques, proactive protection would improve, but it is going the opposite direction. By the way, if your AV is not here, the vendor declined to participate, and you can draw your own conclusions about why.
Now you might think that if AV does not catch it, your spam filter will. Think again.
Martijn Grooten at VB commented on VB's most recent spam filter test that ransomware would be much worse if it wasn't for email security solutions: "Many experts believe that ransomware is set to become an even worse problem in 2017 than it was in 2016 — which is rather bad news, given the damage it has already done.
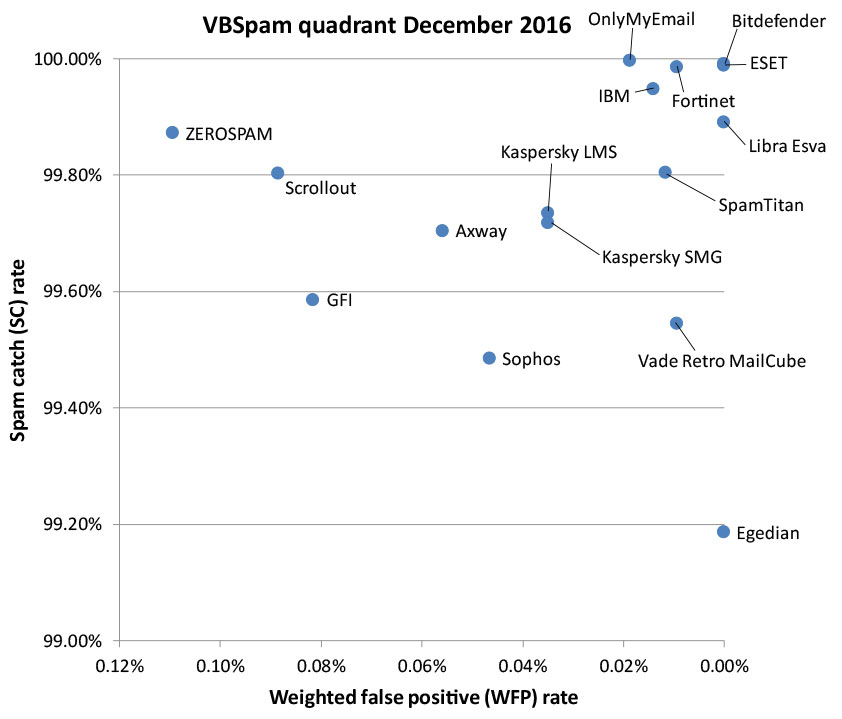
"Still, the problem could be much worse: a test of security products performed by Virus Bulletin in November/December 2016 showed that at least 199 out of every 200 emails with a malicious attachment were blocked by email security solutions (or spam filters). Of course, the fact that spam is sent out in large volumes means that even a very low success rate is sufficient for attackers to make a good return on investment — and thus to cause a lot of damage." Here is the quadrant for spam filters:
Now, let's have a look at that number of 1 in 200 making it through.
Statistics, extrapolations and counting by the Radicati Group from February 2015, estimate the number of email users worldwide was 2.6 billion, and the amount of emails sent per day (in 2015) to be around 205 billion. That is likely higher now. DMR offers these other fascinating statistics on email, compiled in August 2015:
That puts the potential for malware making it in your users' inbox into the millions... every day
And that is just looking at malicious attachments, of which these days 93% are ransomware.
Keep in mind that the bad guys are also very active with CEO Fraud using a spoofed "From" email address, and even more important, the most vicious attacks (like the hacks into the Clinton campaign) were based on a simple social engineering spear phish.
The above makes a very strong case for a brand new look at your last line of defense, your users.
It makes all the sense in the world to transform them into a human firewall ASAP, and keep them on their toes with security top of mind. Step them through new-school security awareness training which combines on-demand interactive, engaging web-based training with frequent simulated phishing attacks right in their inbox. This is a very effective approach, with the best ROI of practically any IT security tool. We have just received a Forrester Total Economic Impact report that shows an ROI of less than a month.
See a Live Demo Webinar
Join us on Thursday, January 19, 2017, at 2:00 p.m. (EST) for a 30-minute live product demonstration of KnowBe4's game-changing Security Awareness Training Platform. You;ll see the world's largest awareness content library available in an all-you-can-eat format through our new Module Store which allows you to easily search, browse and preview content. Find out how easy and fun it is to setup fully automated campaigns to train and phish your users.
See this Live Demo Webinar: best-in-class phishing platform and the world's largest awareness content library:

Don't like to click on redirected buttons? Copy and paste this in your browser:
https://attendee.gotowebinar.com/register/3022021282543425025
Prepare to be pleasantly surprised...

We all had the nagging suspicion that antivirus is not cutting it anymore, but the following numbers confirm your intution. I have not seen more powerful ammo for IT security budget to transform your employees into an effective "last line of defense": a human firewall.
I have covered Virus Bulletin here many times, and have kept track over the years since this is the industry I lived in for 10 years before KnowBe4, and why I started this company in 2010.
Virus Bulletin (VB) is the AV industry's premier "insider site", and shows how good/bad endpoint detection rates are, but VB also covers spam filters, and tests them on a regular basis.
Both antivirus (aka endpoint protection) and spam filter tests are published in quadrants graphing the results. What most people do not know, is that participants in this industry all share the same samples, and it's often just a matter of who gets the definition out first, because soon enough everyone else has that malware sample and blocks the hash.
Well, there is bad news: your proactive antivirus detection rates have dramatically declined in 12 months.
Don't take my word for it. Just look at the quadrants for Jun-Dec 2015 and compare it to the most recent one for 2016. Note the fact that in 2015, the proactive detection is a bit spread out, but the midpoint hovers around 80%, and the reactive midpoint sits at roughly 90-95%. (Reactive means they know this sample, have a hash, and can block it, Proactive means this is an unknown sample and the security software's heuristics need to recognize the malware behavior.)

Next, look at the same midpoints a year later for April-Oct 2016.
The bad guys are winning
Note that reactive detection dropped a little bit and now clusters on the 90% line, but if you eyeball proactive detection, it has dramatically dropped to 67-70%. You would expect that with modern machine-learning techniques, proactive protection would improve, but it is going the opposite direction. By the way, if your AV is not here, the vendor declined to participate, and you can draw your own conclusions about why.

Now you might think that if AV does not catch it, your spam filter will. Think again.
Martijn Grooten at VB commented on VB's most recent spam filter test that ransomware would be much worse if it wasn't for email security solutions: "Many experts believe that ransomware is set to become an even worse problem in 2017 than it was in 2016 — which is rather bad news, given the damage it has already done.
"Still, the problem could be much worse: a test of security products performed by Virus Bulletin in November/December 2016 showed that at least 199 out of every 200 emails with a malicious attachment were blocked by email security solutions (or spam filters). Of course, the fact that spam is sent out in large volumes means that even a very low success rate is sufficient for attackers to make a good return on investment — and thus to cause a lot of damage." Here is the quadrant for spam filters:

Now, let's have a look at that number of 1 in 200 making it through.
Statistics, extrapolations and counting by the Radicati Group from February 2015, estimate the number of email users worldwide was 2.6 billion, and the amount of emails sent per day (in 2015) to be around 205 billion. That is likely higher now. DMR offers these other fascinating statistics on email, compiled in August 2015:
- The average office worker receives 121 emails a day
- Percentage of email that is spam: 49.7%
- Percentage of emails that have a malicious attachment: 2.3%
That puts the potential for malware making it in your users' inbox into the millions... every day
And that is just looking at malicious attachments, of which these days 93% are ransomware.
Keep in mind that the bad guys are also very active with CEO Fraud using a spoofed "From" email address, and even more important, the most vicious attacks (like the hacks into the Clinton campaign) were based on a simple social engineering spear phish.
The above makes a very strong case for a brand new look at your last line of defense, your users.
It makes all the sense in the world to transform them into a human firewall ASAP, and keep them on their toes with security top of mind. Step them through new-school security awareness training which combines on-demand interactive, engaging web-based training with frequent simulated phishing attacks right in their inbox. This is a very effective approach, with the best ROI of practically any IT security tool. We have just received a Forrester Total Economic Impact report that shows an ROI of less than a month.
See a Live Demo Webinar
Join us on Thursday, January 19, 2017, at 2:00 p.m. (EST) for a 30-minute live product demonstration of KnowBe4's game-changing Security Awareness Training Platform. You;ll see the world's largest awareness content library available in an all-you-can-eat format through our new Module Store which allows you to easily search, browse and preview content. Find out how easy and fun it is to setup fully automated campaigns to train and phish your users.
See this Live Demo Webinar: best-in-class phishing platform and the world's largest awareness content library:

Don't like to click on redirected buttons? Copy and paste this in your browser:
https://attendee.gotowebinar.com/register/3022021282543425025
Prepare to be pleasantly surprised...
Scam of the Week: IRS Issues Warning on New Tax Phishing Attack
It's unbelievable, but the new tax season is around the corner and the bad guys are already at it. This is a two-phase scam you need to watch out for:
PHASE 1: Cybercriminals are sending emails, posing as potential clients, and interested in services from tax professionals. Something with the innocent subject "I need a preparer to file my taxes."
The tax preparer responds, and the bad guys send a second email with a malicious attachment claiming to contain the client tax information. The tax preparer falls for this social engineering attack and opens the attachment (likely enables macros) and that compromises the machine and now the bad guys own the tax preparer's computer.
PHASE 2: The bad guys now use the tax pro's computer to send out legit looking emails to all the tax pro's clients and get their financial records sent over to their own email address, so they can quickly file a fake tax return and pocket the money, using the illegally obtained information.
Tax refund identity theft is a growing epidemic. The hassle is enormous, because when you file your own return, the IRS sends you a notice stating that “More than one tax return for you was filed”. That's when the nightmare starts, because on average it takes the IRS a long, long time to resolve tax-related theft cases.
I suggest you send the following to your employees, friends and family.
ALERT: Tax season scams are starting early this year and the bad guys are getting smarter by the month. The current scam works in two steps so watch out for possibly bogus emails for your tax information.
STEP 1: Cybercriminals are sending emails, posing as potential clients, and interested in services from tax professionals. The tax preparer responds, and the bad guys send a second email with a malicious attachment. The tax preparer falls for this social engineering attack and that compromises the machine and now the bad guys "own" the tax preparer's computer.
STEP 2: The bad guys now use the tax pro's computer to send out legit looking emails to all the tax pro's clients and get their financial records sent over to their own email address, so they can quickly file a fake tax return and pocket the money, using the illegally obtained information.
So, when you get any email about your taxes, or your W2 from literally anybody, whether you know them or not, pick up the phone and verify with your known, trusted tax preparer that they actually sent you that email. If you send tax information via email, triple-check that the email address you are sending this to is correct and type it in yourself in the "To" field.
NEVER click on "reply" and attach your tax information, because that reply email address might be spoofed. Want to be 100% safe? Hand-carry your tax info to your preparer and do the tax return in person with them.
Here is a link to the IRS site, with more tax scams you need to watch out for:
https://www.irs.gov/uac/tax-scams-consumer-alerts
Here is a link what to do to get your money back if your tax refund already *has* been stolen:
http://time.com/money/3709141/stolen-tax-refund/
Let's stay safe out there.
Think Before You Click!
It's unbelievable, but the new tax season is around the corner and the bad guys are already at it. This is a two-phase scam you need to watch out for:
PHASE 1: Cybercriminals are sending emails, posing as potential clients, and interested in services from tax professionals. Something with the innocent subject "I need a preparer to file my taxes."
The tax preparer responds, and the bad guys send a second email with a malicious attachment claiming to contain the client tax information. The tax preparer falls for this social engineering attack and opens the attachment (likely enables macros) and that compromises the machine and now the bad guys own the tax preparer's computer.
PHASE 2: The bad guys now use the tax pro's computer to send out legit looking emails to all the tax pro's clients and get their financial records sent over to their own email address, so they can quickly file a fake tax return and pocket the money, using the illegally obtained information.
Tax refund identity theft is a growing epidemic. The hassle is enormous, because when you file your own return, the IRS sends you a notice stating that “More than one tax return for you was filed”. That's when the nightmare starts, because on average it takes the IRS a long, long time to resolve tax-related theft cases.
I suggest you send the following to your employees, friends and family.
ALERT: Tax season scams are starting early this year and the bad guys are getting smarter by the month. The current scam works in two steps so watch out for possibly bogus emails for your tax information.
STEP 1: Cybercriminals are sending emails, posing as potential clients, and interested in services from tax professionals. The tax preparer responds, and the bad guys send a second email with a malicious attachment. The tax preparer falls for this social engineering attack and that compromises the machine and now the bad guys "own" the tax preparer's computer.
STEP 2: The bad guys now use the tax pro's computer to send out legit looking emails to all the tax pro's clients and get their financial records sent over to their own email address, so they can quickly file a fake tax return and pocket the money, using the illegally obtained information.
So, when you get any email about your taxes, or your W2 from literally anybody, whether you know them or not, pick up the phone and verify with your known, trusted tax preparer that they actually sent you that email. If you send tax information via email, triple-check that the email address you are sending this to is correct and type it in yourself in the "To" field.
NEVER click on "reply" and attach your tax information, because that reply email address might be spoofed. Want to be 100% safe? Hand-carry your tax info to your preparer and do the tax return in person with them.
Here is a link to the IRS site, with more tax scams you need to watch out for:
https://www.irs.gov/uac/tax-scams-consumer-alerts
Here is a link what to do to get your money back if your tax refund already *has* been stolen:
http://time.com/money/3709141/stolen-tax-refund/
Let's stay safe out there.
Think Before You Click!
Krebs's 5 Immutable Truths About Data Breaches
The intrepid investigative cybercrime reporter Brian Krebs wrote something both instructive and entertaining:
"I’ve had several requests for a fresh blog post to excerpt something that got crammed into the corner of a lengthy story published here Sunday: A list of immutable truths about data breaches, cybersecurity and the consequences of inaction. Here’s the excerpt requested from yesterday’s story:
“There are some fairly simple, immutable truths that each of us should keep in mind, truths that apply equally to political parties, organizations and corporations alike:
https://krebsonsecurity.com/2017/01/krebss-immutable-truths-about-data-breaches/
The intrepid investigative cybercrime reporter Brian Krebs wrote something both instructive and entertaining:
"I’ve had several requests for a fresh blog post to excerpt something that got crammed into the corner of a lengthy story published here Sunday: A list of immutable truths about data breaches, cybersecurity and the consequences of inaction. Here’s the excerpt requested from yesterday’s story:
“There are some fairly simple, immutable truths that each of us should keep in mind, truths that apply equally to political parties, organizations and corporations alike:
- If you connect it to the Internet, someone will try to hack it.
- If what you put on the Internet has value, someone will invest time and effort to steal it.
- Even if what is stolen does not have immediate value to the thief, he can easily find buyers for it.
- The price he secures for it will almost certainly be a tiny slice of its true worth to the victim.
- Organizations and individuals unwilling to spend a small fraction of what those assets are worth to secure them against cybercrooks can expect to eventually be relieved of said assets.”
https://krebsonsecurity.com/2017/01/krebss-immutable-truths-about-data-breaches/
Warm Regards,
Stu Sjouwerman
Quotes of the Week
Education is not the learning of the facts, but the training of the mind to think. - Albert Einstein
Education is the most powerful weapon which you can use to change the world. - Nelson Mandela
Boil things down to the most fundamental truths. Then reason up from there. - Elon Musk
Thanks for reading CyberheistNews
Education is the most powerful weapon which you can use to change the world. - Nelson Mandela
Boil things down to the most fundamental truths. Then reason up from there. - Elon Musk
Thanks for reading CyberheistNews
Security News
Study: CEO Fraud Attacks Will Overtake APT
As you know, the FBI calls it Business Email Compromise (BEC), but many other people call it CEO fraud. CXOToday wrote: "Business Email Compromise (BEC) attacks will overtake Ransomware and Advanced Persistent Threat (APT) attacks.
"BEC generally happens when email accounts of key executives are compromised and involves payments made to fraudulent bank accounts. In Singapore alone, about S$19 million has been lost through BECs between January to September 2016. There was an increase of 20% in number of such cases as compared to the same period last year. Police investigations revealed that the scam usually involves businesses with overseas dealings with email as the main form of communication in the dealings.
“As BECs are relatively easier to execute and evades cyber defense tools better than other popular attack vectors such as ransomware and APTs, it can potentially be the main cyber threat in Asia,” noted Charles Lim, Industry Principal, Cyber Security practice, Frost & Sullivan, Asia Pacific." Read more:
http://www.cxotoday.com/story/bec-attacks-will-overtake-ransomware-and-atp-attacks-in-2017/
As you know, the FBI calls it Business Email Compromise (BEC), but many other people call it CEO fraud. CXOToday wrote: "Business Email Compromise (BEC) attacks will overtake Ransomware and Advanced Persistent Threat (APT) attacks.
"BEC generally happens when email accounts of key executives are compromised and involves payments made to fraudulent bank accounts. In Singapore alone, about S$19 million has been lost through BECs between January to September 2016. There was an increase of 20% in number of such cases as compared to the same period last year. Police investigations revealed that the scam usually involves businesses with overseas dealings with email as the main form of communication in the dealings.
“As BECs are relatively easier to execute and evades cyber defense tools better than other popular attack vectors such as ransomware and APTs, it can potentially be the main cyber threat in Asia,” noted Charles Lim, Industry Principal, Cyber Security practice, Frost & Sullivan, Asia Pacific." Read more:
http://www.cxotoday.com/story/bec-attacks-will-overtake-ransomware-and-atp-attacks-in-2017/
The Ransomware Chronicle - Timeline from May '16 to Jan '17.
This is a comprehensive report on ransomware-related events covering a time frame of May 2016 – January 2017. The incidents are visually broken down into categories, including new ransomware, updates of existing strains, decryptors released, and other noteworthy news. Security researchers and users interested in the ransomware subject can now use this all-in-one knowledge base instead of having to collect data from multiple different sources. Useful!:
http://privacy-pc.com/articles/ransomware-chronicle.html
This is a comprehensive report on ransomware-related events covering a time frame of May 2016 – January 2017. The incidents are visually broken down into categories, including new ransomware, updates of existing strains, decryptors released, and other noteworthy news. Security researchers and users interested in the ransomware subject can now use this all-in-one knowledge base instead of having to collect data from multiple different sources. Useful!:
http://privacy-pc.com/articles/ransomware-chronicle.html
How to Quickly Check That Your IoT Devices Are Secure
BullGuard has a quick and easy tool that can help you find out if there are any basic problems. It’s called the Internet of Things Scanner. The service scans your public IP address to see if any of your devices are on Shodan, a search engine that lets anyone find IoT devices like cameras, printers, and thermostats that are publicly accessible on the internet. Anything that’s publicly accessible may also be vulnerable to hackers if there are any security flaws in the software that can be exploited. Run it here:
http://iotscanner.bullguard.com/deep-scan/
BullGuard has a quick and easy tool that can help you find out if there are any basic problems. It’s called the Internet of Things Scanner. The service scans your public IP address to see if any of your devices are on Shodan, a search engine that lets anyone find IoT devices like cameras, printers, and thermostats that are publicly accessible on the internet. Anything that’s publicly accessible may also be vulnerable to hackers if there are any security flaws in the software that can be exploited. Run it here:
http://iotscanner.bullguard.com/deep-scan/
The 3 C's of Security Awareness
Lance Spitzner, SANS' famous leader of Securing The Human wrote:
"Explaining the technical part of security comes easy for many of us. But the soft skills needed to change behavior are often sadly missing.
"Over 80% of security awareness professionals have a background in either information security or information technology, according to SANS's 2016 Security Awareness Report. Less than 15% have a background in soft skills such as training, marketing, or communications. The technical part of awareness comes naturally, not so much the softer side of behavior change.
"It's one reason there is an uphill battle when it comes to building comprehensive awareness programs. Because cybersecurity professionals, including awareness leaders, are heavily steeped in technical skills, they understand what behaviors need to be changed but fall short in how they attempt to change those behaviors.
"In a previous post, I described the "what" of a good security awareness program — what you should focus on and what makes a program effective. After analyzing scores of awareness program outcomes and working with hundreds of security awareness leaders in 2016, it's clear to me that we need to place a greater emphasis on how to change behavior and how to run a security awareness program in order to make awareness behavior stick.
