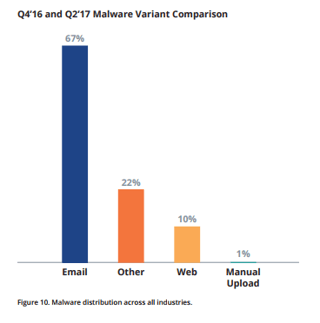
 Cyber-attacks were up by a quarter in Q2 2017, with a surprising twist: global manufacturing is now the top target. The report from NTT Security also shows that phishing is the most popular threat vector, two-thirds (67%) of attacks came in the form of just such a threat.
Cyber-attacks were up by a quarter in Q2 2017, with a surprising twist: global manufacturing is now the top target. The report from NTT Security also shows that phishing is the most popular threat vector, two-thirds (67%) of attacks came in the form of just such a threat.NTT is a very large global managed security provider, and they came out with a PDF showing there was a 24% increase in attacks on its worldwide customer base in the period of April to June, with a third (34%) of all attacks targeting manufacturers: Global Threat Intelligence Center (GTIC) Quarterly Threat Intelligence Report.
This data actually gets confirmed by Verizon, who claimed in their recent Data Breach Investigations Report 2017 that phishing attacks were way up from the previous reporting period. The tactic of embedding malicious VBA macros into documents sent via phishing emails was particularly popular.
Here are a few NTT highlights:
- In terms of attack types, 'reconnaissance' (33%) dominated the manufacturing threat landscape in the period, followed by brute-force attacks (22%) and regular malware (9%).
- Public-facing Microsoft SQL (MSSQL) servers were popular targets for brute-forcing.
- Over a third (37%) of manufacturers claimed they don’t have an incident response plan in place. OUCH
“The motivations for these attacks are often criminal in nature, including extortion via ransomware, industrial espionage, and theft of data such as account numbers,” said Jon Heimerl, manager of NTT Security’s Threat Intelligence Communication Team.
“What poses an even greater problem is that when these breaches are successful, yet go undetected, they allow hackers to establish footholds in organizations’ networks where they have free reign to wreak havoc over extended periods.”
“This is very concerning as manufacturers’ IT security liabilities often impacted not just the manufacturing organizations, but suppliers, as well as related industries and consumers,” said Heimerl.




