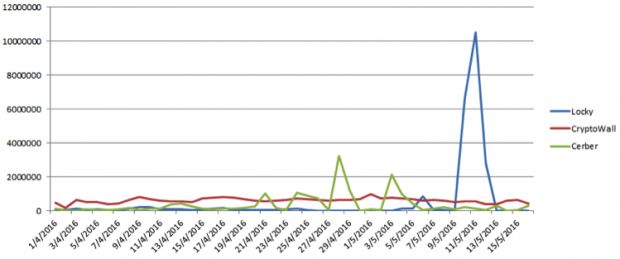
US cyber-security firm Fortinet reports that, between April 1, 2016, and May 15, 2016, the top five most prevalent ransomware families were in this order: CryptoWall (41.04%), Locky (34.36%), Cerber (24.17%), TorrentLocker (0.24%), and TeslaCrypt (0.09%).
TeslaCrypt's disappearance is caused by the fact that its authors decided to throw in the towel and release a master decrypt key that can release any files ever locked with TeslaCrypt.
As you can see in the above activity graph, while CryptoWall is still the most serious threat there have been numerous occasions where Cerber infections surpassed those of CryptoWall.
Unconfirmed rumors among infosec researchers show that TeslaCrypt's authors may have moved on to distributing Cerber instead. If the name sounds familiar, it's because Cerber is the ransomware that speaks to users by reading its ransom note out loud.
According to statistical data, Cerber has been very successful at infecting users in the US and Japan, but it has hit many other countries worldwide as well.
Just to refresh your memory, CryptoWall ransomware is delivered via phishing emails containing malicious PDF files as well as the Nuclear Exploit Kit (NEK). It can run on both 32-bit and 64-bit systems, increasing the likelihood that the virus will run on any machine it infects.
Locky ransomware is delivered via spear phishing emails with Microsoft Word attachments containing malicious macros. Locky targets a large number of file extensions and can even run when a machine is offline.
What these top 3 threats all have in common is that they rely primarily on social engineering and phishing or spear phishing to successfully attack its victims. This is why we tell you all the time to think before you click!
Get the most informative and complete ransomware hostage rescue manual. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.





