 The FBI’s newly-released report shows just how ransomware continues to plague critical infrastructure sectors, despite the U.S. government’s recent efforts to stop these attacks.
The FBI’s newly-released report shows just how ransomware continues to plague critical infrastructure sectors, despite the U.S. government’s recent efforts to stop these attacks.
You’ll probably recall the news about ransomware attacking the Colonial Pipeline and other U.S. critical infrastructure (CI) to the point that the government was stepping up their efforts to stop these attacks and even conducting congressional hearings on what to do about the problem. The FBI reported that nearly 650 CI businesses were hit in 2021. We’d all like to think that the introduction of the involvement of the U.S. government would spell the end of attacks on such important industry vectors that keep the country going.
But according to the FBI’s latest Internet Crimes Report that covers 2022, the number of CI businesses attacked increased by 34% in 2022, rising to 870.
In short, CI industries have plenty to be worried about. According to the FBI, Lockbit, BlackCat and Hive were the top three ransomware strains used in these attacks, targeting 16 CI sectors (shown below).
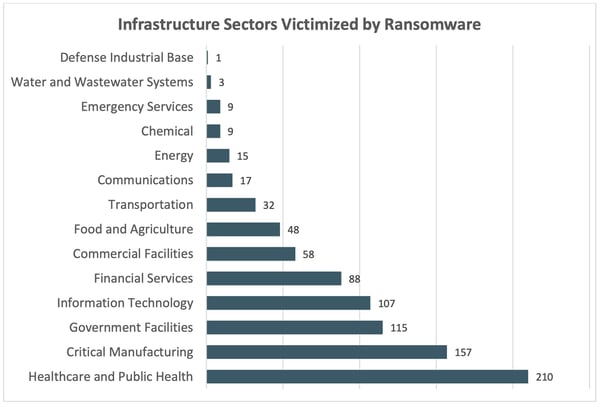
Source: FBI
According to the FBI, 14 of the 16 sectors had at least one attack that was successful, but did not go into detail on how many succumbed to an attack in total.
As an additional layer of security, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) began a pilot program - Ransomware Vulnerability Warning Pilot (RVWP) – which scans CI networks for internet-exposed devices that could be exploited.
In the meantime, CI organizations need to also focus on the number one ransomware initial attack vector – phishing. Users need to undergo continual Security Awareness Training to stifle scams, social engineering and BEC attacks that may be a prelude to a ransomware attack.
 Here's how it works:
Here's how it works:




