 New analysis of ransomware attacks shows growth in the number of active strains, ransoms collected, and use of third-party services all adding up to a more organized and profitable industry.
New analysis of ransomware attacks shows growth in the number of active strains, ransoms collected, and use of third-party services all adding up to a more organized and profitable industry.
It’s one thing to see one metric measuring ransomware up “up and to the right”. But when you start seeing multiple indicators that the ransomware “industry” as a whole is growing, it’s a real problem. New data from Chainalysis’ preview of their 2022 Crypto Crime Report shows some pretty unnerving growth from ransomware gangs.
According to the report:
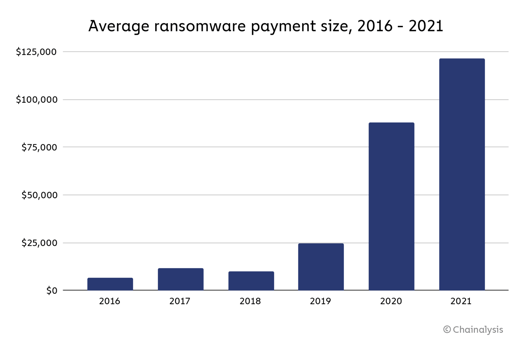
Ransomware payments grew 34% from $88K in 2020 to $118K in 2021
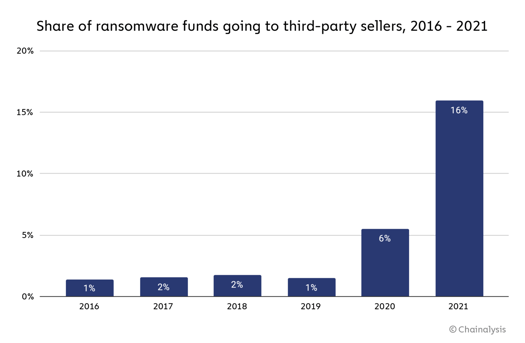
Ransomware threat actors are engaging with third parties to leverage tools and services that increase the chances of successful attack and payment – up 166% from 6% of ransomware funds in 2020 to 16% in 2021.
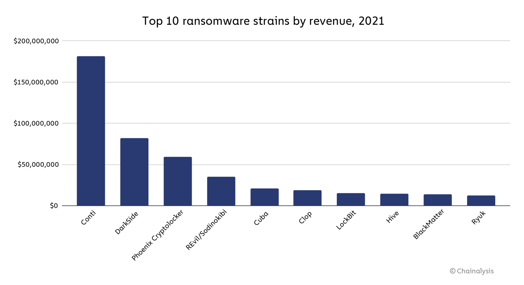
Conti, by far, was the top ransomware strain, seeing success in its ransomware-as-a-service model, taking in $180 million in 2021.
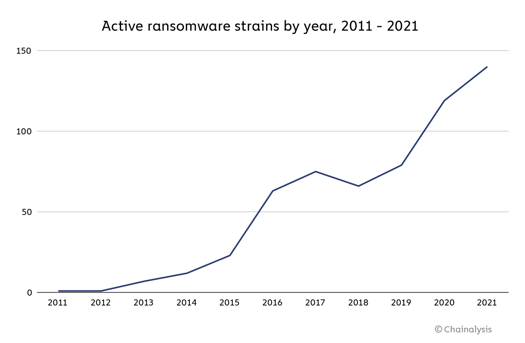
The number of active ransomware strains grew 17%, from 119 in 2020 to “at least” 140 (according to Chainalysis) in 2021.
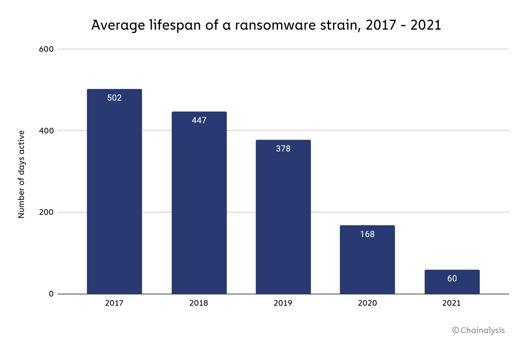
Lastly, it was interesting to see that the average lifespan of a ransomware variant is down to just 60 days, down 64% from 2020’s 168 days.
Put all this together and you quickly realize cybercriminals are getting smarter; leveraging partnerships, best-of-breed tools, constantly changing their malware, and seeing greater results.
Both Conti and Darkside (the second place “contender” according to Chanalysis) use phishing and spear phishing as an initial attack vector – something that can be defeated with a combination of a defense-in-depth approach around malicious email content and Security Awareness Training to employ your users in stopping attacks by not engaging with phishing content in email and on the web.
 Here's how it works:
Here's how it works:




