CyberheistNews Vol 6 #51
Scam of the Week: The 1 Billion Yahoo Hack 
This is getting old. It's all over the press... again. Here is a Reuters article where I am quoted, which covers the most recent billion-record Yahoo hack.
Some people asked me after our Flash announcement last week: "Stu, really, these hacks happened a few years ago, closing down my whole Yahoo account, or blocking Yahoo at the firewall... aren't you going a bit overboard here?"
Good question. Here is my take:
Well, that whole 1B database was sold on the dark web by a group of professional blackhats from Eastern Europe for 300K, (and is still for sale at a much lower price right now) which means that a ton of bad guys now have these credentials, but worse, they have answers to security questions like "your mother's maiden name" which do not change like passwords, and and backup email addresses that could help with resetting forgotten passwords.
Bloomberg reported that 150,000 U.S. government and military employees are among the victims in the latest breach.
My position is that all Yahoo accounts need to be considered compromised. They are sitting ducks for spam, phishing and malware attacks. If employees check their Yahoo account on their lunch break, do you want to expose your company network to that?
It looks like Yahoo has not learned their lessons, so new hacks can happen any time. There has been an exodus of qualified Yahoo staff and they seem to be unable to apply best security practices. They are now forcing all users (link to WSJ article) to change their password, but that's too little, too late. I simply have lost trust.
So, I recommend you warn your users, friends and family... again. We have been here before on September 23rd when the 500 million record hack was first announced.
In September, Yahoo did not force people to change passwords, but now they are forcing a password change, and the bad guys are (again) all over this -- the ones that own the Yahoo database but also the ones that do not, because news like this is a phishing paradise.
This is a phishing paradise with significant fallout
Phishing attacks likely will be the number one possible fallout, with Yahoo user accounts being used for social engineering attacks. However, since many people use the same username and passwords across multiple sites, the other thing that will continue to happen is called "credential-stuffing", a brute-force attack where attackers inject stolen usernames, passwords and possibly the answers to security questions into a website until they find a match using the stolen Yahoo username and passwords.
The bad guys will continue to exploit this, so remind your users
Remind your users, friends and family. They will be likely be confronted with Yahoo-related scams in their inbox. The bad guys are going to leverage this in a variety of ways, starting with bogus password reset phishing attacks, but also with masked links so that if you click on it you wind up on a compromised site which could steal personal information and/or infect the computer. The variations are infinite, but the defense against it is relatively simple.
I suggest you send them the following reminder - You're welcome to copy/paste/edit:
"Yahoo announced that 1 billion of their accounts were hacked. These accounts are now sold by internet criminals to other bad guys which are going to use this information in a variety of ways. For instance, they will send phishing emails claiming you need to change your Yahoo account, looking just like the real ones. Here is what I suggest you do right away.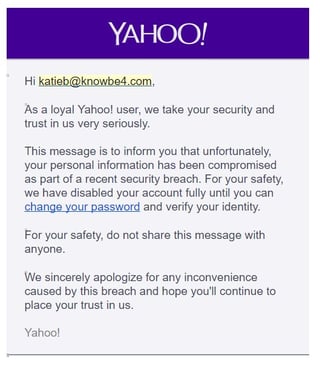 If you are a KnowBe4 customer, we have a template in the Current Events Campaign which I suggest you send to all your users immediately as a reminder.
If you are a KnowBe4 customer, we have a template in the Current Events Campaign which I suggest you send to all your users immediately as a reminder.
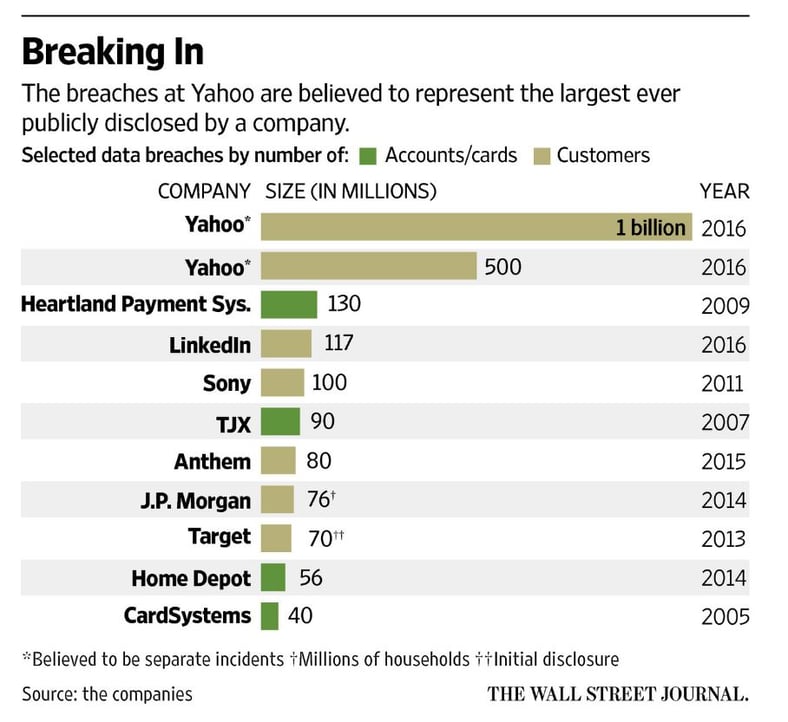
This is the largest hack ever, below is a graph fresh from an article in the Wall Street Journal that puts it in perspective. I suggest you send this to your management.
This is exactly the kind of thing that they want to prevent from happening and security awareness training is the number one thing that makes your organization more hack-resistant since your users are your weakest IT security link.

This is getting old. It's all over the press... again. Here is a Reuters article where I am quoted, which covers the most recent billion-record Yahoo hack.
Some people asked me after our Flash announcement last week: "Stu, really, these hacks happened a few years ago, closing down my whole Yahoo account, or blocking Yahoo at the firewall... aren't you going a bit overboard here?"
Good question. Here is my take:
Well, that whole 1B database was sold on the dark web by a group of professional blackhats from Eastern Europe for 300K, (and is still for sale at a much lower price right now) which means that a ton of bad guys now have these credentials, but worse, they have answers to security questions like "your mother's maiden name" which do not change like passwords, and and backup email addresses that could help with resetting forgotten passwords.
Bloomberg reported that 150,000 U.S. government and military employees are among the victims in the latest breach.
My position is that all Yahoo accounts need to be considered compromised. They are sitting ducks for spam, phishing and malware attacks. If employees check their Yahoo account on their lunch break, do you want to expose your company network to that?
It looks like Yahoo has not learned their lessons, so new hacks can happen any time. There has been an exodus of qualified Yahoo staff and they seem to be unable to apply best security practices. They are now forcing all users (link to WSJ article) to change their password, but that's too little, too late. I simply have lost trust.
So, I recommend you warn your users, friends and family... again. We have been here before on September 23rd when the 500 million record hack was first announced.
In September, Yahoo did not force people to change passwords, but now they are forcing a password change, and the bad guys are (again) all over this -- the ones that own the Yahoo database but also the ones that do not, because news like this is a phishing paradise.
This is a phishing paradise with significant fallout
Phishing attacks likely will be the number one possible fallout, with Yahoo user accounts being used for social engineering attacks. However, since many people use the same username and passwords across multiple sites, the other thing that will continue to happen is called "credential-stuffing", a brute-force attack where attackers inject stolen usernames, passwords and possibly the answers to security questions into a website until they find a match using the stolen Yahoo username and passwords.
The bad guys will continue to exploit this, so remind your users
Remind your users, friends and family. They will be likely be confronted with Yahoo-related scams in their inbox. The bad guys are going to leverage this in a variety of ways, starting with bogus password reset phishing attacks, but also with masked links so that if you click on it you wind up on a compromised site which could steal personal information and/or infect the computer. The variations are infinite, but the defense against it is relatively simple.
I suggest you send them the following reminder - You're welcome to copy/paste/edit:
"Yahoo announced that 1 billion of their accounts were hacked. These accounts are now sold by internet criminals to other bad guys which are going to use this information in a variety of ways. For instance, they will send phishing emails claiming you need to change your Yahoo account, looking just like the real ones. Here is what I suggest you do right away.
- If you do not use your Yahoo account a lot. Close it down because it's a risk. If you use it every day:
- Open your browser and go to Yahoo. Do not use a link in any email. Reset your password and make it a strong, complex password or rather a pass-phrase.
- If you were using that same password on multiple websites, you need to stop that right now. Using the same password all over the place is an invitation to get hacked. If you did use your Yahoo passwords on other sites, go to those sites and change the password there too. Also change the security questions and make the answer something non-obvious.
- At the house, use a free password manager that can generate hard-to-hack passwords, keep and remember them for you.
- Watch out for any phishing emails that relate to Yahoo in any way and ask for information.
- Now would also be a good time to use Yahoo Account Key, a simple authentication tool that eliminates the need to use a password altogether.
 If you are a KnowBe4 customer, we have a template in the Current Events Campaign which I suggest you send to all your users immediately as a reminder.
If you are a KnowBe4 customer, we have a template in the Current Events Campaign which I suggest you send to all your users immediately as a reminder. This is the largest hack ever, below is a graph fresh from an article in the Wall Street Journal that puts it in perspective. I suggest you send this to your management.
This is exactly the kind of thing that they want to prevent from happening and security awareness training is the number one thing that makes your organization more hack-resistant since your users are your weakest IT security link.

IBM Study: 70% of Businesses Attacked Pay Ransomware
A rather mind-blowing 70% of businesses hit by ransomware paid the hackers to regain access to hijacked systems and files, according to a new IBM X-Force Ransomware report. Of the attacked businesses, 20 percent paid over 40,000 dollars to decrypt their files, while more than half paid more than 10,000 dollars.
The IBM study, “Ransomware: How Consumers and Businesses Value Their Data” surveyed 600 business leaders and more than 1,000 consumers in the U.S. to determine the value placed on different types of data.
Around 66% of the report’s respondents are generally worried about hackers compromising data, and almost 60 percent of business leaders said they would be willing to pay the ransom to regain access to financial records, intellectual property, business plans and consumer data, the report found.
And depending on the datatype, they’re willing to pay between 20,000 dollars and 50,000 dollars to get their data back.
FBI: "Not a Good Idea to Pay up"
Law enforcement agencies like the FBI say that it's not a good idea to pay the ransom. But unlocking patient records in a healthcare site is crucial to keeping patients safe - so hospitals pay up if backups fail.
IBM researchers determined financial returns on ransomware are expected to grow to over 1 billion dollars for cybercriminals in the next year, which means these types of extortion attempts will continue to expand.
Small to medium businesses are less prepared for a ransomware attack than larger businesses. And medium to large organizations are more likely to have taken action in the last three months to protect data.
Further, 74 percent of large organizations require employees to regularly change passwords, versus 56 percent of small companies. And only 30 percent of small organizations offer IT security awareness training. OUCH.
“Cybercriminals have no boundaries when it comes to their targets,” Limor Kessem, executive security adviser for IBM Security, said in a statement. “The digitization of memories, financial information and trade secrets require a renewed vigilance to protect it from extortion schemes like ransomware.”
Ransomware attacks very often succeed through a phishing attack with a spoofed 'From' address. These types of attacks are hard to spot and employees tend to fall for them.
Find out now if your email server is configured correctly. Our tests over the last 2 years show that 82% of servers fail to handle spoofed emails correctly.
https://info.knowbe4.com/domain-spoof-test-chn
Link to the blog post and the IBM study which is excellent budget ammo, but you do need to register:
https://blog.knowbe4.com/ibm-study-70-percent-of-businesses-attacked-pay-ransomware
A rather mind-blowing 70% of businesses hit by ransomware paid the hackers to regain access to hijacked systems and files, according to a new IBM X-Force Ransomware report. Of the attacked businesses, 20 percent paid over 40,000 dollars to decrypt their files, while more than half paid more than 10,000 dollars.
The IBM study, “Ransomware: How Consumers and Businesses Value Their Data” surveyed 600 business leaders and more than 1,000 consumers in the U.S. to determine the value placed on different types of data.
Around 66% of the report’s respondents are generally worried about hackers compromising data, and almost 60 percent of business leaders said they would be willing to pay the ransom to regain access to financial records, intellectual property, business plans and consumer data, the report found.
And depending on the datatype, they’re willing to pay between 20,000 dollars and 50,000 dollars to get their data back.
FBI: "Not a Good Idea to Pay up"
Law enforcement agencies like the FBI say that it's not a good idea to pay the ransom. But unlocking patient records in a healthcare site is crucial to keeping patients safe - so hospitals pay up if backups fail.
IBM researchers determined financial returns on ransomware are expected to grow to over 1 billion dollars for cybercriminals in the next year, which means these types of extortion attempts will continue to expand.
Small to medium businesses are less prepared for a ransomware attack than larger businesses. And medium to large organizations are more likely to have taken action in the last three months to protect data.
Further, 74 percent of large organizations require employees to regularly change passwords, versus 56 percent of small companies. And only 30 percent of small organizations offer IT security awareness training. OUCH.
“Cybercriminals have no boundaries when it comes to their targets,” Limor Kessem, executive security adviser for IBM Security, said in a statement. “The digitization of memories, financial information and trade secrets require a renewed vigilance to protect it from extortion schemes like ransomware.”
Ransomware attacks very often succeed through a phishing attack with a spoofed 'From' address. These types of attacks are hard to spot and employees tend to fall for them.
Find out now if your email server is configured correctly. Our tests over the last 2 years show that 82% of servers fail to handle spoofed emails correctly.
https://info.knowbe4.com/domain-spoof-test-chn
Link to the blog post and the IBM study which is excellent budget ammo, but you do need to register:
https://blog.knowbe4.com/ibm-study-70-percent-of-businesses-attacked-pay-ransomware
My Interview at CSO About Ransomware-As-A-Service
Joan Goodchild, Editor-in-chief at CSO sat me down and asked why Ransomware-as-a-Service has taken off recently. She said:
"It’s not just your company that’s moving to cloud services - cybercriminals are doing this too. Recently, the industry has seen ransomware move to a service model, where criminals can purchase third-party versions of ransomware and put their own “label” on them.
In this episode of Security Sessions, I spoke with Stu Sjouwerman, CEO of KnowBe4, about the reasons why ransomware is being offered as a cloud service, and how CSOs and CISOs can prepare their staffs to fight ransomware."
Among the highlights of the video are the following sections:
http://www.csoonline.com/article/3147815/security/the-rise-of-ransomware-as-a-service.html
Joan Goodchild, Editor-in-chief at CSO sat me down and asked why Ransomware-as-a-Service has taken off recently. She said:
"It’s not just your company that’s moving to cloud services - cybercriminals are doing this too. Recently, the industry has seen ransomware move to a service model, where criminals can purchase third-party versions of ransomware and put their own “label” on them.
In this episode of Security Sessions, I spoke with Stu Sjouwerman, CEO of KnowBe4, about the reasons why ransomware is being offered as a cloud service, and how CSOs and CISOs can prepare their staffs to fight ransomware."
Among the highlights of the video are the following sections:
- 1:00 Explaining the concept of ransomware-as-a-service
- 1:53 Why is this appealing to the cybercriminal community?
- 2:18 How are these ransomware attacks being perpetrated?
- 3:07 How can CSOs and CISOs train users to be aware of the red flags of ransomware?
- 3:29 Beyond training, what else can companies do to prevent ransomware attacks?
- 4:18 If a company does get attacked, should they pay the ransom?
http://www.csoonline.com/article/3147815/security/the-rise-of-ransomware-as-a-service.html
KnowBe4 and Barracuda Team up to Educate and Protect Users Against Phishing Attacks
KnowBe4, the most popular security awareness training and simulated phishing platform, and Barracuda Networks, Inc. (NYSE: CUDA), a leading provider of cloud-enabled security and data protection solutions, announced a joint effort to enhance email security, improve user awareness, and help protect employees from targeted phishing attacks.
As part of the effort, Barracuda’s cloud-based email security solutions, including Barracuda Essentials for Office 365, now includes integrated education and training exercises to help employees identify potential threats, such as phishing and ransomware, to reduce risk of data loss.
“Even the strongest security technology and practices cannot compete with a highly sophisticated spear phishing attack. Unfortunately, it’s not a matter of if, but when an employee will click on a malicious link,” said Buddy Davis, Vice President at Data Network Solutions, a Barracuda Premier Partner.
“With this announcement Barracuda and KnowBe4 are bridging the gap between security technology and training education. The joint effort merges award-winning protection from email-borne attacks, spam, and viruses, with industry-leading training and education to help workforces identify potential threats.”
An educated employee trained to identify potential threats significantly reduces the risk of an organization falling prey to spear phishing and ransomware attacks. However, with the evolving nature of these attacks and human error at play, it is inevitable that someone will eventually click on a suspicious or malicious link, making it even more critical to deploy layered security designed to stop these targeted attacks.
To learn more about how KnowBe4 and Barracuda are helping to address this need, please visit https://info.knowbe4.com/kmsat_get_a_quote_bc.
KnowBe4, the most popular security awareness training and simulated phishing platform, and Barracuda Networks, Inc. (NYSE: CUDA), a leading provider of cloud-enabled security and data protection solutions, announced a joint effort to enhance email security, improve user awareness, and help protect employees from targeted phishing attacks.
As part of the effort, Barracuda’s cloud-based email security solutions, including Barracuda Essentials for Office 365, now includes integrated education and training exercises to help employees identify potential threats, such as phishing and ransomware, to reduce risk of data loss.
“Even the strongest security technology and practices cannot compete with a highly sophisticated spear phishing attack. Unfortunately, it’s not a matter of if, but when an employee will click on a malicious link,” said Buddy Davis, Vice President at Data Network Solutions, a Barracuda Premier Partner.
“With this announcement Barracuda and KnowBe4 are bridging the gap between security technology and training education. The joint effort merges award-winning protection from email-borne attacks, spam, and viruses, with industry-leading training and education to help workforces identify potential threats.”
An educated employee trained to identify potential threats significantly reduces the risk of an organization falling prey to spear phishing and ransomware attacks. However, with the evolving nature of these attacks and human error at play, it is inevitable that someone will eventually click on a suspicious or malicious link, making it even more critical to deploy layered security designed to stop these targeted attacks.
To learn more about how KnowBe4 and Barracuda are helping to address this need, please visit https://info.knowbe4.com/kmsat_get_a_quote_bc.
Warm Regards,
Stu Sjouwerman
Quotes Of The Week
Dare to think for yourself. - Voltaire - Philosopher and Writer (1694 - 1778)
We cannot solve our problems with the same thinking we used when we created them.
- Albert Einstein
Thanks for reading CyberheistNews
We cannot solve our problems with the same thinking we used when we created them.
