 With ransomware players, sophistication, effectiveness, and cost all on the rise, it may be time for us to take a page from counterterrorism to make it more difficult for cybercriminal gangs.
With ransomware players, sophistication, effectiveness, and cost all on the rise, it may be time for us to take a page from counterterrorism to make it more difficult for cybercriminal gangs.
Ransomware is no longer something that just happens to “other organizations.” With cyber insurance claims up a whopping 422% in the first quarter of this year, payments at an all time high. Some cybercriminal gangs are now acting as VC investors for newer “ransomware startups,” it’s evident that threat actors are stepping on the accelerator pedal and aren’t looking back.
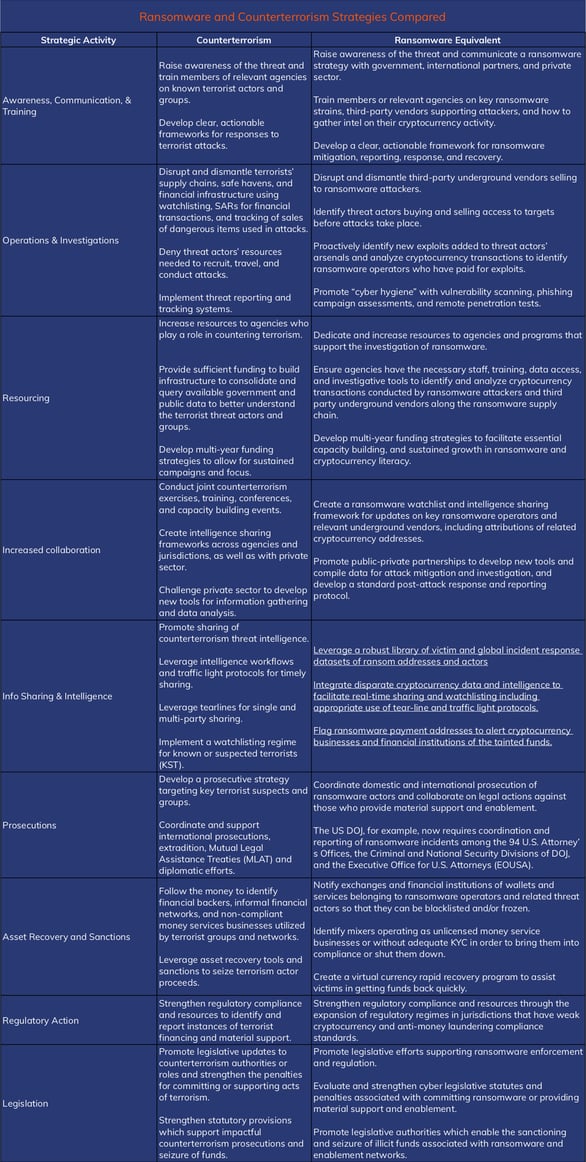
According to a new article by blockchain tech vendor, Chainanalysis, the answer to stopping ransomware could be found by using similar strategies as those utilized in counterterrorism.
In the article, they maintain collaboration is key – between military, law enforcement, intelligence agencies, public-private partnerships, using shared frameworks and watchlists:
If governments and cryptocurrency businesses brought together all of the intelligence they have on who’s carrying out and enabling ransomware attacks, they could put together a robust library of the most prolific operators, affiliates, third-party vendors, and money laundering service providers, along with the cryptocurrency data associated with these persons and entities (e.g., addresses and transaction histories). This combined threat reporting and resulting watchlist of known or suspected ransomware actors would give organizations around the world a shared understanding of who’s driving the most ransomware attacks at any given time, help all parties respond to attacks faster, and support efforts to arrest and sanction the worst offenders.
They also provide a summary of strategies and how they might be used to counter ransomware:
Source: Chainanalysis
I’m glad to see Security Awareness Training at the top of the list – it’s not just a means to educate users so they don’t click a malicious email attachment; it’s also the foundation for establishing a security culture within an organization by stressing the importance of personal cybersecurity hygiene and best practices.
I suspect we’ll begin to see this kind of intelligence sharing come to fruition soon; it’s needed and could be impactful.
 Here's how it works:
Here's how it works:




