| Security News |
Here are the Top 10 predictions for 2017 in alphabetical order
|
|
1) ARTIFICIAL INTELLIGENCE.
Everyone and their brother will claim that they have machine learning and/or AI as an offering and/or built into their product/platform, yours truly included. It's going to be marketing buzzword hell, because at the moment AI is not nearly as smart as people would like it to be, so buyer beware.
However...
Machine Learning and AI *will* move forward with lightning speed. Some of them will pass the Turing test. You will be able to talk to supportbots and not know if it is a human or not. You will also see fully programmable digital avatars going into commercial use.
2) BLOCKCHAIN
Micropayments and Blockchain applications will go mainstream in 2017. Mobile payments will grow massively, and apps will use "micro-payments" built on digital protocols like the Blockchain. Perhaps Blockchain will allow us to vote from our own devices in the next election. We will see the first smart contracts built on Blockchain.
Ransomware-as-a-Service will become a major threat vector, with a new technical feature using Blockchain to deliver the decryption keys after ransom payment.
3) BOARD ROOM
During 2016, boards of directors have realized that InfoSec risk management is an enterprise risk equivalent to financial, reputational, and legal risk. In 2017, there will be a raft of boards demanding a corporate security culture starting from the C-level down.
4) CEO FRAUD aka BUSINESS EMAIL COMPROMISE
CEO fraud was the up and coming cyberfraud scheme right after ransomware these last 12 months. During 2017 it will be an epidemic, equaling the ransomware plague we are suffering now. Remember the Nigerian prince scams? These cyber gangs are really in Nigeria, but they have climbed up in the criminal food chain and CEO fraud is their focus now. Train your high-risk users within an inch of their lives.
5) ESPIONAGE
During 2017 it will become apparent that espionage will turn out to have gone massively mobile and nobody knew about it. Revelations about both Android and iPhone devices will show they have had 0-days for several years and the NSA was able to own any device they wanted at any time.
6) INTERNET OF THINGS
A major outage caused by a purely malicious Botnet of Things like Mirai will prompt the new U.S. Administration to enforce IoT device security standards and require certification from device vendors.
7) MOBILE MALWARE
Mobile malware will continue to grow at an exponential rate. During 2017 tens of millions of smartphones will be infected with auto-rooting malware. New strains can embed themselves in a phone’s bootloader and remain persistent even after factory reset. Scary.
8) OPEN SOURCE
In 2017 we will see a very high-profile data breach based on an open source vulnerability that was disclosed in...wait for it... 2012. The average age of an open source vulnerability in commercial applications is more than five years, and almost everyone is using Open Source these days. Ouch.
9) RANSOMWARE
We have seen exponential ransomware infections in 2016, and this trend will continue in 2017. There are close to 250 different families at this point, this will triple in the next 12 months.
Locky will be the first strain with 1 billion dollar in criminal revenues. Organized Eastern European cybercrime will continue to specifically target health care, education and local government with updated ransomware strains.
10) STATE SPONSORED HACKING
Look, we have a low-grade cyberwar and massive cyber arms-race going on. It's simmering and now and then it flares up, basically with proof-of-concept attacks, except for Stuxnet which was the real deal. In 2017 we may very well see the first major real-world damage caused by state-sponsored hacking.
Bonus: 2017 will finally see an effective platform for InfoSec Crowd intelligence that allows white hats to be organized and improve security strategies.
WILD-ASS Guesses For 2017:
* A cyberattack on a medical device will cause the first confirmed injury to a patient
* SWIFT bank heists will be available as CaaS: Cyberheist-as-a-Service.
* A city-wide attack in a worm-like form targets IoT devices and destroys them.
* Hackers will put together a drone-swarm which hijacks a whole city's Wi-fi networks.
* Porn has always been a trailblazer in adopting new technology. At the moment, the bleeding edge is Virtual Reality, integrated with sex toys. This is a booming market and one of the leaders will be hacked and all customers exposed.
* Ransomware "Newbie Crims" ruin the reputation of the established players and the first real-world gang war breaks out with people getting killed.
|
| Does *Your* Antivirus Block The Latest Ransomware Strains? |
|
Bad guys are constantly coming out with new versions to evade detection. Are your defenses effective in blocking ransomware when employees fall for social engineering attacks?
KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.
Here's how RanSim works:
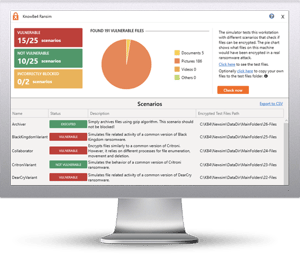 ✔ 100% harmless simulation of a real ransomware infection ✔ 100% harmless simulation of a real ransomware infection
✔ Does not use any of your own files
✔ Tests 10 types of infection scenarios
✔ Just download the install and run it
✔ Results in a few minutes!
Download your complimentary RanSim now:
https://info.knowbe4.com/ransomware-simulator-tool-1chn
|
| Don’t Miss The December Live Demo: New-School Security Awareness Training |
|
Today, your employees are frequently exposed to sophisticated phishing and ransomware attacks. Old-school security awareness training doesn’t hack it anymore. More than ever, your users are the weak link in your network security.
Join us on Wednesday, December 7, 2016, at 2:00 p.m. (EST) for a 30-minute live product demonstration of the innovative Kevin Mitnick Security Awareness Training Platform to see the latest features and how easy it is to train and phish your users:
- NEW Active Directory Integration allows you to easily upload and manage users.
- NEW Send Simulated Phishing tests to your users during specified business hours and drive down the Phish-prone percentage of employees.
- Roll out Training Campaigns for all users (or groups) with follow-up emails to “nudge” users who are incomplete on the training.
- Advanced Features: EZXploit™ an internal, fully automated "human pentest”. USB Drive Test™ to test reactions to unknown USBs.
- Reporting to watch your Phish-prone percentage drop, with great ROI.
- Find out how thousands of organizations have mobilized their end-users as their first line of defense.
Register Now: https://attendee.gotowebinar.com/register/1297472477949589251
|
| Kaspersky: DDoS Often Smokescreen For Phishing Attack |
|
Distributed denial of service attacks, also known as DDoS, are becoming a major threat. They can bring websites and networks down, and generally make a lot of noise demanding attention.
And according to a new Kaspersky Lab report, that is exactly what hackers are using them for.
The strategy goes that as businesses are preoccupied with handling DDoS attacks, cybercriminals and hackers can use the opportunity for another, more targeted type of attack — like spear phishing, happens in the background. The conclusion comes in Kaspersky Lab’s report, which polled businesses about their cybersecurity experiences.
More than half (56 percent) say DDoS is being used to cover something else.
As Kirill Ilganaev, head of Kaspersky DDoS Protection, put it:
“DDoS prevents a company from continuing its normal activities by putting either public or internal services on hold. This is a real problem to businesses and it is often ‘all hands on deck’ in the IT team to try and fix the problem quickly so the business can carry on as before. DDoS can therefore be used not only as an easy way to stop the activity of a company, but also as a decoy to distract IT staff from another intrusion taking place through other channels.” Getting back to the report, it surveyed businesses about their cybersecurity experiences. 29% of the attacks, DDoS was only used as part of tactics. Another quarter of the companies surveyed, 26%, said that when they lost data due to a targeted attack, they were also hit by DDoS.
The usual tactics include social engineering employees through their mobile devices, phishing scams, or even malicious activity from insiders.
Ilganaev continued: “The research shows us that DDoS attacks are often aligned with other threats. Businesses therefore need to be aware of the full threat landscape and prepared to deal with multiple types of criminal activity at any one time,” “Failure to do this could increase the collateral damage, on top of already significant losses caused by downtime and the resulting impact on reputation. Businesses need to use a reliable DDoS protection service to reduce the risk of DDoS and help staff concentrate their efforts on protecting the business from any threats that can be hidden as a result.”
What to do about it:
The moment your organization is on the receiving end of a DDoS attack, start watching your back like a hawk. We recommend to immediately kick off a security awareness training campaign to keep your users on their toes with security top of mind.
|
| Phishing Attack Hits Saudi Govt Networks With Disk-Wiping Malware |
|
Hackers penetrated six Saudi Arabian government agencies including its General Authority of Civil Aviation, and bricked thousands of computers with the well-known Shamoon disk-wiper malware. Saudi's Central Bank denies it was hit despite earlier reports that it was one of the victims.
Bloomberg reports that an investigation into the breach, which is still in its early stages, is currently underway, citing two anonymous sources briefed on the investigation and pointed at Iran as the likely culprit. This attack is very similar to the 2012 incident that destroyed 35,000 machines at the Saudi state oil company Saudi Aramco. The malware was installed using passwords that appear to have been accessed through spear-phishing emails.
"The attackers appear to have done a significant amount of preparatory work for the operation," the Symantec Security Response team wrote on its blog. "The malware was configured with passwords that appear to have been stolen from the targeted organizations and were likely used to allow the threat to spread across a targeted organization's network."
Multiple security firms noted that the malware triggered the disk-wiping to commence at 8:45PM local time on Thursday (17 November), which is the end of the Saudi business week, in order to avoid discovery and inflict maximum damage. "Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice," the blog read.
Hackers penetrated six Saudi Arabian government agencies including its General Authority of Civil Aviation, and bricked thousands of computers with the well-known Shamoon disk-wiper malware. Saudi's Central Bank denies it was hit despite earlier reports that it was one of the victims.
Bloomberg reports that an investigation into the breach, which is still in its early stages, is currently underway, citing two anonymous sources briefed on the investigation and pointed at Iran as the likely culprit. This attack is very similar to the 2012 incident that destroyed 35,000 machines at the Saudi state oil company Saudi Aramco. The malware was installed using passwords that appear to have been accessed through spear-phishing emails.
"The attackers appear to have done a significant amount of preparatory work for the operation," the Symantec Security Response team wrote on its blog. "The malware was configured with passwords that appear to have been stolen from the targeted organizations and were likely used to allow the threat to spread across a targeted organization's network."
Multiple security firms noted that the malware triggered the disk-wiping to commence at 8:45PM local time on Thursday (17 November), which is the end of the Saudi business week, in order to avoid discovery and inflict maximum damage. "Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice," the blog read.
MotiveHackers penetrated six Saudi Arabian government agencies including its General Authority of Civil Aviation, and bricked thousands of computers with the well-known Shamoon disk-wiper malware. Saudi's Central Bank denies it was hit despite earlier reports that it was one of the victims.
Bloomberg reports that an investigation into the breach, which is still in its early stages, is currently underway, citing two anonymous sources briefed on the investigation and pointed at Iran as the likely culprit. This attack is very similar to the 2012 incident that destroyed 35,000 machines at the Saudi state oil company Saudi Aramco. The malware was installed using passwords that appear to have been accessed through spear-phishing emails.
"The attackers appear to have done a significant amount of preparatory work for the operation," the Symantec Security Response team wrote on its blog. "The malware was configured with passwords that appear to have been stolen from the targeted organizations and were likely used to allow the threat to spread across a targeted organization's network."
Multiple security firms noted that the malware triggered the disk-wiping to commence at 8:45PM local time on Thursday (17 November), which is the end of the Saudi business week, in order to avoid discovery and inflict maximum damage. "Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice," the blog read.
Motive
Crowdstrike Co-founder and CTO Dmitri Alperovitch speculated that the current geopolitical situation may have sparked the recent Shamoon attacks. He said in a blog: "While the precise motives in this most recent November incident are currently unclear, the attacks coincide with multiple geopolitical events impacting the Gulf countries, as well as recent industry developments within Saudi Arabia itself." It's well known that Saudi Arabia and Iran are not the best of friends.
Alperovitch continued: "This new variant of Shamoon kept many of its original tactics, down to the commercial raw disk ElDos driver that was used for disk wiping (including the original trial license key for this driver) that had been used in the original attacks. That ElDos trial key was only valid for 30 days and expired by September 2012. In order to continue to use the key, the wiper now has to reset the Windows system clock back to August 2012 to manipulate the license validation process."
How it happened
According to Symantec, the new variant of Shamoon shares several similarities with the original strain. Like its predecessor, Shamoon 2.0 also uses stolen administrative credentials to gain entry and attempts to spread across other devices in the network. According to Palo Alto security researchers, this technique "suggests that the threat actors had previous access to the network or carried out successful phishing attacks prior to the attack".
What to do about It
It looks clear that higher-quality intrusion detection software should have been used, and that employees should have been stepped through awareness training to identify phishing red flags. There are other steps that can and should be taken as well, but these two are obvious and have fast ROI.
Bad guys generally get into their targets with spear-phishing attacks to get credentials so they can penetrate the target network. New-school security awareness training is an effective way to block those attacks.
Get a quote and be pleasantly surprised how affordable this is for your organization. Let us know how many users you have and we'll get you a quote:
https://info.knowbe4.com/kmsat_get_a_quote_now-chn
|
|
|
|