"The soft skills needed to change behavior and deliver key messages are critical to the success of an awareness program, starting with gaining executive-level support all the way to scrapping boring PowerPoint decks in favor of a personal story to better engage employees. To help awareness officers address this in 2017, I have put together the three C's of security awareness program success: communication, collaboration, and culture."
Continue reading about these three points and what action items to take!:
http://www.darkreading.com/endpoint/the-3-cs-of-security-awareness-/a/d-id/1327854
Lance Spitzner, SANS' famous leader of Securing The Human wrote:
"Explaining the technical part of security comes easy for many of us. But the soft skills needed to change behavior are often sadly missing.
"Over 80% of security awareness professionals have a background in either information security or information technology, according to SANS's 2016 Security Awareness Report. Less than 15% have a background in soft skills such as training, marketing, or communications. The technical part of awareness comes naturally, not so much the softer side of behavior change.
"It's one reason there is an uphill battle when it comes to building comprehensive awareness programs. Because cybersecurity professionals, including awareness leaders, are heavily steeped in technical skills, they understand what behaviors need to be changed but fall short in how they attempt to change those behaviors.
"In a previous post, I described the "what" of a good security awareness program — what you should focus on and what makes a program effective. After analyzing scores of awareness program outcomes and working with hundreds of security awareness leaders in 2016, it's clear to me that we need to place a greater emphasis on how to change behavior and how to run a security awareness program in order to make awareness behavior stick.
"The soft skills needed to change behavior and deliver key messages are critical to the success of an awareness program, starting with gaining executive-level support all the way to scrapping boring PowerPoint decks in favor of a personal story to better engage employees. To help awareness officers address this in 2017, I have put together the three C's of security awareness program success: communication, collaboration, and culture."
Continue reading about these three points and what action items to take!:
http://www.darkreading.com/endpoint/the-3-cs-of-security-awareness-/a/d-id/1327854
SANS Kicks Off 2017 With Social Engineering Basics Ouch!
They said: "We are excited to announce the first issue of OUCH! for 2017. This month, led by Guest Editor James Lyne, we focus on Social Engineering. We wanted to kick off the new year with the review of the basics. By understanding how social engineering works, people will be far better prepared to stop many of today's latest online attacks. Share OUCH! with your family, friends, and coworkers. English Version (PDF)
http://securingthehuman.sans.org/newsletters/ouch/issues/OUCH-201701_en.pdf?
They said: "We are excited to announce the first issue of OUCH! for 2017. This month, led by Guest Editor James Lyne, we focus on Social Engineering. We wanted to kick off the new year with the review of the basics. By understanding how social engineering works, people will be far better prepared to stop many of today's latest online attacks. Share OUCH! with your family, friends, and coworkers. English Version (PDF)
http://securingthehuman.sans.org/newsletters/ouch/issues/OUCH-201701_en.pdf?
Cyberheist 'Fave' Links
This Week's Links We Like, Tips, Hints and Fun Stuff
- DOD successfully tests a terrifying swarm of 104 micro-drones. Holy $#!+:
http://arstechnica.com/information-technology/2017/01/dod-successfully-tests-terrifying-swarm-of-104-micro-drones/
- Sure. Kick the robot. What's the worst that could happen?:
https://twitter.com/alex_parker/status/579753858328440833
- Crows are amongst the most intelligent birds on the planet and this video is another hilarious example of it:
http://www.flixxy.com/clever-crow-steals-spoon.htm?utm_source=4
- OK, here is a good one. Remember to always: "Consider the source" when you look at information? "RT" is the flagship of the Russian propaganda machine:
https://www.youtube.com/watch?v=E7t5zbKnvQk
- Beautiful airborne footage of the Airbus Beluga - a modified version of the Airbus A300-600 wide-body airliner specifically designed to transport oversized air cargo:
http://www.flixxy.com/the-airbus-beluga.htm?utm_source=4
- Pretty mermaid at the Morocco Mall in Casablanca. This gal learned her trade in Weeki Wachee Springs in Florida:
http://www.flixxy.com/beautiful-mermaid-show-at-the-morocco-mall-in-casablanca.htm?utm_source=4 - The classic video of legendary solo climber Dan Osman climbing the 400 foot 'Bear's Reach' rock in in 4 min 25 sec:
http://www.flixxy.com/the-rock-climber.htm?utm_source=4





