 Cleveland Medical Associates is offering about 22,000 patients identity protection services after a ransomware attack against the practice. The practice is offering a year of protective services through Equifax to both current and former patients whose information may have been affected.
Cleveland Medical Associates is offering about 22,000 patients identity protection services after a ransomware attack against the practice. The practice is offering a year of protective services through Equifax to both current and former patients whose information may have been affected.
The breach was discovered the morning of April 17. “We were unable to determine with reasonable certainty whether or not there was an unauthorized access of your information. However, we are providing you with notification of this incident.” they told patients in a notification letter.
Protected health information that could have been compromised includes patient names, addresses, demographics, telephone numbers, email addresses, clinical information, insurance billings and Social Security numbers.
Are Ransomware Infections considered a Data Breach?
Regulators are starting to lean that way, especially in healthcare. HIPAA violations include unauthorized access to protected health information and the case is argued that a ransomware infection qualifies as such. This issue is making its way through both the courts and regulatve process and I expect sooner rather than later that a consensus will be reached that an infection does indeed constitute a data breach and should result in a breach notification.
The Two Steps How To Prevent This
Based on the most recent compilation of HIPAA audits done by the Office for Civil Rights (ORC), an organization within the U.S. Department of Health & Human Services, OCR found that lack of privacy and security awareness training led to the highest number of audit findings. Not having formal policies and procedures in place for protection of PHI as well as general lack of understanding of HIPAA requirements were the next most common occurrences of findings.
One: Not having proper security awareness training can lead to an untrained user clicking a link within an email and causing a ransomware infection. Breaches lead to increased audit scrutiny and without an understanding of the HIPAA requirements and incomplete policies there could be fine increases. Step all users through short, interactive training modules and then test them with frequent simulated phishing attacks.
Two: The KnowBe4 Compliance Manager (KCM) can help with understanding what requirements need to be satisfied and gives you a platform for being able to demonstrate compliance with those requirements. KCM helps you to get compliant and more importantly stay compliant year-round. Does this compliance curve look familiar? 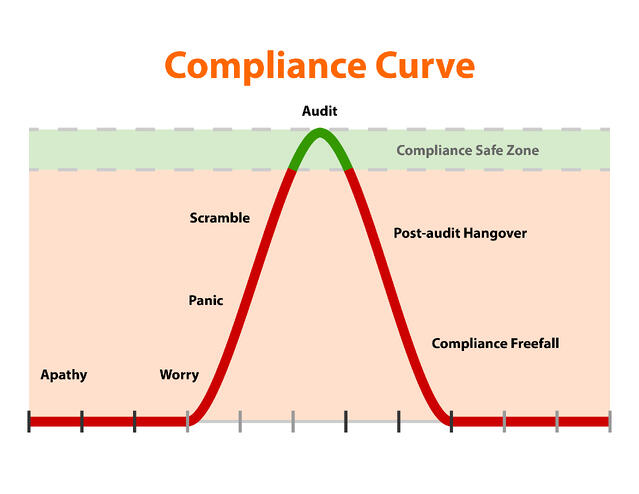
Available as a Trial Account
You can test KCM for yourself using one of the KnowBe4 pre-built compliance requirements templates listed below. Request a demo and get a walkthrough of KCM to get started.
Available Compliance Requirements Templates
The following are a list of the currently available pre-build compliance requirements templates offered for KCM. If a regulation you need is not listed below you can simply build your own using our custom templates feature.
- PCI-DSS
- HIPAA
- ISO 27001
- NIST SP800-53
- NIST Cyber Security Framework
- FFIEC Cybersecurity Assessment Tool
- CIS Critical Security Controls
- COSO Fundamentals
- ACCSC Accreditation
- NIST SP800-171 Protecting Controlled Unclassified Information
- SEC OCIE Cybersecurity Examination Initiative
- AICPA SSAE16 SOC 2 Trust Services Principles with Privacy
- Cloud Security Alliance - Cloud Controls Matrix 3
- New York State - Department of Financial Services - 23 NYCCR 500 Cybersecurity Requirements
- FDA 21 CFR Part 11 Requirements for Electronic Records




