 Because of ransomware attacks, I have been covering the cybersecurity insurance industry for a few years, including here. I even have a whole chapter dedicated to cybersecurity insurance in my forthcoming Wiley book, “The Ransomware Protection Playbook”.
Because of ransomware attacks, I have been covering the cybersecurity insurance industry for a few years, including here. I even have a whole chapter dedicated to cybersecurity insurance in my forthcoming Wiley book, “The Ransomware Protection Playbook”.
The damage caused by ransomware gangs has increased so much over the last two years that average cybersecurity insurance policy coverage amounts are plummeting, premiums are rising (doubling in many cases), deductibles are increasing, and exclusionary policy “outs” are increasing. It is a moment of reckoning for both potential victims and the cybersecurity insurance industry. Insurance brokers are also responding by requiring better computer security from a customer before they can even get insurance. Usually that means that they pass a vulnerability scan and prove to have at least average cybersecurity hygiene to even begin to think about getting a policy.
The cybersecurity insurance industry, and many other guides and regulatory agencies, seem to think that requiring the use of multi-factor authentication (MFA) is the ultimate answer to everyone’s concerns. And it is not!
Last week, I was watching a great speaker from one of the world’s biggest insurance companies, talking about ransomware, discuss how using MFA would prevent 99% of attacks. It is not true. It will never be true.
The 99% figure pops up all over the place. Just use MFA and you will never need to worry about hackers or malware, they claim. You will have a very hard time getting cybersecurity insurance without proving you use MFA. It is the binary litmus test. You either use MFA or you do not. You want cybersecurity insurance, then get MFA. MFA is being sold as the Holy Grail of computer security. And it is not.
I even wrote a book on the subject, “Hacking Multifactor Authentication”. You do not need to buy the book because KnowBe4 offers a ton of free content that we created about the same subject, including these:
- Many Ways to Hack MFA webinar
- 12 Ways to Hack 2FA eBook
- Multifactor Authentication Security Assessment tool
If you do not have time for even those, let me give you the very shortened Cliffs Notes version:
- MFA is good, it significantly reduces the risk of many types of popular attacks
- Use MFA where you can, but you will not be able to use it to protect most things
- A very sizable portion of hacking either does not care about your MFA solution or can hack around it, sometimes easily so
- If you deploy or use MFA, make sure to educate yourself about what attacks can still bypass or ignore your type of MFA solution
- If MFA is used by 100% of people, hacking and malware will still be highly successful
There is a huge difference between saying that MFA significantly reduces the risk of many types of hacking and malware and saying you do not need to worry about hackers and malware!
Or let me put it this way. I spent much of my 34-year computer security career helping companies get significantly more secure. A lot of that effort was spent helping to deploy advanced computer security systems and a lot of MFA. And every company that deployed MFA was just as likely to be successfully exploited after they deploy MFA as before. How? Usually, social engineering and unpatched software.
This conclusion was the majority of the reason I left Microsoft and decided to go to work for KnowBe4. KnowBe4 is tackling the biggest risk to any environment – social engineering. I wanted to help people focus on and fight the biggest cybersecurity risk they have. I have dedicated the rest of my life to doing the same.
The Mistaken Assumption
I know where the people and organizations who are spreading the message that MFA will defeat 99% of hacking and malware are getting their source data. They are reading some quote from a big vendor, like Microsoft or Google, which states that MFA significantly reduced risk of some sorts of attacks (see an example here) and missing or ignoring that it discusses a single type of attack. That is big. That is important.
It is like saying all car accident injuries can be avoid by wearing a seat belt. Yes, seat belts significantly reduce death and injuries, but seat belts alone do not stop all car accident deaths and injuries. If it did, we would not need all the other auto safety systems, traffic lights and speed limits.
How Do I Know MFA Will Not Stop All Hackers and Malware?
Well, for one, every organization I know that has implemented MFA in a widespread way still gets hacked. That is all you need to know right there. I do not know of a single organization that was hacked without MFA, that then went to MFA, and now is not hacked. Maybe there is one out there, but I have never heard of it – it would be a rare unicorn.
Second, if you look at the reported root causes of ransomware exploitation, as I covered in my recent white paper, and shown below, social engineering is the number one cause of ransomware, followed by either unpatched software, Remote Desktop Protocol (RDP)-involved hacks or password attacks.
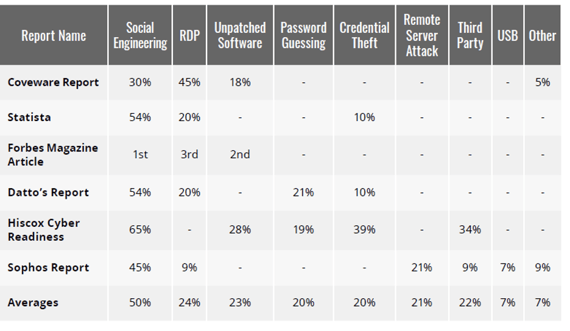
What compromises the RDP attacks is hard to define. I believe, depending on the surveyor, that RDP attacks include attacks against unpatched and insecure RDP and also password guessing. They also likely include the attackers who already knew a valid login credential and just logged in without guessing once. Social engineering may involve password attacks, but because password attacks are well covered in two to three other categories, I think it is mostly covering social engineered trojan horse program attacks, which do not care if you use MFA or not.
If you throw the social engineering category in with any of the ones likely not to be related to passwords (i.e., unpatched software, remote server attack, third party, USB and Other), you get a pretty huge majority of attacks. Just social engineering alone is the biggest threat.
Why are cybersecurity insurance companies not requiring social engineering security awareness training as the best mitigation to prevent ransomware and hacking? Or security awareness training and patching? If I was going on risk analysis alone, I would get far bigger bang for my buck by requiring defenders to mitigate social engineering and better patching than anything else.
The Problem
The problem I see is many groups, who have recently deployed MFA, thinking that they are now significantly less likely to be compromised by hackers and malware. And that is just not true. I or any other hacker can send a normal-looking, routine, run-of-the-mill, phishing email and get past 90% of MFA solutions like they were not even there. Here is an example.
Do you think the organizations that spent all that time and money deploying MFA were told that? Probably not. And if it is not that type of hack, it is something else. I can hack any MFA solution at least a few different ways. I can hack most 10 different ways and I am not even that good of a hacker. If you want to know how I could hack your favorite MFA solution, consider taking KnowBe4’s Multi-factor Authentication Security Assessment tool. Essentially, that tool asks you enough questions to figure out what type of MFA you are using (12 to 20 questions usually) and tells you all the ways I could hack it. I helped create that tool when I only knew of 18 ways to hack MFA (not yet up to my current level of 50+ ways to hack MFA). But you will get the general idea.
Let me repeat the problem. All MFA solutions can be hacked. Most organizations deploying MFA can be hacked. Most organizations that deploy MFA are still at high risk of being successfully compromised by hackers and malware. MFA decreased some of that risk…a big portion of it, but you still have huge gaps to worry about.
The Solution
So, what is the solution? What can users do to mitigate the risks of today’s threats. Clearly, the three biggest things they can do are:
- Mitigate social engineering
- Perfect patching of high-risk apps
- Use MFA where you can to protect valuable data and use good password policies everywhere else (see here)
You should use your best layered, defense-in-depth, combination of policies, technical defenses and education, to do those three things. Nothing else matters nearly as much. And telling anyone to focus on just one thing to the exclusion of others is probably not the right advice. You are just leading them from one false hope to another false hope.
The cybersecurity industry seems to be buying MFA as a risk panacea. That is their prerogative. But they just got through a nightmarish two years of hemorrhaging losses by underestimating risks. Now they have mistakenly bought into this idea that MFA along with a vulnerability scan is the deciding factor. They should just do a single simulated phishing test as well to see what the real remaining risk is. You will not find a single cybersecurity report or survey that does not show social engineering as the number one problem. And if it is, should that not be at the top of the worry list? Should that not be tested in the assurance process as well? It does not have to be first or the only, but should it not be part of the process?
I think there is a good argument, based on data, to say that mitigating social engineering is the single best defense any organization could implement, along with better patching and using MFA.