- Albert Einstein
Thanks for reading CyberheistNews
Security News
How Your Program Saved My Company 85,000 Dollars Last Week
Hi Stu,
I wanted to share with you, how your program saved my company 85,000 dollars last week.
We started training all staff including senior people and the accounting staff a few months ago when we subscribed to the KnowBe4 training system.
Two weeks ago our accounting team received an email from a supplier that asked us to “change” the wire transfer bank accounts payment info to a new account. Our accounting staff and our president – our other company is in Canada - immediately became suspicious to this request, because of KnowBe4 training!
They contacted the representatives of the supplier (supplier is in China) and they all confirmed its OK. We went ahead and sent the money, then the supplier contacted us looking for their money!! They reported they never received it.
It turns out the our supplier in China was hacked, and that compromise sent out bogus wire transfer banking change requests to all its customers. Because we received a confirmation it was OK (they made a mistake) we received all of our funds back!
Our President called me yesterday to thank me for starting KnowBe4. So thank you Stu!
Best Regards,
F.A.- CEO
Hi Stu,
I wanted to share with you, how your program saved my company 85,000 dollars last week.
We started training all staff including senior people and the accounting staff a few months ago when we subscribed to the KnowBe4 training system.
Two weeks ago our accounting team received an email from a supplier that asked us to “change” the wire transfer bank accounts payment info to a new account. Our accounting staff and our president – our other company is in Canada - immediately became suspicious to this request, because of KnowBe4 training!
They contacted the representatives of the supplier (supplier is in China) and they all confirmed its OK. We went ahead and sent the money, then the supplier contacted us looking for their money!! They reported they never received it.
It turns out the our supplier in China was hacked, and that compromise sent out bogus wire transfer banking change requests to all its customers. Because we received a confirmation it was OK (they made a mistake) we received all of our funds back!
Our President called me yesterday to thank me for starting KnowBe4. So thank you Stu!
Best Regards,
F.A.- CEO
Law Firms Are Increasingly Targeted With Spear Phishing
The massive data breach of what became known as the Panama Papers, in which 11.5 million files were stolen from the law firm of Mossack Fonseca is far from an isolated incident. Law firms are targeted for private information about the companies they represent for a variety of purposes from industrial espionage to insider trading.
In the last few months, several American law firms were hacked, where attackers were able to steal gigabytes of data, Fortune reports. The incidents involved hackers getting into the email accounts of partners at well-known firms, and then relaying messages and other data from the partners’ inboxes to outside servers.
In the case of successful attacks, firms had deployed firewalls and other technical measures to guard their networks, but they failed to detect the email-driven attack. Such attacks, known as “spear phishing,” target victims with personalized emails.
Last week, NY Attorney General Eric T. Schneiderman issued a consumer alert following recent reports that hackers are targeting attorneys in New York pretending to be representatives of his office. Attorneys are receiving email claiming that their business was the subject of a complaint for which they have 10 days to respond.
The email includes a hyperlink to the “complaint” but in reality it links to a website that installs malicious software on the person’s computer. Link:
http://www.ag.ny.gov/press-release/ag-schneiderman-issues-alert-phishing-scam-targeting-new-york-attorneys
Full link to Fortune article with a lot more data:
http://fortune.com/2016/12/07/china-law-firms/
It is a very good idea to step all employees in law firms through new-school security awareness training to prevent data breaches like this. Find out how affordable this is for your organization and be pleasantly surprised:
https://www.knowbe4.com/products/enterprise-security-awareness-training/
The massive data breach of what became known as the Panama Papers, in which 11.5 million files were stolen from the law firm of Mossack Fonseca is far from an isolated incident. Law firms are targeted for private information about the companies they represent for a variety of purposes from industrial espionage to insider trading.
In the last few months, several American law firms were hacked, where attackers were able to steal gigabytes of data, Fortune reports. The incidents involved hackers getting into the email accounts of partners at well-known firms, and then relaying messages and other data from the partners’ inboxes to outside servers.
In the case of successful attacks, firms had deployed firewalls and other technical measures to guard their networks, but they failed to detect the email-driven attack. Such attacks, known as “spear phishing,” target victims with personalized emails.
Last week, NY Attorney General Eric T. Schneiderman issued a consumer alert following recent reports that hackers are targeting attorneys in New York pretending to be representatives of his office. Attorneys are receiving email claiming that their business was the subject of a complaint for which they have 10 days to respond.
The email includes a hyperlink to the “complaint” but in reality it links to a website that installs malicious software on the person’s computer. Link:
http://www.ag.ny.gov/press-release/ag-schneiderman-issues-alert-phishing-scam-targeting-new-york-attorneys
Full link to Fortune article with a lot more data:
http://fortune.com/2016/12/07/china-law-firms/
It is a very good idea to step all employees in law firms through new-school security awareness training to prevent data breaches like this. Find out how affordable this is for your organization and be pleasantly surprised:
https://www.knowbe4.com/products/enterprise-security-awareness-training/
Top Five Phishing Awareness Training Fails
Our friends at PhishLabs made some very good points in a blog post a little while ago.
"Phishing awareness training is an essential security function. But while it may seem straightforward, training employees to spot phishing attacks is no simple task. Done poorly, phishing awareness training can be counterproductive and leave your organization more vulnerable instead of more secure.
Here are 5 common pitfalls to avoid when training your users to spot and report phishing attacks.
1) Infrequent testing. Spotting phishing attacks is a skill that needs constant sharpening and reminders to stay vigilant. Testing once or twice a year might check the box for an auditor, but it’s not enough. Maintaining an ongoing process so users remain vigilant in their email traffic decisions, not just a one-off experiment, is imperative.
2) Click rate sandbagging. Click rate the only measure of success? Great! Just make the phishing simulations easy to spot and call it a day. Who cares if the real-world attacks are more complex and sophisticated? If your click rate is consistently close to zero, it says more about the difficulty of your simulations (or lack thereof) than the vigilance of your employees.
3) Not finishing the drill. Training employees to spot phishing attacks is only part of the equation. What happens when employees report suspicious email. If those reports are sitting in a helpdesk queue, they aren’t doing you any good. There’s probably a legit attack in those reports, and it’s likely that someone else fell for it. Would you rather find out about that now? Or wait until it becomes a much bigger security incident? Have a process in place to collect reported phishing emails, analyze them, and mitigate threats.
4) “Best guess” phishing simulations. Sure, cybercriminals might use that major news headline in a phishing attack. But what’s the real probability that it will really be used to target your employees? You can’t train an employee to be sharp against every conceivable phishing ploy, so it’s important to focus your efforts on those that present the most risk. The ideal phishing awareness training program simulates the techniques most likely to be used by your adversaries.
5) Lame training videos. People have high expectations when it comes to video content these days, and the quality of the training videos you pair with phishing simulations says a lot to employees about how serious this really is. Videos that are childish, or videos that blatantly attempt to stoke people’s fears, can be detrimental and reflect poorly on the company’s security team. Remember, it’s the video that delivers the training when an employee fails a simulated phish. If it isn’t effective, the rest doesn’t matter. So don’t skimp on training videos!"
We could not agree more.
Our friends at PhishLabs made some very good points in a blog post a little while ago.
"Phishing awareness training is an essential security function. But while it may seem straightforward, training employees to spot phishing attacks is no simple task. Done poorly, phishing awareness training can be counterproductive and leave your organization more vulnerable instead of more secure.
Here are 5 common pitfalls to avoid when training your users to spot and report phishing attacks.
1) Infrequent testing. Spotting phishing attacks is a skill that needs constant sharpening and reminders to stay vigilant. Testing once or twice a year might check the box for an auditor, but it’s not enough. Maintaining an ongoing process so users remain vigilant in their email traffic decisions, not just a one-off experiment, is imperative.
2) Click rate sandbagging. Click rate the only measure of success? Great! Just make the phishing simulations easy to spot and call it a day. Who cares if the real-world attacks are more complex and sophisticated? If your click rate is consistently close to zero, it says more about the difficulty of your simulations (or lack thereof) than the vigilance of your employees.
3) Not finishing the drill. Training employees to spot phishing attacks is only part of the equation. What happens when employees report suspicious email. If those reports are sitting in a helpdesk queue, they aren’t doing you any good. There’s probably a legit attack in those reports, and it’s likely that someone else fell for it. Would you rather find out about that now? Or wait until it becomes a much bigger security incident? Have a process in place to collect reported phishing emails, analyze them, and mitigate threats.
4) “Best guess” phishing simulations. Sure, cybercriminals might use that major news headline in a phishing attack. But what’s the real probability that it will really be used to target your employees? You can’t train an employee to be sharp against every conceivable phishing ploy, so it’s important to focus your efforts on those that present the most risk. The ideal phishing awareness training program simulates the techniques most likely to be used by your adversaries.
5) Lame training videos. People have high expectations when it comes to video content these days, and the quality of the training videos you pair with phishing simulations says a lot to employees about how serious this really is. Videos that are childish, or videos that blatantly attempt to stoke people’s fears, can be detrimental and reflect poorly on the company’s security team. Remember, it’s the video that delivers the training when an employee fails a simulated phish. If it isn’t effective, the rest doesn’t matter. So don’t skimp on training videos!"
We could not agree more.
Cyberheist 'Fave' Links
This Week's Links We Like, Tips, Hints And Fun Stuff
- Zapatou’s latest compilation of the 367 most captivating video clips - from amazing stunts, to incredible visuals, to people just being awesome.
http://www.flixxy.com/best-of-the-web-2016-edited-by-zapatou.htm?utm_source=4
- Freeskier Jesper Tjäder pulled off an epic trick, skiing an upside down loop on a 360º rail:
http://www.flixxy.com/loop-the-loop-on-ski.htm?utm_source=4
- Amazon Prime Air has begun private trials in England, and the first customer delivery by drone recently took place. Check it out!
http://www.flixxy.com/amazons-first-drone-delivery-in-england.htm?utm_source=4
- Ever been late for a flight? Jason Paul uses his jaw-dropping freerunning skills to get through Munich airport and catches his flight in record time:
http://www.flixxy.com/last-call-for-mr-paul.htm?utm_source=4
- 11 Weirdest Homemade Bicycle Inventions. Now, how to stop and get off?
https://www.youtube.com/watch?v=tjqnMKXrkxA
- CLASSIC! Carpool Karaoke with Mariah Carey, Adele, Demi Lovato and Nick Jonas, Elton John, Selena Gomez, Lady Gaga, Chris Martin, Red Hot Chili Peppers and Gwen Stefani:
http://www.flixxy.com/all-i-want-for-christmas-carpool-karaoke-with-mariah-carey-adele-lady-gaga-elton-john.htm?utm_source=4
- Out of the archives: A beautiful, life-size, fully decorated Christmas tree flying over Mission Bay in San Diego:
http://www.flixxy.com/radio-controlled-flying-christmas-tree.htm?utm_source=4
- Star Wars Rogue One - A Phish Story. Rogue One is the epic tale of a scrappy group of rebels and their daring mission to steal the plans for the Death Star. Given what we know about cyber security, we couldn't help wondering if perhaps it might have actually happened in a different way. LOL:
https://vimeo.com/195371513 - Misconceptions about Vikings, Lady Godiva, Napoleon Bonaparte, the Roman Vomitoria, and Christopher Columbus cleared up by C.G.P Grey:
http://www.flixxy.com/five-historical-lies-columbus-vikings-napoleon-vomitoria-lady-godiva.htm?utm_source=4





