 From the Front Lines of Incident Response, the CrowdStrike Services Cyber Intrusion Casebook 2018 offers some compelling stories how threat actors are continuously adopting new means to achieve their objectives. Drawn from real-life client engagements, the annual Casebook provides valuable insights into ever-evolving attacker tactics, techniques and procedures (TTPs).
From the Front Lines of Incident Response, the CrowdStrike Services Cyber Intrusion Casebook 2018 offers some compelling stories how threat actors are continuously adopting new means to achieve their objectives. Drawn from real-life client engagements, the annual Casebook provides valuable insights into ever-evolving attacker tactics, techniques and procedures (TTPs).
ATTACK VECTORS
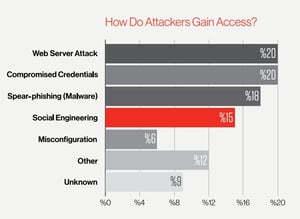
A dramatic increase in the number of attacks leveraging social engineering, phishing and spear phishing, which accounted for one-third of all attacks investigated — up from 11 percent last year. This is due, in no small part, to this year’s rise in BECs, along with the continued popularity of phishing among nation-state actors. Web server attacks, although still the biggest single attack vector at 19.7 percent of all attacks, declined significantly from the 37 percent reported last year.
CrowdStrike recommends what it calls the 1-10-60 rule: Detect an attack on your organization within one minute, take 10 minutes to investigate it, and then remediate it within 60 minutes. "Organizations that can operate at this level will dramatically improve their chances of staying ahead of the adversary and stopping a potential breach from occurring," the company wrote in its case report.
Learn how CrowdStrike Services IR experts detected and stopped sophisticated adversaries and get recommendations that will better protect your organization, PDF:
https://www.crowdstrike.com/resources/reports/cyber-intrusion-services-casebook-2018





