Anytime there’s a transaction involving money, cybercriminals look for ways to hack in and intercept funds. Student Loans are the latest target.
It’s the Fall semester and an eager young college student is due the balance of their student loan. They’ve inputted their banking information into the university’s system, and the money should show up any day. That is, until the student receives an email that’s all-too-familiar to those of us in the security sector of tech:
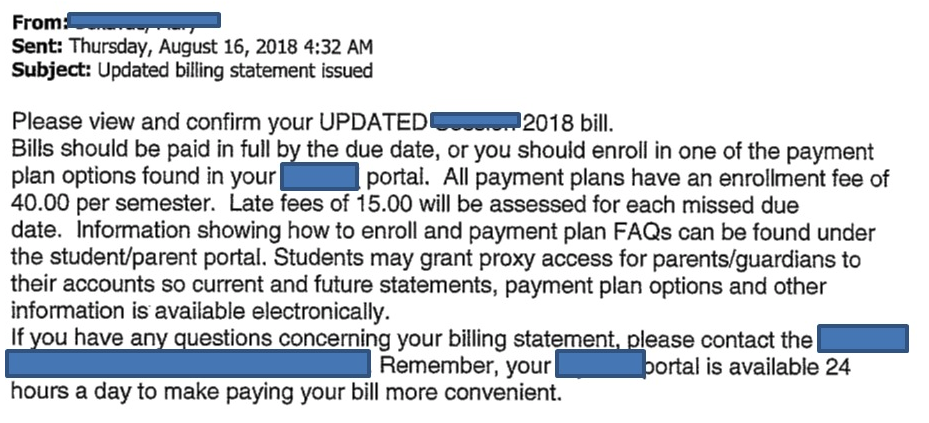
It's a rather convincing-looking email sent to an unsuspecting student. The use of late fees creates a sense of urgency within the student, requiring them to log in and check their bill.
The email links to what appears to be a university student portal – where the student sees their billing, schedule, grades, and more. It’s not. It’s a duplicate set up by cybercriminals. Students “log on”, providing their credentials. Cybercriminals are able to use those credentials to log onto the real portal and alter the banking details for the excess student loan payout to be directed to an account they control.
Some universities have already seen this scam: Florida Gulf Coast and Wellesley College have both reported schemes like these. Some universities are taking measures such as requiring two-factor authentication to gain access, making it difficult for scammers to access student accounts.
This scam demonstrates how cybercriminals are digging into business processes where money changes hands and are finding ways to insert themselves into the process in order to redirect money transfers. We covered this same type of scam impacting the mortgage industry a few months back.
Those parts of your organization’s businesses processes that involve the transacting of money (accounts payable, accounts receivable, sales, an online store, etc.) requires additional levels of security to ensure users don’t become victims of scams designed to give an attacker access to systems controlling any part of those transactions. Providing users with Security Awareness Training is critical in these circumstances, to educate the user on the kinds of social engineering scams they may face, how to identify them, and what to do about it should they encounter one.
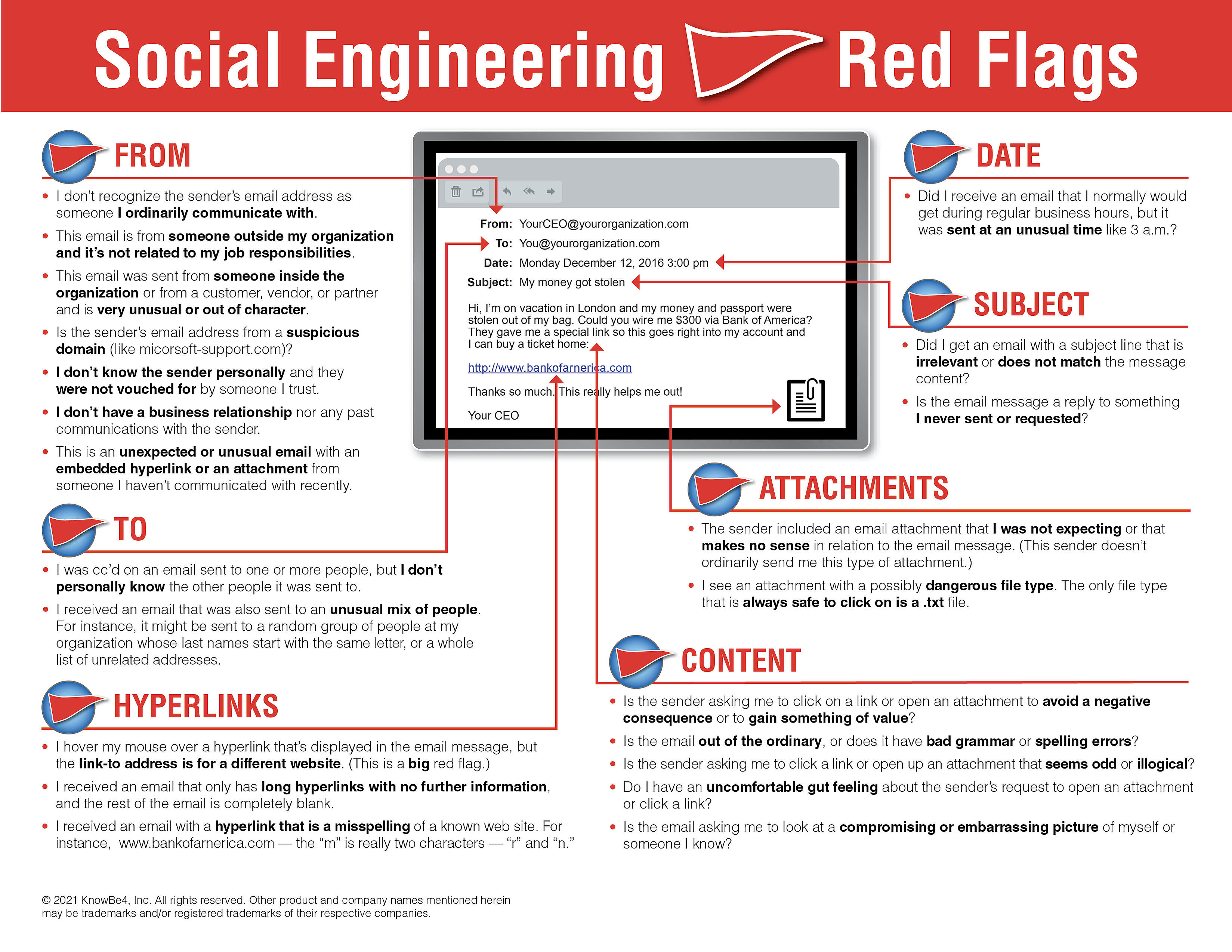
We recommend EVERYONE to review the 22 social engineering red flags to watch out for in any email. It might be a good idea to print out this PDF and pass it along to family, friends, and coworkers. Remember to always think before you click!