 Remember the CRYSIS ransomware? The attacks started up again, mostly targeting US healthcare orgs. using brute force attacks via Remote Desktop Protocol (RDP).
Remember the CRYSIS ransomware? The attacks started up again, mostly targeting US healthcare orgs. using brute force attacks via Remote Desktop Protocol (RDP).
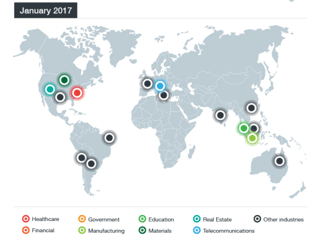
The number of attacks has more than doubled in volume in January 2017 over that same timeframe in 2016. This most recent wave included a wide variety of sectors worldwide, but the U.S. healthcare sector was hit the hardest.
Security researchers at Trend Micro observed that the same cyber mafia that perpetrated the 2016 CRYSIS attacks are behind this recent wave of ransomware attacks, evidenced by the very same file names and malware placement as were used earlier.
The problem: User accounts with weak credentials, open RDP ports
The bad guys try to log in to the system using common username and password combos, and once the system is accessed they return multiple times to quickly compromise the machine. Trend Micro found that these repeated attempts were generally successful in a matter of minutes.
A typical infection goes through the following steps. An attacker picks targets with RDP ports available online and identifies if the computer is assigned to an enterprise network. Alternatively, he can always buy access to previously hacked RDP servers, via marketplaces like xDedic.
Once he purchased or gained access to a computer by brute-forcing the RDP connection with basic username-password combos, the attacker downloads and then manually executes a version of the Crysis ransomware on each of the hacked computers.
In one case it was observed that CRYSIS was deployed six times, packed in different ways on a single endpoint within ten minutes. The attackers copied over several files and appeared to be experimenting with different payloads to find the best option.
Because there are no default restrictions on shared folders of clipboards, unless the network administrator applies controls, these features may be exposed to the internet and accessible by a malicious individual.
What To Do About It:
Best practice to protect a network from a brute force RDP attack is to apply strong RDP security settings, including limiting or disabling access to shared folders and clipboards from remote locations.
An RDP brute force approach opens the attacker’s information to the targeted network, so you should parse the Windows Event Viewer and find the compromised user account and the IP address of the attacker and block that.
Ransomware Hostage Rescue Manual
Get the most complete Ransomware Manual packed with actionable info that you need to have to prevent infections, and what to do when you are hit with ransomware.
If you do not like to click on buttons with redirects, cut/paste this link in your browser:
https://info.knowbe4.com/ransomware-hostage-rescue-manual-0





