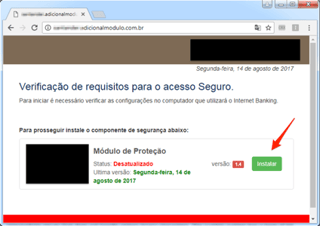
 The attackers did reconnaissance on their targets, using social networks which people inside the organization were involved in making financial transactions. These victims were then called using the old-fashioned phone by the attacker posing as bank employees, who then used social engineering tactics to trick the victim to install an "update" to the bank’s security module.
The attackers did reconnaissance on their targets, using social networks which people inside the organization were involved in making financial transactions. These victims were then called using the old-fashioned phone by the attacker posing as bank employees, who then used social engineering tactics to trick the victim to install an "update" to the bank’s security module.The victims who complied, worried that they would lose access to their account, were installing a Chrome extension called Interface Online offered by Internet Security Online. The extension was available on Tuesday in the store and there were at least 30 downloads. As it was discovered, Google took it down. This scam was first discovered in Brazil, but expect this soon in the US and Europe.
The SANS Internet Storm Center handler Marinho disclosed the scam Tuesday on the ISC site, and commented that the malware has relatively few detections on VirusTotal.
The pressure-filled phone call to the banks includes instructions on how to update the supposed security module. The victim is provided with a web address over the phone and when they click “Install,” they are redirected to the extension’s installation page, hosted in the Chrome Store.
The fraudster keeps the victim on the line throughout the installation process and once it’s complete, has them test their access to the corporate bank account. As they enter their credentials, the data is sent to the attackers in the background. Ironically, a description of the extension explains that it can read and change data on websites the victim visits, and continue to monitor browsing activity on the victim’s version of Chrome.
“I’ve had the opportunity to listen to one of those calls and I must admit that they make it in a professional way,” Marinho told Threatpost.
“In my opinion, the criminals are shifting from the traditional [malicious spam] to targeted and more creative attack methods here in Brazil,” Marinho said. ‘It’s getting common to have victims reporting that they are receiving phone calls from someone pretending to be from a bank and urging the victim to do something, like installing a fake security module, in this case, or asking them to type the token combination on a fake website.”
These attacks are just the latest in a growing trend of fraud exploiting Chrome extensions. In the last two weeks, researchers have reported at least eight popular Chrome plugins had been hijacked and were being abused to manipulate internet traffic and serve ads in the browser.
Warn your accounting team that this is a new scam they need to watch out for. And step them through new-school security awareness training to prevent compromises like this.
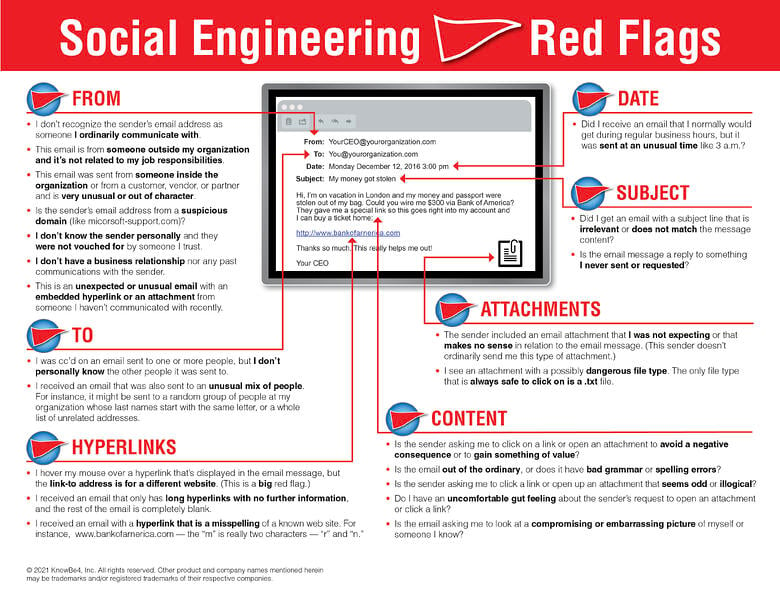
We also suggest that you share this document with your users so they have a constant reminder if social engineering red flags. It's a great resource for them to keep near their computer!