 New data from Palo Alto Network’s Unit42 provides a wealth of insight into specifically how cybercriminals have leveraged COVID-related theming to ensure a successful phishing attack.
New data from Palo Alto Network’s Unit42 provides a wealth of insight into specifically how cybercriminals have leveraged COVID-related theming to ensure a successful phishing attack.
Throughout the last 14 months, the bad guys have consistently kept pace with the state of the pandemic. They have been looking for the best aspects of the COVID saga to get the attention of individuals and businesses alike of these attacks.
According to Unit42’s new COVID-19 themed phishing attack data, these scammers know exactly how to press the buttons of their potential victims at just the right time. For example, the current concern is around vaccines. According to Unit42:
- Vaccine-related phishing attacks rose by 530% from December 2020 to February 2021
- Phishing attacks targeting pharmacies and hospitals rose by 189% during that same timeframe
Over the past 14 months phishing attacks have changed their stripes to meet the current state of the potential victim’s concerns, fears, needs, and hopes – as shown below.
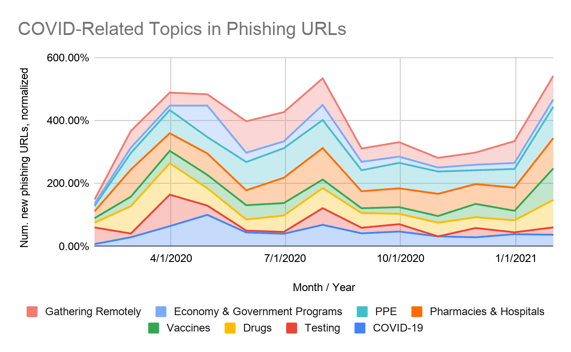
Source: Unit42
The number of new phishing URLs in February of this year reached the same level as approximately August of last year – at the height of some very large COVID case spikes.
Unit42’s data also touches on some interesting points around how these campaigns are being executed:
- Microsoft 365 accounts were the top target, with 23% of COVID phishing URLs impersonating logon pages to steal credentials
- The greatest percentage of websites at time of detection were less than 32 days old
The bad guys know their audience well and they can adapt on how to change up tactics as needed so that you’ll fall for their scam. It’s important to keep your users current with information on the latest scams, themes, and social engineering methods through continual Security Awareness Training. By doing so, no matter how the bad guys change their stripes, your users will see the next COVID-themed phishing attack for what it truly is.
 Here's how it works:
Here's how it works:




