Taking advantage of IMAP functionality a new tool now available on the dark web empowers cybercriminals to circumvent mail scanners, virtual sandboxes, and other security solutions.
It’s every phishers dream and should be your nightmare: a means to bypass all that security software designed to weed out malicious emails, attachments and links. Well, it’s here. According to security analysts at Gemini Advisory, the tool known as “Email Appender” has hit the market on the dark web.
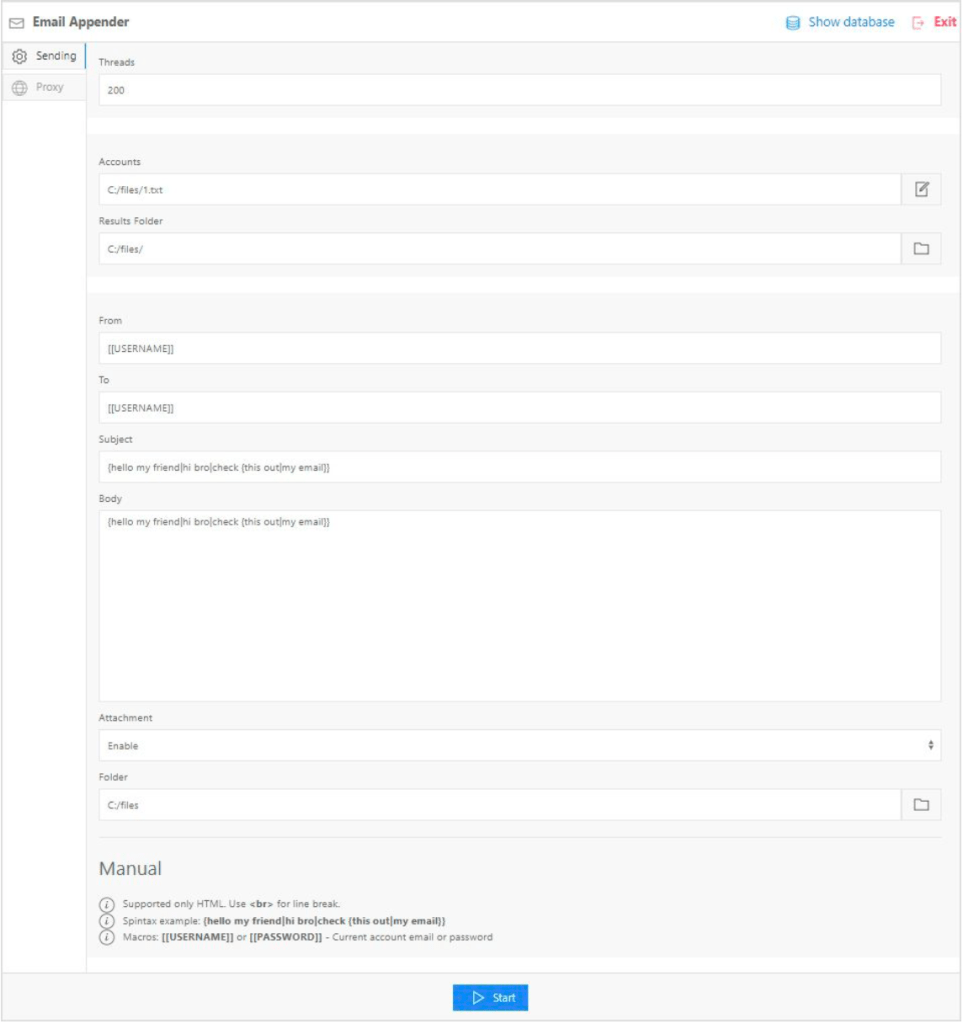
This tool gives any cybercriminal with a set of email account credentials an ability to implant a malicious email directly into the Inbox of that victim’s mailbox. By using an IMAP connection (which is normally used to retrieve email), Email Appender uses allowed functionality to append a message to the victim’s Inbox.
In other words, that malicious phishing email you don’t want getting to the user’s Inbox is placed there directly with no alarms sounding, lights flashing, or other warning that it’s malicious. Able to set the Sender address, email contents, and include attachments, Email Appender is the next big thing (until someone makes an IMAP security solution).
Source: Gemini Advisors
There is a silver lining here; to make this work, the attacker does need the victim’s email credentials. So as long as users are vigilant about phishing scams designed to fool them into logging onto a fake Office 365 website (or equivalent), this attack has no ability to succeed.
Organizations that employ Security Awareness Training educate their users about the dangers of phishing attacks, the types of attacks to watch out for, and why it’s important for the user to play a role in the organization’s cybersecurity stance.
 Here's how it works:
Here's how it works:




